Trusted proxy for DLM
In the existing scenario, communication between DLP App and DLM Engine is through the Knox, using SSO cookie.
Knox routes all the requests to cluster services like Ambari, Beacon, Ranger, Atlas, and others. Each of these services must enable Knox SSO and later setup Knox certificates on each of the requested services, which could be cumbersome and prone to errors. User has to go through Knox SSOs to access any services.
Additionally, when DLM Engine communicates with Source and Target clusters, the Knox SSO cookie is generated using beacon-preauth.xml file. Later, the service request calls are routed through Knox. Again, the cluster services have to enable the Knox SSO, which could be cumbersome and possibly end up being prone to errors.
New Trusted Proxy
In the new trusted proxy set up, the communication between DLM App and DLM Engine goes through Knox, and the authentication at DLM Engine will be handled using Kerberos. The DLM App to Knox authentication will still be using SSO. Use the recommended HDP stack versions and also install Knox certificate on the DLM Engine service.
HDP stack for Trusted Proxy
Before setting up the new Trusted Proxy for DLM, make a note of the supported stack details.
 | Caution |
|---|---|
As of DLM 1.5.1 release, trusted proxy
feature is certified to function only on HDP 2.6.5 to
2.6.5 clusters. |
- HDP release - 2.6.5.1175
- Ambari - 2.6.2.33-3
- Dataplane - 1.2.2 and 1.2.3
- DLM - 1.5.1
Install Knox certificates
Follow these instructions to download and install Knox certificates on your DLM Engine service:
-
Before pairing two secured clusters, for example, Cluster0 and Cluster1, ensure that Beacon is running on Cluster0 on Beacon0 host and Cluster1 on Beacon1 host.
-
Knox is running on Cluster0 on Knox0 host and on Cluster1 on Knox1 host.
- Later, run the following commands on Beacon0 host:
openssl s_client -connect <knox0>:8443 <<<‘’ | openssl x509 -out /tmp/knox0.crtkeytool -import -trustcacerts -keystore <java cacert path> -storepass <storepass> -noprompt -alias <alias> -file /tmp/knox0.crtFor example:
keytool -import -trustcacerts -keystore /usr/lib/jvm/java-openjdk/jre/lib/security/cacerts -storepass changeit -noprompt -alias knox0 -file /tmp/knox0.crtopenssl s_client -connect <knox1>:8443 <<<‘’ | openssl x509 -out /tmp/knox1.crtkeytool -import -trustcacerts -keystore <java cacert path> -storepass <storepass> -noprompt -alias <alias> -file /tmp/knox1.crt- Restart Beacon0 using Ambari.
- Repeat the above steps for Beacon1 host as well.
As a prerequisite for this set up to work, the clusters must be kerberized.
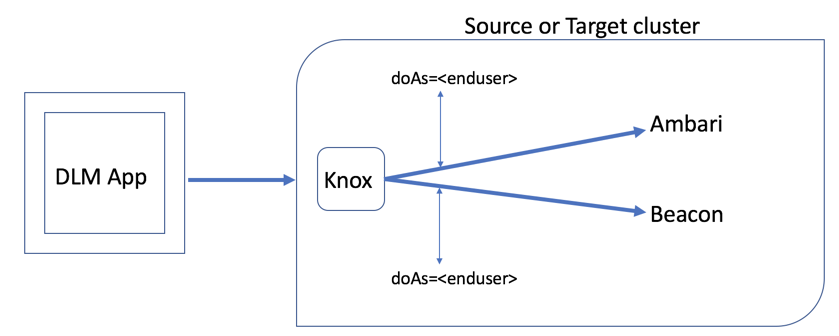
When a call is made from DLM App to DLM Engine, the trusted proxy flow takes place in the following manner:
-
Knox authenticates the incoming request using SSO.
-
Knox initiates a new request to service using ‘Knox’ keytab with
doas=<enduser> -
The service authenticates the requesting user as ‘knox’, but uses enduser UGI.
-
Only ‘Knox’ can set doas parameter. Any extra validation for the doAs user will be done in services.
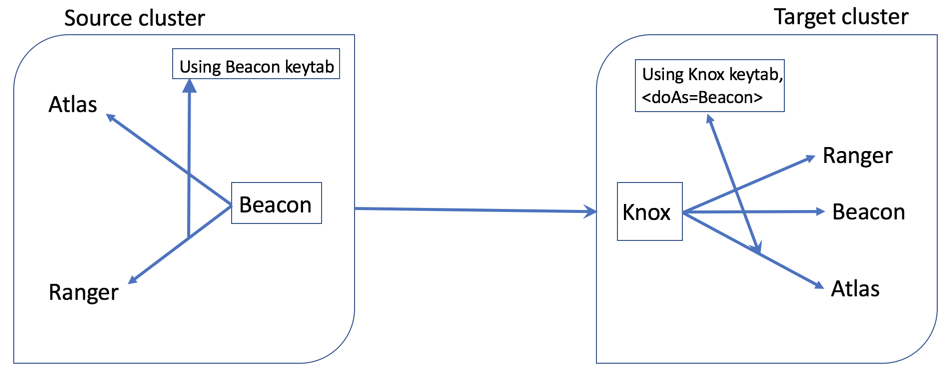
Again, in the new trusted proxy environment, DLM Engine to remote cluster service communication happens as follows:
-
Knox authenticates the incoming request using Kerberos.
-
Knox initiates a new request to service using ‘Knox’ keytab with
doas=<enduser> -
The service authenticates the requesting user as ‘knox’, but uses enduser UGI.
-
Only ‘Knox’ can set doas parameter. Any extra validation for the doAs user will be done in services.
Use the following information to set up the new trusted proxy for DLM:
-
Supported stack versions: Ambari (2.6.2), HDP (2.6.5), and DataPlane Platform (1.2.2 and 1.2.3)
-
Install Knox. Don’t enable SSO and Knox proxy
-
Enable Kerberos for Ambari service
- Download the script: DP cluster setup utility
-
Run sudo python
dp-cluster-setup-utility.pyutility from the Knox host
 | Note |
|---|---|
If you are using HDP 2.6.5 cluster, you must run ambari-server
setup-trusted-proxy before running the above script. |
-
Provide all in-prompt inputs
-
Adds trusted proxy configurations to Ambari, Ranger, Atlas, and DLM Engine
-
Creates Knox topologies -
token,dp-proxy, andbeacon-proxy - Registers the cluster with DataPlane platform
-
Import Knox certificates in the DLM Engine service
- Finally, you must restart all the available services with stale configurations on Ambari gateways (both clusters)

