Verify the DLM Engine installation
Ensure that your DLM Engine set up is functional.
- Scan through Ambari logs of DLM Engine service installation for any errors.
-
Run the
/usr/dlm/current/beacon/bin/verify_beacon_knox.shutility script to ensure that Knox SSO is configured successfully with the DLM Engine./usr/dlm/current/beacon/bin/verify_beacon_knox.sh https://<knox_hostname>:8443/gateway/knoxsso/api/v1/websso http://<beacon_hostname>:25968 admin admin -
Verify that DLM Engine was added as a user to the HDFS superuser group.
hdfs groups beaconThe output should display HDFS (or value of the dfs.permissions.superusergroup config) as one of the groups.
-
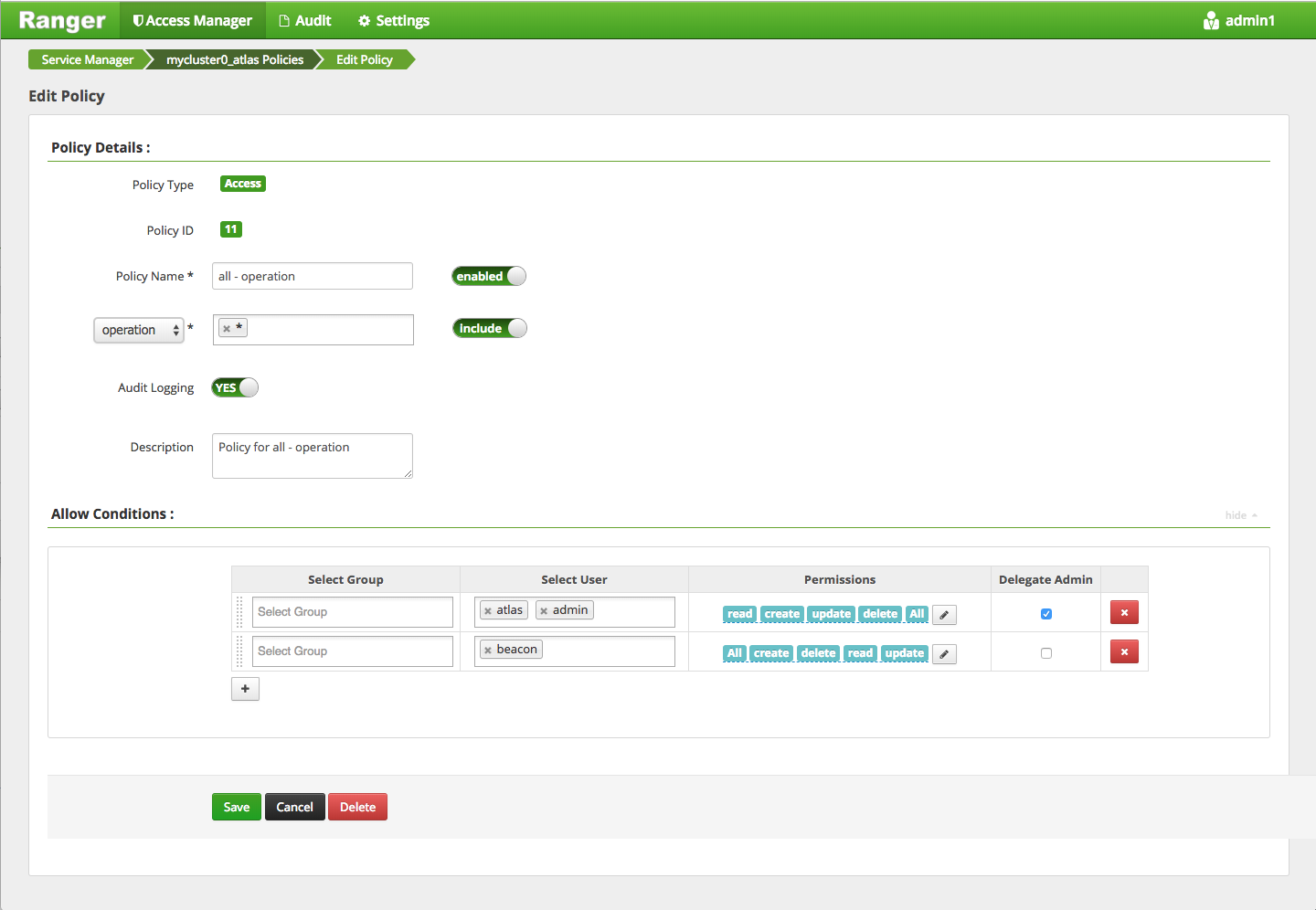
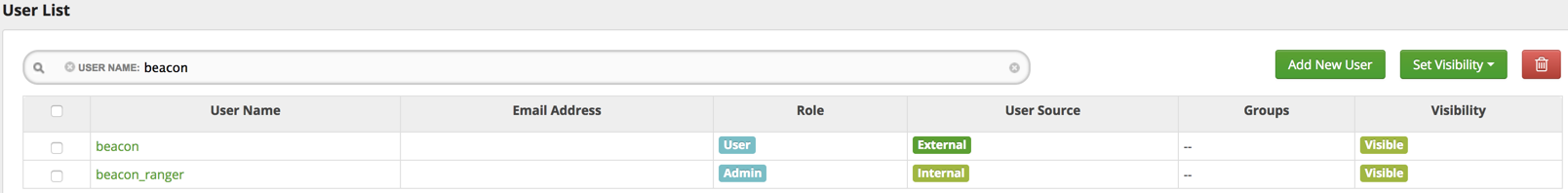
Verify that DLM Engine user is setup as Ranger admin. In secure cluster, this
will be ‘beacon’ user with role ‘Admin. In unsecure cluster, this will be
‘beacon_ranger” user with ‘Admin’ role.
-
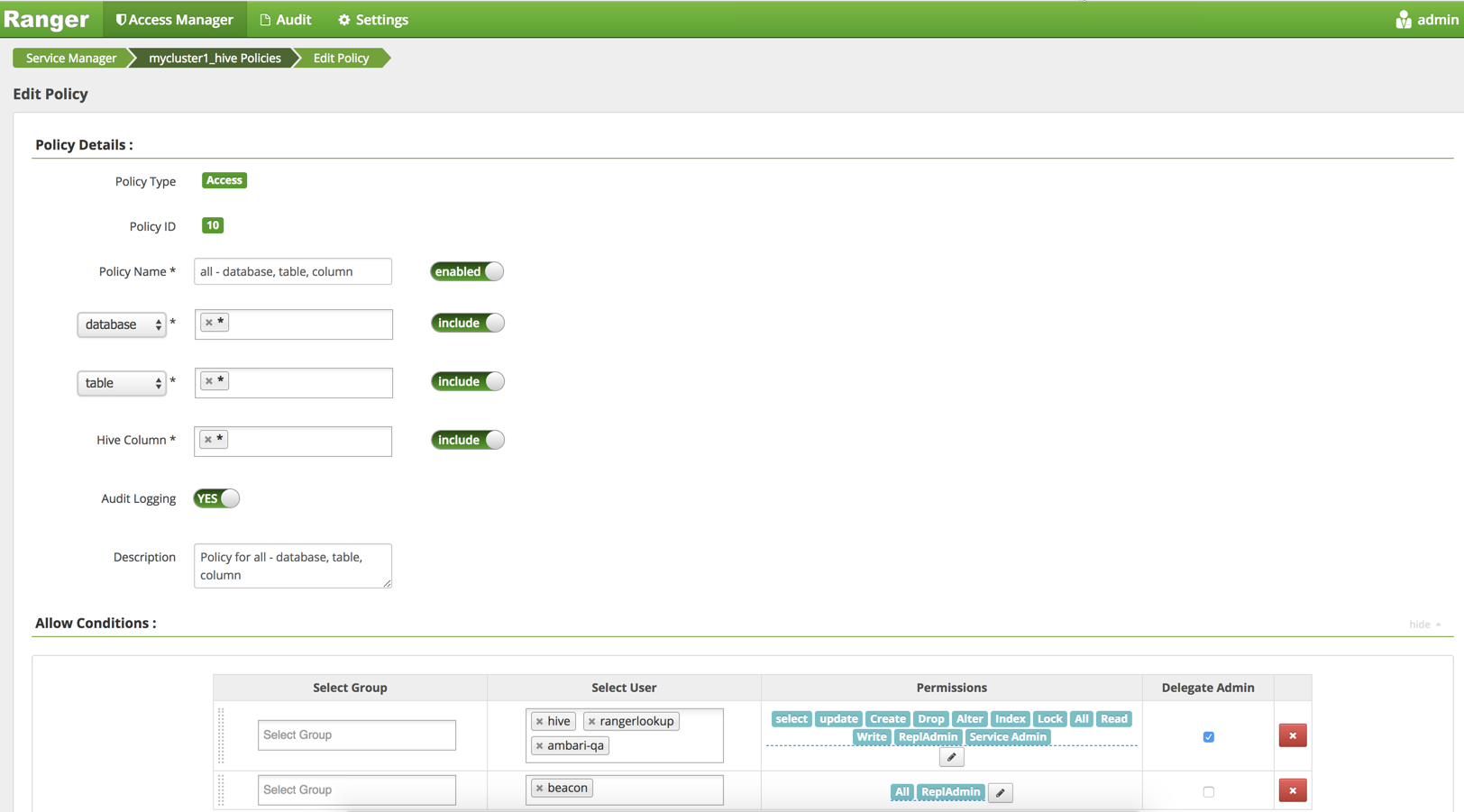
Verify that the ‘DLM Engine’ user has Hive access through Ranger policies.
‘DLM Engine’ user has repladmin privileges
‘DLM Engine’ user has access to all databases, tables, and columns.
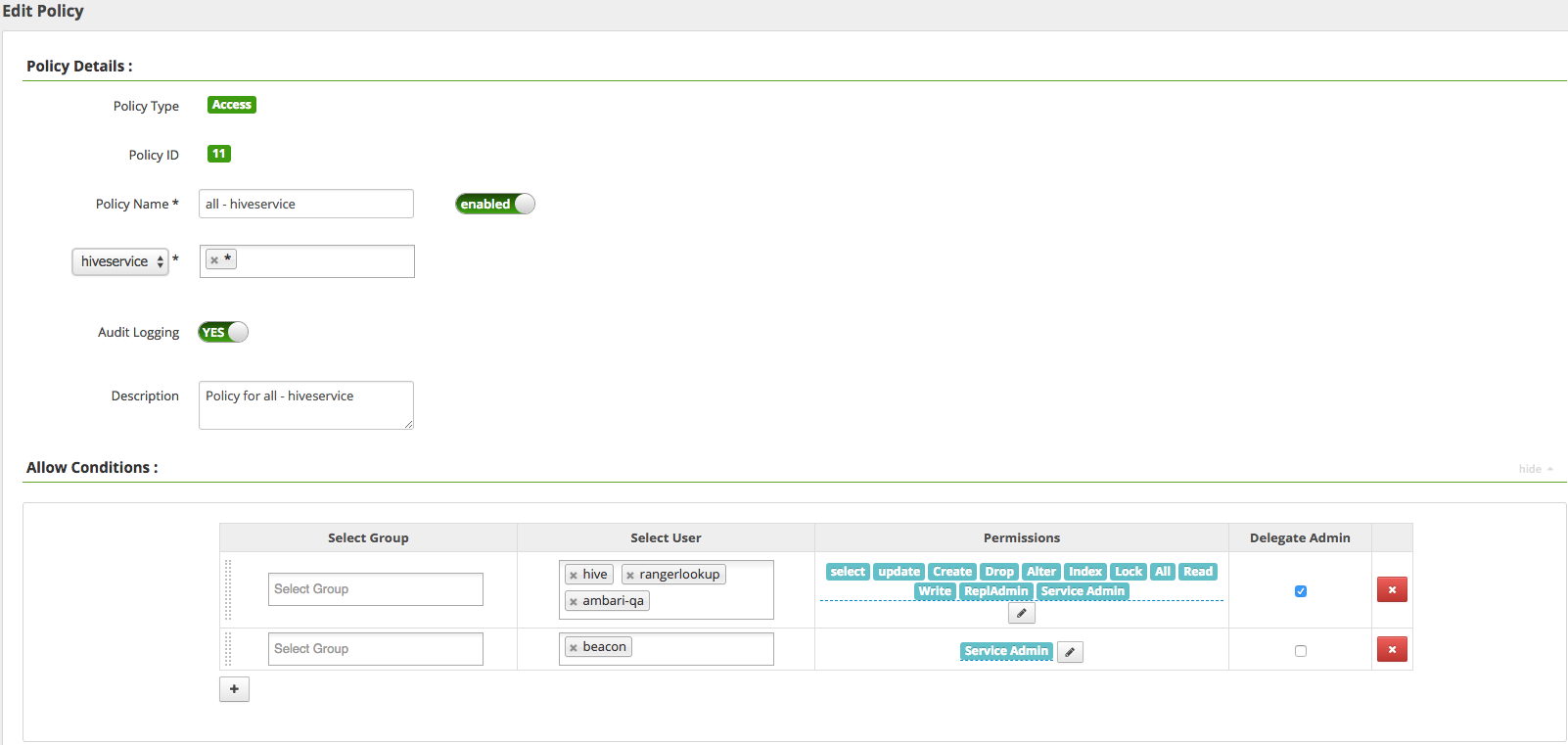
DLM Engine service user requires Service Admin permission to perform Hive replication and related operations. Make sure that DLM Engine service user is assigned Service Admin privilege.
.
Verify that Hive service is setup with Ranger authoriser and
doas=false.List of Atlas policies with ‘DLM Engine’ user on a secure cluster.
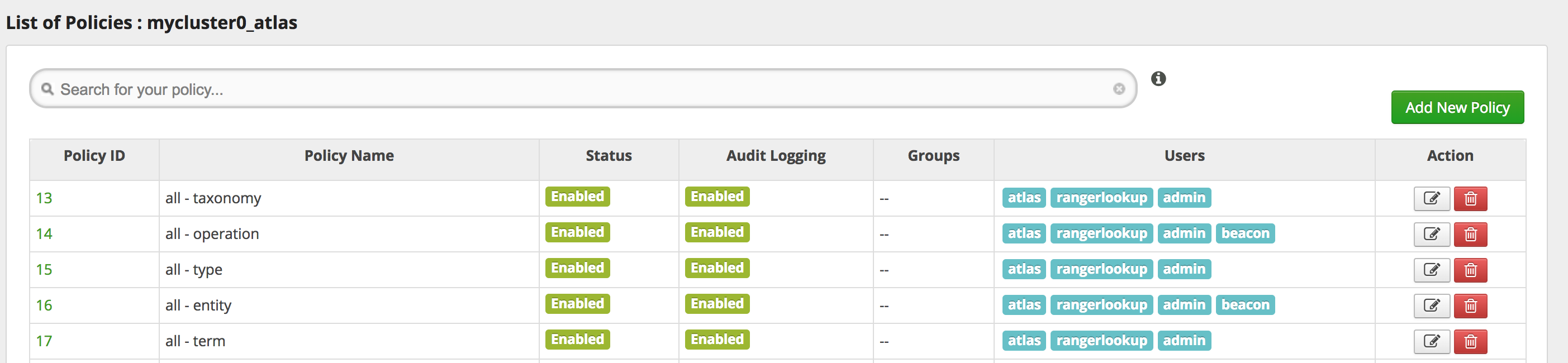
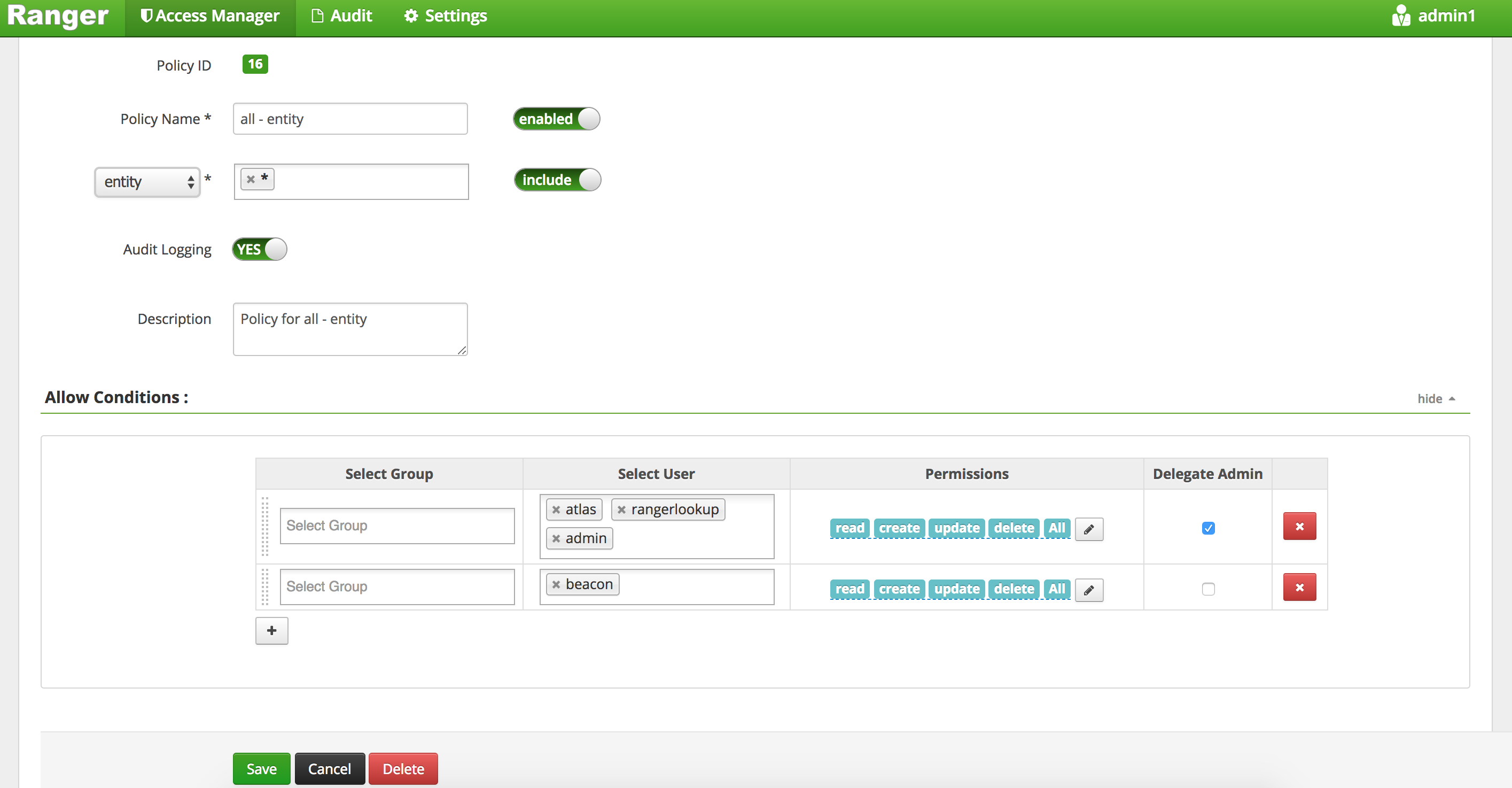
Atlas entity policy.
Atlas operation policy.