Ranger AD Integration
A conceptual overview of Ranger-AD integration architecture.
Ranger AD Integration: Architecture Overview
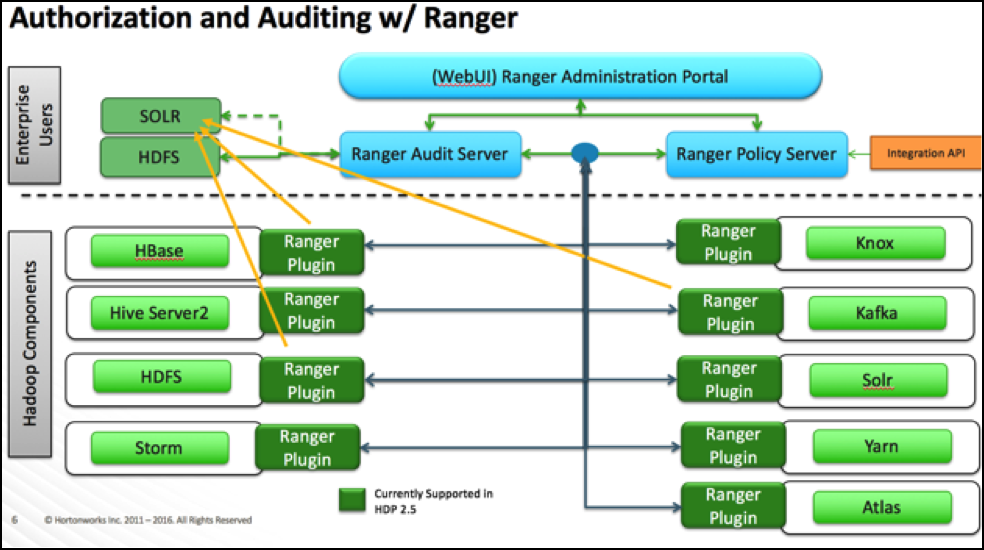
- Plugins to RPS: Ranger plugins regularly call the RPS to see if new policies were defined in the Ranger Administration Portal (RAP). Generally it takes approximately 30 seconds for a policy to be updated.
- RPS to components: The RPS queries the component for meta objects that live on the component to base policies upon (this provides the autocomplete and drop-down list when defining policies).
The first communication channel (Plugin to RPS) is essential for the plugin to function, whereas the second (RPS to components) is optional. It would still be possible to define and enforce policies without the second channel, but you would not have autocomplete during policy definition.
Configuration details on both communication channels are configured in both Cloudera Manager and in the Ranger Administration Portal.
Example for HDFS plugin on a kerberized cluster:
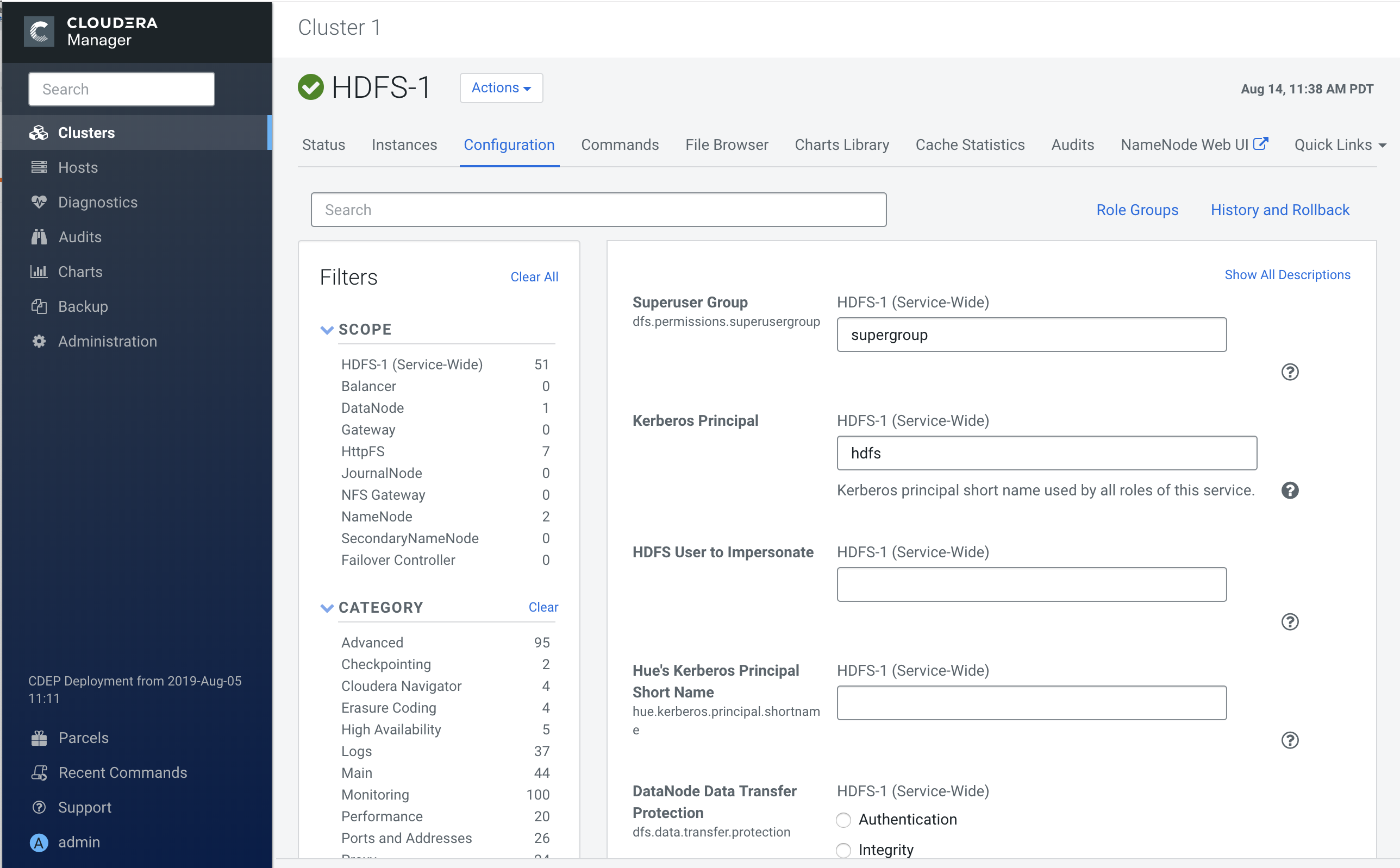
The Kerberos principal short name for the HDFS service,"hdfs", is the one that is involved the second communication channel (RPS to components) for getting metadata from HDFS (such as HDFS folders) across. The settings on the HDFS configuration must match those set in Ranger (by selecting Access > Manager > Resource Based Policies, then selecting the Edit icon for the HDFS service:
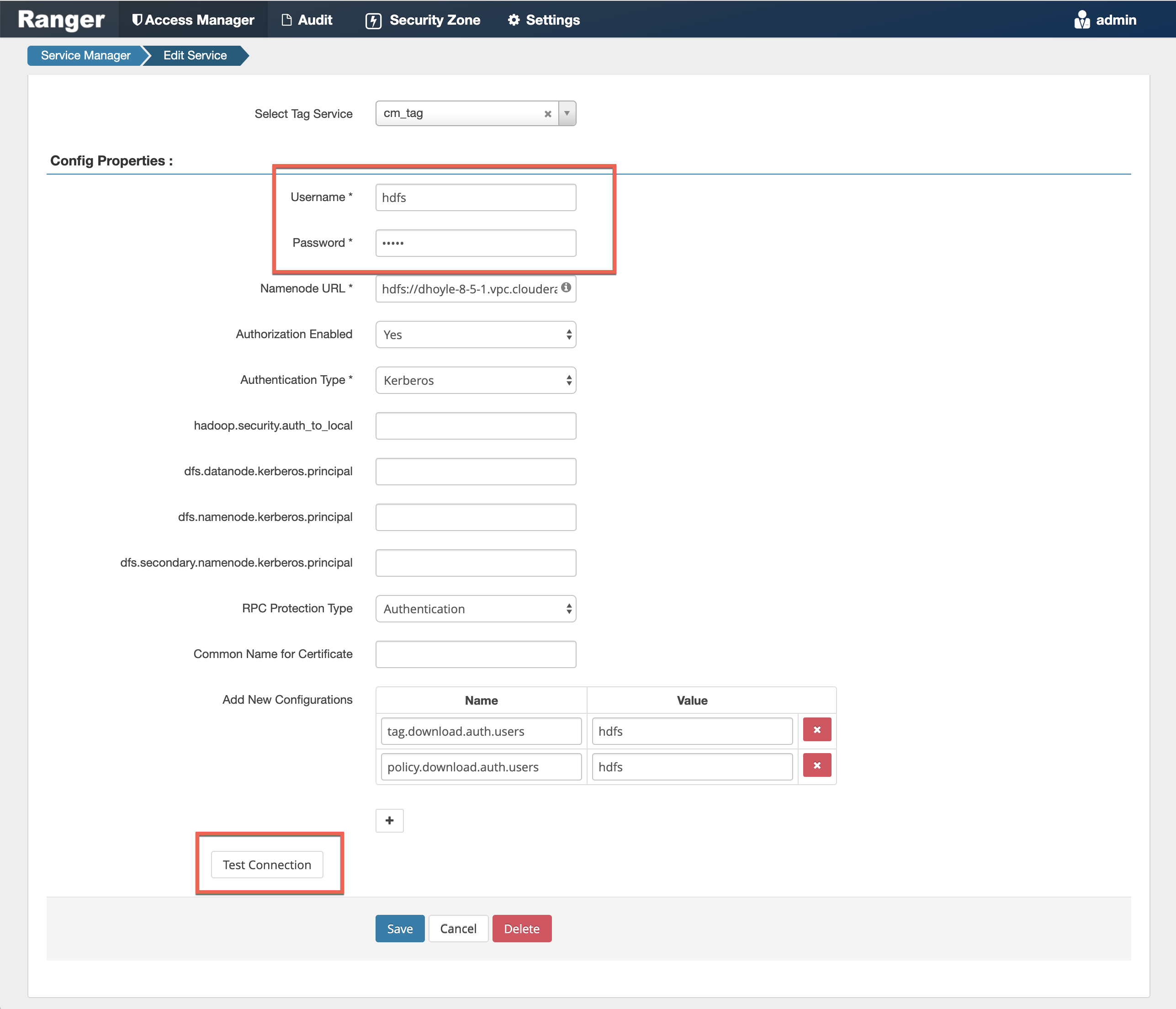
To verify the second communication channel (RPS to components) click Test Connection for the applicable service (as shown above for the HDFS service). A confirmation message appears if the connection works successfully.
To verify if the paramount first communication channel (Plugins to RPS) works, select Audit > Plugins in Ranger:
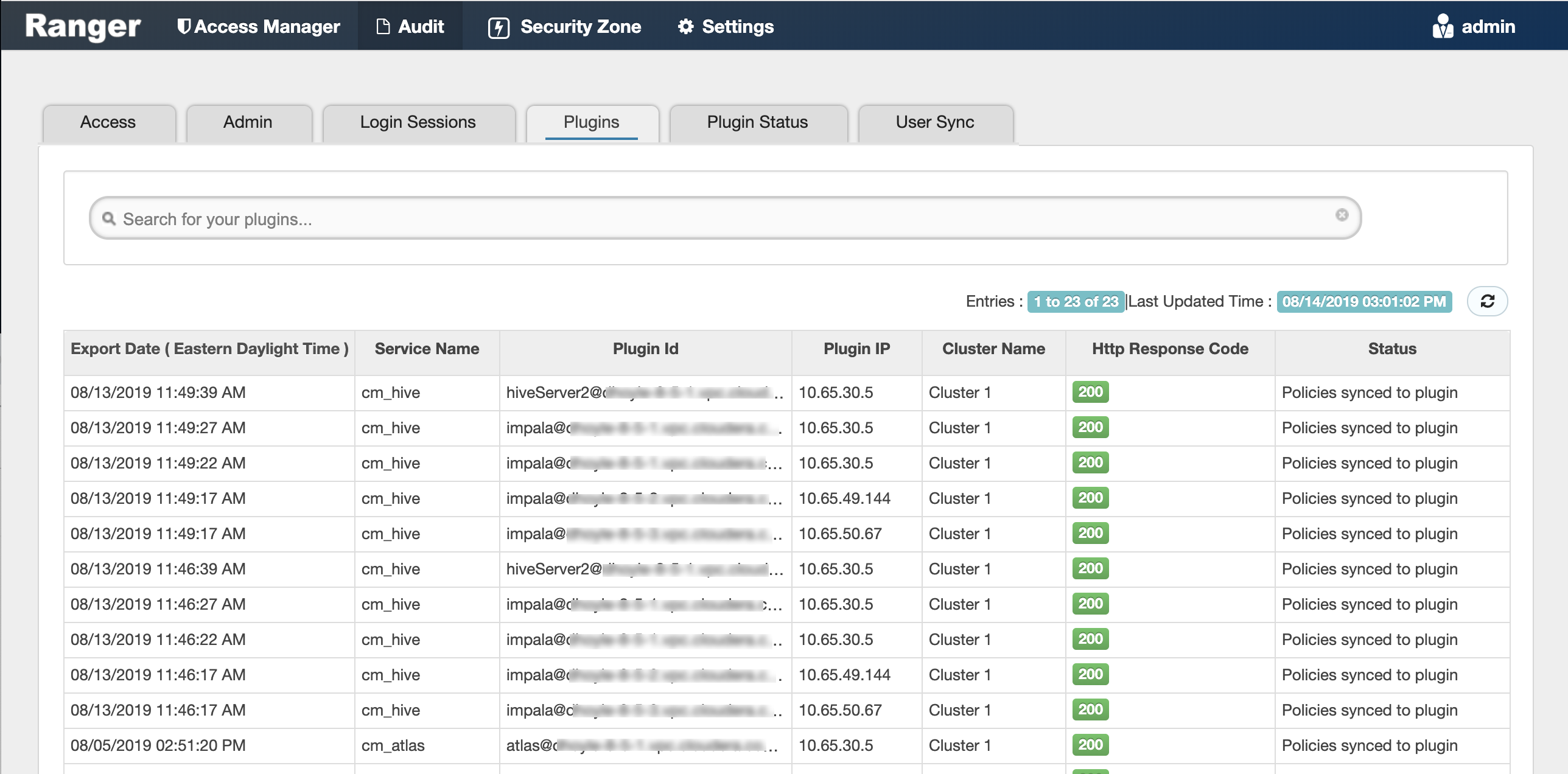
Ranger AD Integration: Ranger Audit
Ranger plugins furthermore send their audit event (whether access was granted or not and based on which policy) directly to the configured sink for audits, which can be HDFS, Solr or both. This is indicated by the yellow arrows in the architectural graph.
The audit access tab on the RAP (Audit > Access) is only populated if Solr is used as the sink.
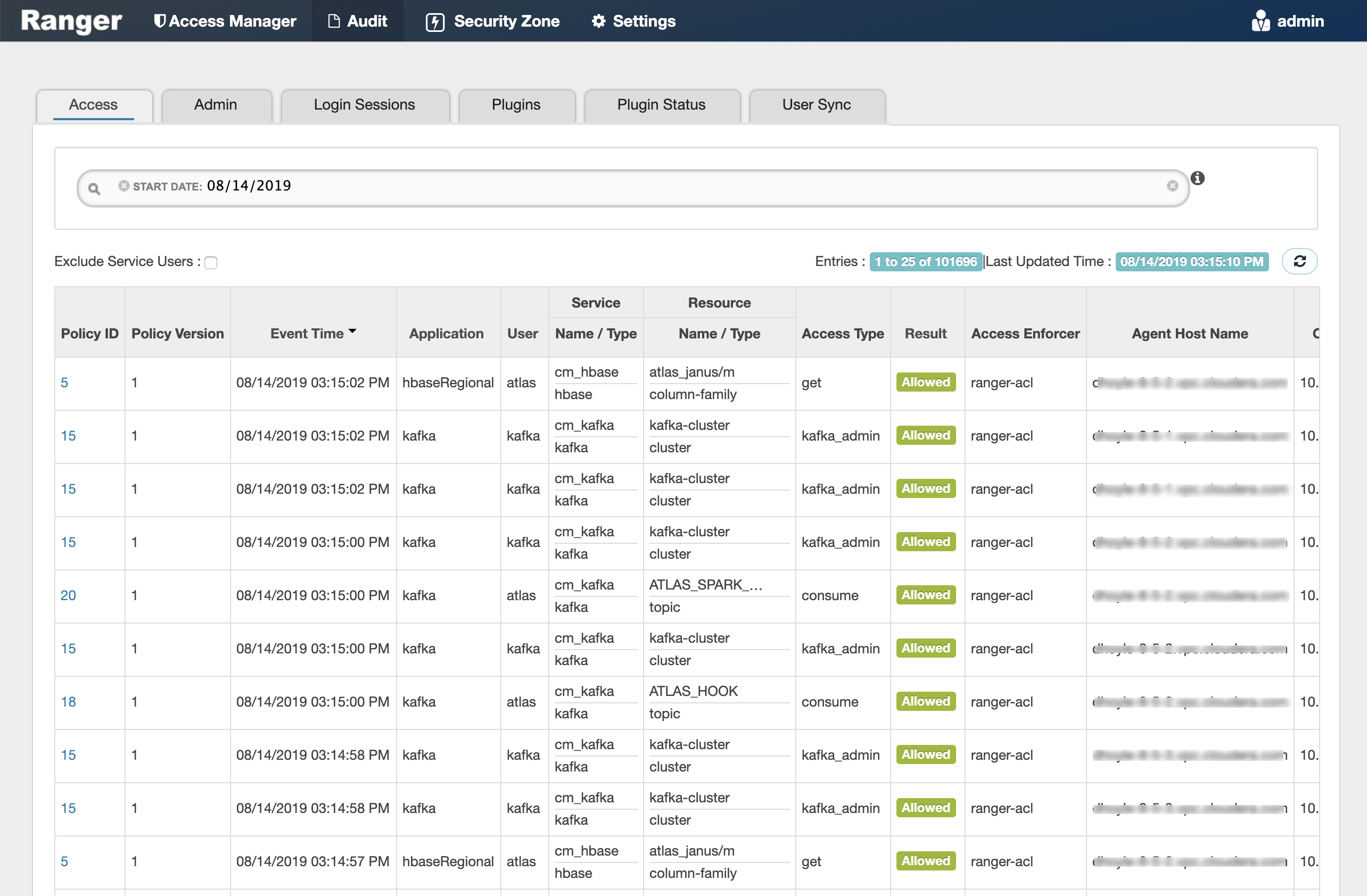
This screen points out an important Ranger feature. When the plugin is enabled AND no specific policy is in place for access to some object, the plugin will fall back to enforcing the standard component-level Access Control Lists (ACLs). For HDFS that would be the user : rwx / group : rwx / other : rwx ACLs on folders and files.
Once this defaulting to component ACLs happens, the audit events list a " - " in the Policy ID column instead of a policy number. If a Ranger policy was in control of allowing/denying access, the policy number is shown.
Ranger AD Integration: Overview
Rangers AD Integration has 2 levels:
- Ranger UI authentication (which users can log in to Ranger itself).
- Ranger user/group sync (which users/groups to define policies for)


