Create an Encryption Key
Create a "master" encryption key for the new encryption zone. Each key will be specific to an encryption zone.
Ranger supports AES/CTR/NoPadding as the cipher suite. (The associated property is listed under HDFS -> Configs in the Advanced hdfs-site list.)
Key size can be 128 or 256 bits.
Recommendation: create a new superuser for key
management. In the following examples, superuser encr creates the key.
This separates the data access role from the encryption role, strengthening
security.
Create an Encryption Key using Ranger KMS (Recommended)
In the Ranger Web UI screen:
Choose the Encryption tab at the top of the screen.
Select the KMS service from the drop-down list.
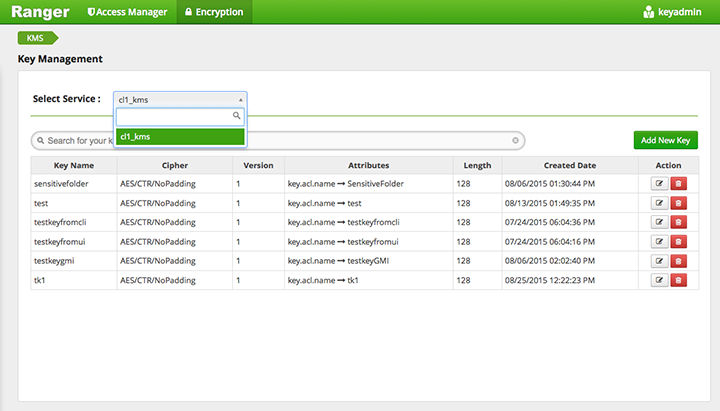
To create a new key:
Click on "Add New Key":
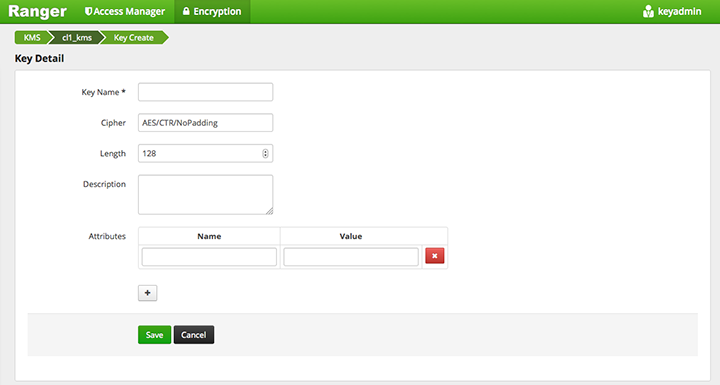
Add a valid key name.
Select the cipher name. Ranger supports AES/CTR/NoPadding as the cipher suite.
Specify the key length, 128 or 256 bits.
Add other attributes as needed, and then save the key.
For information about rolling over and deleting keys, see Using the Ranger Key Management Service.
![[Warning]](../common/images/admon/warning.png) | Warning |
|---|---|
Do not delete an encryption key while it is in use for an encryption zone. This will result in loss of access to data in that zone. |
Create an Encryption Key using the CLI
The full syntax of the hadoop key create command is as follows:
[create <keyname> [-cipher <cipher>] [-size <size>] [-description <description>] [-attr <attribute=value>] [-provider <provider>] [-help]]
Example:
# su - encr
# hadoop key create <key_name> [-size <number-of-bits>]
The default key size is 128 bits. The optional -size parameter
supports 256-bit keys, and requires the Java Cryptography Extension (JCE)
Unlimited Strength Jurisdiction Policy File on all hosts in the cluster. For
installation information, see Installing the JCE.
Example:
# su - encr
# hadoop key create key1
To verify creation of the key, list the metadata associated with the current user:
# hadoop key list -metadata
For information about rolling over and deleting keys, see Using the Ranger Key Management Service.
![[Warning]](../common/images/admon/warning.png) | Warning |
|---|---|
Do not delete an encryption key while it is in use for an encryption zone. This will result in loss of access to data in that zone. |