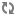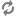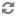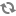Configure Ranger User Sync
This section describes how to configure Ranger User Sync for either UNIX or LDAP/AD.
Test Run Ranger Usersync
Steps
Before committing to usersync changes, it is recommended that you test-run that users and groups are being retrieved as intended.
To test-run loading User and Group data into Ranger before committing to the changes:
Set
ranger.usersync.policymanager.mockrun=true. This parameter can be found inAmbari> Ranger> Configs> Advanced> Advanced ranger-ugsync-site.View the Users and Groups that will be loaded into Ranger:
tail -f /var/log/ranger/usersync/usersync.log.After confirming that the users and groups are retrieved as intended, set
ranger.usersync.policymanager.mockrun=falseand restart Ranger Usersync.This will sync the users shown in the usersync log to the Ranger database.
Configuring Ranger User Sync for UNIX
Before you begin
Before committing to usersync changes, it is recommended that you test-run that users and groups are being retrieved as intended: Test Run Ranger Usersync.
Steps
Use the following steps to configure Ranger User Sync for UNIX.
On the Customize Services page, select the Ranger User Info tab.
Click Yes under Enable User Sync.
Use the Sync Source drop-down to select UNIX, then set the following properties.
Table 3.6. UNIX User Sync Properties
Property Description Default Value Sync Source Only sync users above this user ID. 500 Password File The location of the password file on the Linux server. /etc/passwd Group File The location of the groups file on the Linux server. /etc/group 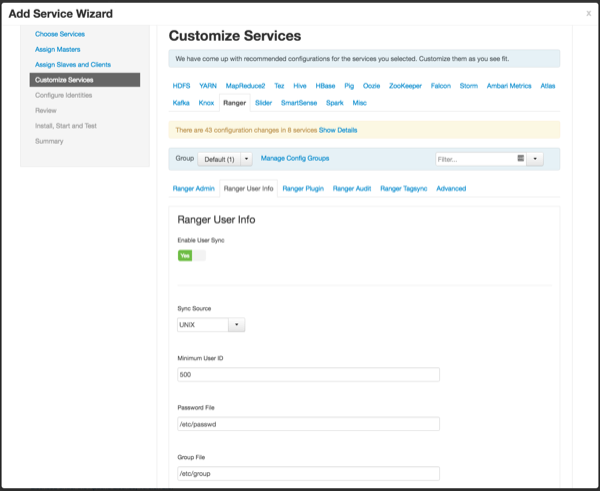
Configuring Ranger User Sync for LDAP/AD
![[Important]](../common/images/admon/important.png) | Important |
|---|---|
To ensure that LDAP/AD group level authorization is enforced in Hadoop, you should set up Hadoop group mapping for LDAP/AD. |
![[Note]](../common/images/admon/note.png) | Note |
|---|---|
You can use the LDAP Connection Check tool to determine User Sync settings for LDAP/AD. |
Before you begin
Before committing to usersync changes, it is recommended that you test-run that users and groups are being retrieved as intended: Test Run Ranger Usersync.
Steps
Use the following steps to configure Ranger User Sync for LDAP/AD.
On the Customize Services page, select the Ranger User Info tab.
Click Yes under Enable User Sync.
Use the Sync Source drop-down to select LDAP/AD.
Set the following properties on the Common Configs tab.
Table 3.7. LDAP/AD Common Configs
Property Description Default Value Sample Values LDAP/AD URL Add URL depending upon LDAP/AD sync source ldap://{host}:{port} ldap://ldap.example.com:389 or ldaps://ldap.example.com:636 Bind Anonymous If Yes is selected, the Bind User and Bind User Password are not required. NO Bind User The location of the groups file on the Linux server. The full distinguished name (DN), including common name (CN), of an LDAP/AD user account that has privileges to search for users. The LDAP bind DN is used to connect to LDAP and query for users and groups. cn=admin,dc=example,dc=com or admin@example.com Bind User Password The password of the Bind User. 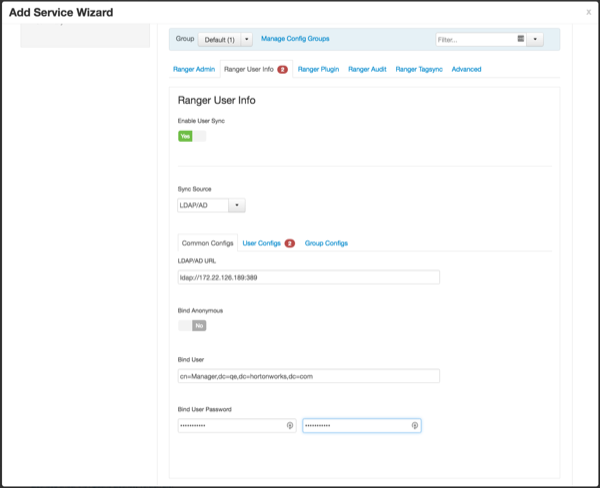
Set the following properties on the User Configs tab.
Table 3.8. LDAP/AD User Configs
Property Description Default Value Sample Values Group User Map Sync Sync specific groups for users. Yes Yes Username Attribute The LDAP user name attribute. sAMAccountName for AD, uid or cn for OpenLDAP User Object Class Object class to identify user entries. person top, person, organizationalPerson, user, or posixAccount User Search Base Search base for users.
Ranger can search multiple OUs in AD. Ranger UserSync module performs a user search on each configured OU and adds all the users into single list. Once all the OUs are processed, a user’s group membership is computed based on the group search.
cn=users,dc=example,dc=com;ou=example1,ou=example2 User Search Filter Optional additional filter constraining the users selected for syncing. Sample filter to retrieve all the users: cn=*
Sample filter to retrieve all the users who are members of groupA or groupB: (|(memberof=CN=GroupA,OU=groups,DC=example,DC=com)(memberof=CN=GroupB,OU=groups,DC=example,DC=com))
User Search Scope This value is used to limit user search to the depth from search base. sub base, one, or sub User Group Name Attribute Attribute from user entry whose values would be treated as group values to be pushed into the Access Manager database. You can provide multiple attribute names separated by commas. memberof,ismemberof memberof, ismemberof, or gidNumber
Enable User Search This option is available only when the "Enable Group Search First" option is selected. No Yes 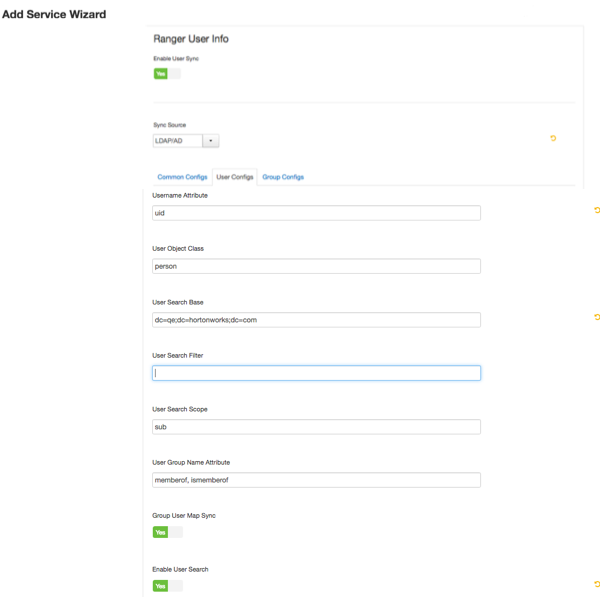
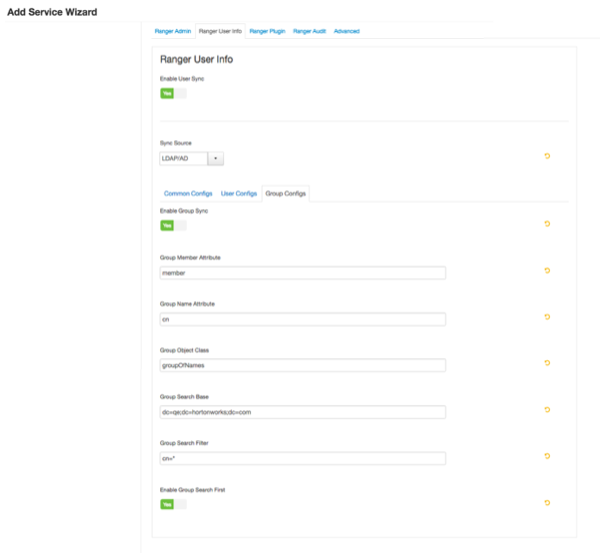
Set the following properties on the Group Configs tab.
Table 3.9. LDAP/AD Group Configs
Property Description Default Value Sample Values Enable Group Sync If Enable Group Sync is set to No, the group names the users belong to are derived from “User Group Name Attribute”. In this case no additional group filters are applied.
If Enable Group Sync is set to Yes, the groups the users belong to are retrieved from LDAP/AD using the following group-related attributes.
No Yes Group Member Attribute The LDAP group member attribute name. member Group Name Attribute The LDAP group name attribute. distinguishedName for AD, cn for OpenLdap Group Object Class LDAP Group object class. group, groupofnames, or posixGroup Group Search Base Search base for groups.
Ranger can search multiple OUs in AD. Ranger UserSync module performs a user search on each configured OU and adds all the users into single list. Once all the OUs are processed, a user’s group membership is computed based on the group search configuration. Each OU segment needs to be separated by a ; (semi-colon).
ou=groups,DC=example,DC=com;ou=group1;ou=group2 Group Search Filter Optional additional filter constraining the groups selected for syncing. Sample filter to retrieve all groups: cn=*
Sample filter to retrieve only the groups whose cn is Engineering or Sales: (|(cn=Engineering)(cn=Sales))
Enable Group Search First When Enable Group Search First is selected, there are two possible ways of retrieving users:
If Enable User Search is not selected: users are retrieved from the “member” attribute of the group.
If Enable User Search is selected: user membership is computed by performing an LDAP search based on the user configuration.
No Yes