WebHDFS
Recommendations
WebHDFS is supported for writing and reading files to and from encryption zones.
Steps
To access encrypted files via WebHDFS, complete the following steps:
To enable WebHDFS in
hdfs-site.xml, set thedfs.webhdfs.enabledproperty to true:<property> <name>dfs.webhdfs.enabled</name> <value>true</value> </property>
Make sure that you have separate HDFS administrative and service users, as described in Creating an HDFS Admin User.
KMS supports a blacklist and a whitelist for key access (through
kms-acls.xml).By default the
hdfsservice user is included in the blacklist for decrypt_eek operations. To support WebHDFS, the HDFS service user must not be on the key access blacklist. Remove the HDFS service user from the blacklist:To edit the blacklist using Ambari, go to Ranger KMS -> Configs, and search for "blacklist" or open the Advanced dbks-site list.
Remove
hdfsfrom thehadoop.kms.blacklist.DECRYPT_EEKproperty: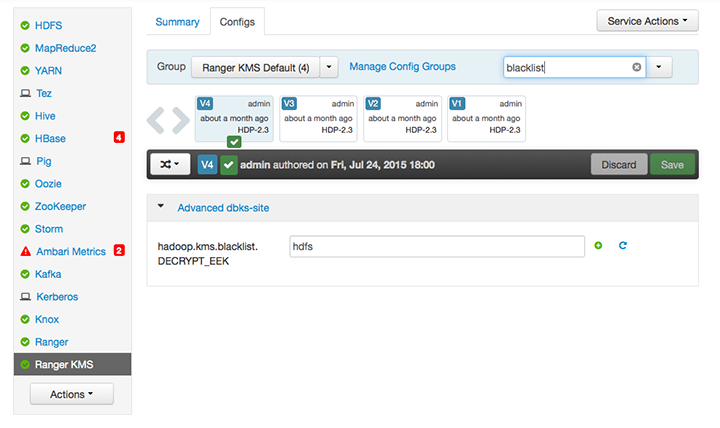
Restart Ranger KMS.
The HDFS service user must have GENERATE_EEK and DECRYPT_EEK permissions. To add the permissions using the Ranger Web UI, select the Access Manager tab-> Resource Based Policies (the default Access Manager view). Select the key store, select the policy, and click the edit icon. In the Permissions column click the edit icon and check the boxes for GenerateEEK and DecryptEEK. Then click Save.
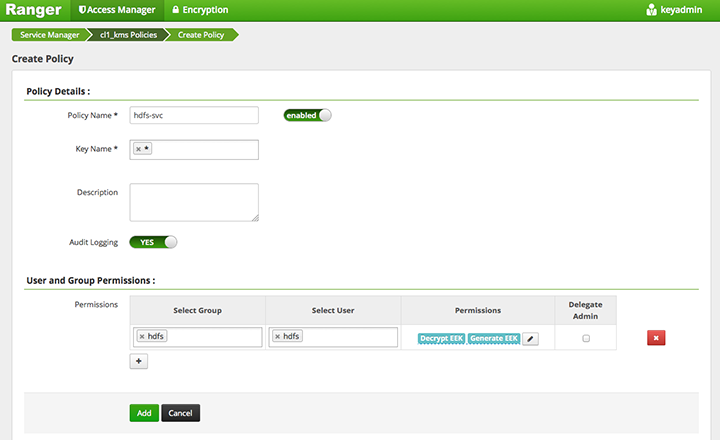
Because the HDFS service user will have access to all keys, the HDFS service user should not be the administrative user. Specify a different administrative user in
hdfs-site.xmlfor the administrative user.
For more information about operational tasks using Ranger KMS, see the Ranger KMS Administration Guide.