Knox SSO
Identity Providers
Knox has two identity providers: form-based and SAML 2.0.
Setting up Knox SSO for Ambari
This section describes how to configure Ambari to use Knox SSO (Single Sign-on) to authenticate users. With this configuration, unauthenticated users who try to access Ambari are redirected to the Knox SSO login page for authentication.
Use the following steps to configure Knox SSO for Ranger:
Log in as the root user
Run the following command:
ambari-server setup-sso
When prompted, enter
y.For the provider URL, enter:
https://.<hostname>:8443/gateway/knoxsso/api/v1/webssoRun the following CLI command to export the Knox certificate:
JAVA_HOME/bin/keytool -export -alias gateway-identity -rfc -file <cert.pem> -keystore /usr/hdp/current/knox-server/data/security/keystores/gateway.jks
When prompted, enter the Knox master password.
Note the location where you save the
cert.pemfile.
When prompted to configure advanced properties, enter
n.Leave
JWT Cookie name (hadoop-jwt)andJWT audiences listempty.The prompt returns
Ambari Server 'setup-sso' completed successfully.Restart the Ambari Server:
ambari-server restart.
Example 2.2. Example Knox SSO for Ambari
ambari-server setup-sso Setting up SSO authentication properties... Do you want to configure SSO authentication [y/n] (y)?y Provider URL [URL] (http://example.com):https://c6402.ambari.apache.org:8443/gateway/knoxsso/api/v1/websso Public Certificate pem (empty) (empty line to finish input): MIICYTCCAcqgAwIBAgIIHd3j94bX9IMwDQYJKoZIhvcNAQEFBQAwczELMAkGA1UEBhMCVVMxDTAL BgNVBAgTBFRlc3QxDTALBgNVBAcTBFRlc3QxDzANBgNVBAoTBkhhZG9vcDENMAsGA1UECxMEVGVz dDEmMCQGA1UEAxMda25veHNzby1za29uZXJ1LTItMi5ub3ZhbG9jYWwwHhcNMTYwMzAxMTEzMTQ0 WhcNMTcwMzAxMTEzMTQ0WjBzMQswCQYDVQQGEwJVUzENMAsGA1UECBMEVGVzdDENMAsGA1UEBxME VGVzdDEPMA0GA1UEChMGSGFkb29wMQ0wCwYDVQQLEwRUZXN0MSYwJAYDVQQDEx1rbm94c3NvLXNr b25lcnUtMi0yLm5vdmFsb2NhbDCBnzANBgkqhkiG9w0BAQEFAAOBjQAwgYkCgYEAlV0Jtd8zmzVZ UZRbqxXvK9MV5OYIOWTX9/FMthwr99eClHp3JdZ1x3utYr9nwdZ6fjZaUIihzu8a8SGoipbW2ZVU TShGZ/5VKtu96YcSAoB3VTyc3WWRDGERRs7aKAlEqnURDkQz7KRs2tvItJpBBjrTXZpHKFTOecL4 hCkaalUCAwEAATANBgkqhkiG9w0BAQUFAAOBgQAqvPfl4fivozd+4QI4ZBohFHHvf1z4Y7+DxlY7 iNAnjnau4W3wgwTt6CQ1B9fSx3zVTlhu2PfDJwvumBbuKuth/M+KXpG28AbKIojrL2Odlv+cftrJ YeJC6Qjee+5Pf2P9G2wd9fahWF+aQpr50YlMZSU+VMiTO2a2FSAXvOdjvA== Do you want to configure advanced properties [y/n] (n) ?y JWT Cookie name (hadoop-jwt): JWT audiences list (comma-separated), empty for any (): Ambari Server 'setup-sso' completed successfully. ambari-server restart
Setting up Knox SSO for Ranger
This section describes how to configure Ranger to use Knox SSO (Single Sign-on) to authenticate users on an Ambari cluster. With this configuration, unauthenticated users who try to access Ranger are redirected to the Knox SSO login page for authentication.
![[Note]](../common/images/admon/note.png) | Note |
|---|---|
|
Use the following steps to configure Knox SSO for Ranger:
Install Ambari with HDP-2.5 or higher. Install Knox along with the other services.
The Knox SSO topology settings are preconfigured in Knox > Configs > Advanced knoxsso-topology.
Run the following CLI command to export the Knox certificate:
JAVA_HOME/bin/keytool -export -alias gateway-identity -rfc -file <cert.pem> -keystore /usr/hdp/current/knox-server/data/security/keystores/gateway.jks
When prompted, enter the Knox master password.
Note the location where you save the
cert.pemfile.
Select Ranger > Configs > Advanced > Knox SSO Settings and set the following properties:
Enable Ranger SSO – Select this check box to enable Ranger SSO.
SSO provider url –
https://<knox_host>:8443/gateway/knoxsso/api/v1/webssoSSO public key – Paste in the contents of the
cert.pemcertificate file exported from Knox.When you paste the contents, exclude the header and footer.
SSO browser useragent – Preconfigured with
Mozilla,chrome.
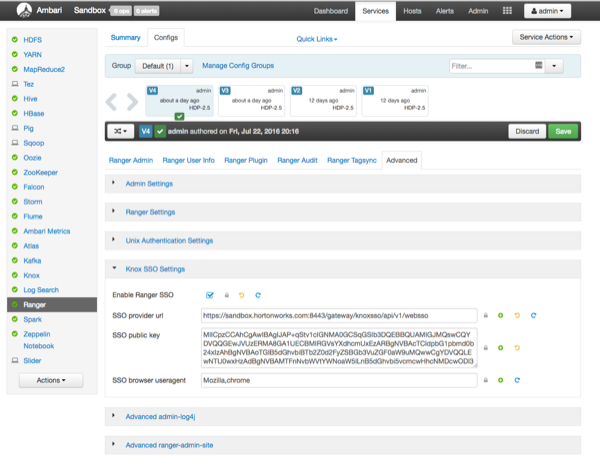
Click Save to save the new configuration, then click through the confirmation pop-ups.
Restart Ranger. Select Actions > Restart All Required to restart all other services that require a restart.
Knox SSO should now be enabled. Users who try to access Ranger are redirected to the Knox SSO login page for authentication.