Configuring Kerberos Authentication for HBase
Using Kerberos for authentication for the HBase component requires that you also use Kerberos authentication for ZooKeeper. This means that HBase Master, RegionServer, and client hosts
must each have a Kerberos principal for authenticating to the ZooKeeper ensemble. The steps below provide the details. Before you start, be sure that:
- Kerberos is enabled for the cluster, as detailed in Enabling Kerberos Authentication Using the Wizard.
- Kerberos principals for Cloudera Manager Server, HBase, and ZooKeeper hosts exist and are available for use. See Managing Kerberos Credentials Using Cloudera Manager for details.
Cloudera Manager automatically configures authentication between HBase to ZooKeeper and sets up the HBase Thrift gateway to support impersonation (doAs).
However, you must manually configure the HBase REST service for Kerberos (it currently uses Simple authentication by default, instead of Kerberos). See Configure HBase REST Server for Kerberos Authentication for details.
You can use either Cloudera Manager or the command line to configure Kerberos authentication for HBase. Using Cloudera Manager simplifies the process, but both approaches are detailed below. This page includes these topics:
Configuring Kerberos Authentication for HBase Using Cloudera Manager
Cloudera Manager simplifies the task of configuring Kerberos authentication for HBase.
Configure HBase Servers to Authenticate with a Secure HDFS Cluster Using Cloudera Manager
Required Role: Cluster Administrator or Full Administrator
- Log on to Cloudera Manager Admin Console.
- Go to the HBase service (select ).
- Click the Configuration tab.
- Under the Scope filter, click HBase (Service-Wide).
- Under the Category filter, click Security.
- Ensure the Kerberos principal for the HBase service was generated.
- Find the HBase Secure Authentication property (type "HBase Secure" in the Search box, if necessary), and confirm (or enter) the principal to use for HBase.
- Select kerberos as the authentication type.
- Click Save Changes.
- Restart the role.
- Restart the service. Select Restart from the Actions drop-down menu adjacent to HBASE-n (Cluster).
Configure HBase Servers and Clients to Authenticate with a Secure ZooKeeper
As mentioned above, secure HBase also requires secure ZooKeeper. The various HBase host systems—Master, RegionServer, and client—must have a principal to use to authenticate to the secure ZooKeeper ensemble. This is handled transparently by Cloudera Manager when you enable Kerberos as detailed above.
Configure HBase REST Server for Kerberos Authentication
Currently, the HBase REST Server uses Simple (rather than Kerberos) authentication by default. You must manually modify the setting using the Cloudera Manager Admin Console, as
follows:
- Log on to Cloudera Manager Admin Console.
- Select .
- Click the Configuration tab.
- Under the Scope filter, click HBase (Service-Wide).
- Under the Category filter, click Security.
- Find the HBase REST Authentication property:
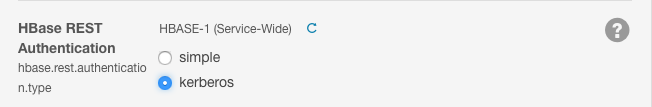
- Click kerberos to select Kerberos instead of simple authentication.
- Click Save Changes.
- Restart the role.
- Restart the service. Select Restart from the Actions drop-down menu adjacent to HBASE-n (Cluster).