Configuring the Ranger KMS Server for SSL
Use the following steps to configure Ranger KMS (Key Management Service) Server for SSL.
Stop Ranger KMS by selecting Service Actions > Stop.
Use the following CLI commands to change to the Ranger KMS configuration directory and create a self-signed certificate.
cd /etc/ranger/kms/conf keytool -genkey -keyalg RSA -alias rangerkms -keystore ranger-kms-keystore.jks -storepass rangerkms -validity 360 -keysize 2048 chown kms:kms ranger-kms-keystore.jks chmod 400 ranger-kms-keystore.jks
When prompted, provide an identifiable string as the value for the "What is your first and last name?" question. then provide answers to the subsequent questions to create the keystore. When prompted for a password, press the Enter key.
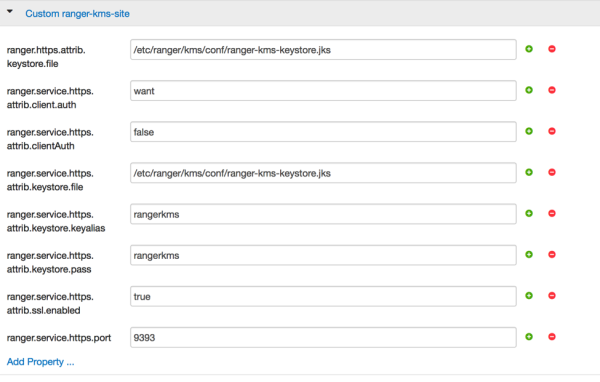
Select Custom ranger-kms-site, then add the following properties as shown below:
ranger.https.attrib.keystore.file
ranger.service.https.attrib.keystore.file (duplicate of above – workaround for now)
ranger.service.https.attrib.clientAuth
ranger.service.https.attrib.client.auth (duplicate of above – workaround for now)
ranger.service.https.attrib.keystore.keyalias
ranger.service.https.attrib.keystore.pass
ranger.service.https.attrib.ssl.enabled
ranger.service.https.port
Under Advanced kms_env, update the value of kms_port to match the value of ranger.service.https.port.
Save your changes and restart Ranger KMS.
When you attempt to access the Ranger KMS UI with the HTTPS protocol on the port specified by the ranger.service.https.port property, the browser should report that it does not trust the site. Click Proceed anyway and you should be able to access the Ranger Admin UI over HTTPS.
Use the following CLI commands to export the Ranger KMS certificate.
cd /usr/hdp/<version>/ranger-kms/conf keytool -export -keystore ranger-kms-keystore.jks -alias rangerkms -file ranger-kms-trust.cer
Use the following CLI command to import the Ranger KMS certificate into the Ranger Admin truststore.
keytool -import -file ranger-kms-trust.cer -alias rangerkms -keystore <Truststore file used by Ranger Admin - can be the JDK cacerts> -storepass changeit
Use the following CLI command to import the Ranger KMS certificate into the Hadoop client truststore.
keytool -import -file ranger-kms-trust.cer -alias rangerkms -keystore /etc/security/clientKeys/all.jks -storepass bigdata
Restart Ranger Admin and HDFS.