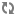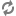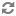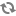Configure Ranger Authentication
This section describes how to configure Ranger authentication for UNIX, LDAP, and AD.
Configuring Ranger UNIX Authentication
Use the following steps to configure Ranger authentication for UNIX.
Select the Advanced tab on the Customize Services page.
Under Ranger Settings, specify the Ranger Access Manager/Service Manager host address in the External URL box in the format
http://<your_ranger_host>:6080.Under Ranger Settings, select UNIX.
HTTP is enabled by default -- if you disable HTTP, only HTTPS is allowed.
Under UNIX Authentication Settings, set the following properties.
Table 3.10. UNIX Authentication Settings
Property Description Default Value Example Value Allow remote Login Flag to enable/disable remote login. Only applies to UNIX authentication. true true ranger.unixauth.service.hostname The address of the host where the UNIX authentication service is running. {{ugsync_host}} {{ugsync_host}}
ranger.unixauth.service.port The port number on which the UNIX authentication service is running. 5151 5151 ![[Note]](../common/images/admon/note.png)
Note Properties with value
{{xyz}}are macro variables that are derived from other specified values in order to streamline the configuration process. Macro variables can be edited if required -- if you need to restore the original value, click the Set Recommended symbol at the right of the property box.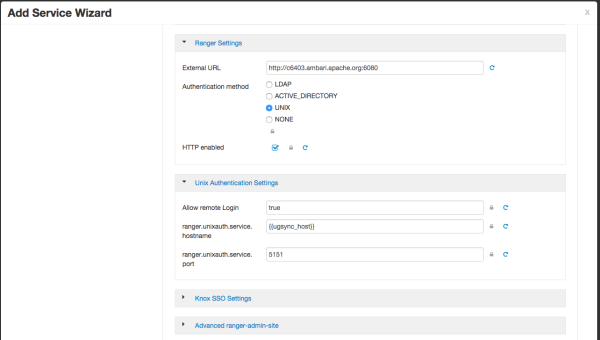
Configuring Ranger LDAP Authentication
![[Note]](../common/images/admon/note.png) | Note |
|---|---|
You can use the LDAP Connection Check tool to determine authentication settings for LDAP. |
Use the following steps to configure Ranger authentication for LDAP.
Select the Advanced tab on the Customize Services page.
Under Ranger Settings, specify the Ranger Access Manager/Service Manager host address in the External URL box in the format
http://<your_ranger_host>:6080.Under Ranger Settings, select LDAP.
Under LDAP Settings, set the following properties.
Table 3.11. LDAP Authentication Settings
Property Description Default Value Example Value ranger.ldap.base.dn The Distinguished Name (DN) of the starting point for directory server searches. dc=example,dc=com dc=example,dc=com Bind User The full Distinguished Name (DN), including Common Name (CN) of an LDAP user account that has privileges to search for users. This is a macro variable value that is derived from the Bind User value from Ranger User Info > Common Configs. {{ranger_ug_ldap_bind_dn}} {{ranger_ug_ldap_bind_dn}} Bind User Password Password for the Bind User. This is a macro variable value that is derived from the Bind User Password value from Ranger User Info > Common Configs. ranger.ldap.group. roleattribute The LDAP group role attribute. cn cn ranger.ldap.referral See description below. ignore follow | ignore | throw LDAP URL The LDAP server URL. This is a macro variable value that is derived from the LDAP/AD URL value from Ranger User Info > Common Configs. {{ranger_ug_ldap_url}} {{ranger_ug_ldap_url}} ranger.ldap.user. dnpattern The user DN pattern is expanded when a user is being logged in. For example, if the user "ldapadmin" attempted to log in, the LDAP Server would attempt to bind against the DN "uid=ldapadmin,ou=users,dc=example,dc=com" using the password the user provided>
uid={0},ou=users, dc=xasecure,dc=net cn=ldapadmin,ou=Users, dc=example,dc=com User Search Filter The search filter used for Bind Authentication. This is a macro variable value that is derived from the User Search Filter value from Ranger User Info > User Configs. {{ranger_ug_ldap_user_searchfilter}} {{ranger_ug_ldap_user_searchfilter}} ![[Note]](../common/images/admon/note.png)
Note Properties with value
{{xyz}}are macro variables that are derived from other specified values in order to streamline the configuration process. Macro variables can be edited if required -- if you need to restore the original value, click the Set Recommended symbol at the right of the property box.There are three possible values for
ranger.ldap.referral:follow,throw, andignore. The recommended setting isfollow.When searching a directory, the server might return several search results, along with a few continuation references that show where to obtain further results. These results and references might be interleaved at the protocol level.
When this property is set to
follow, the LDAP service provider processes all of the normal entries first, and then follows the continuation references.When this property is set to
throw, all of the normal entries are returned in the enumeration first, before theReferralExceptionis thrown. By contrast, a "referral" error response is processed immediately when this property is set tofolloworthrow.When this property is set to
ignore, it indicates that the server should return referral entries as ordinary entries (or plain text). This might return partial results for the search.
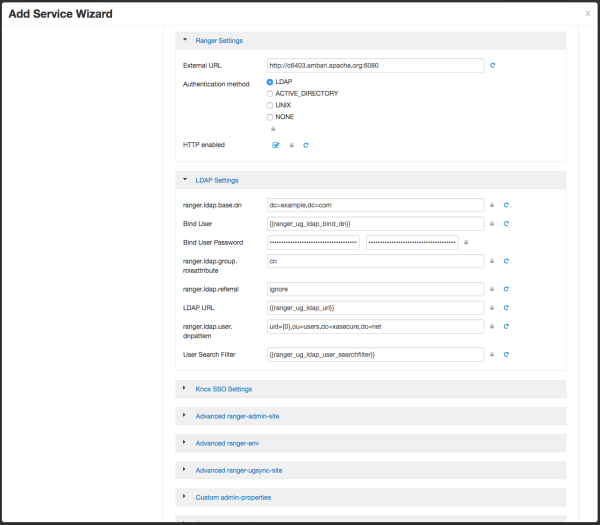
Configuring Ranger Active Directory Authentication
![[Note]](../common/images/admon/note.png) | Note |
|---|---|
You can use the LDAP Connection Check tool to determine authentication settings for Active Directory. |
Use the following steps to configure Ranger authentication for Active Directory.
Select the Advanced tab on the Customize Services page.
Under Ranger Settings, specify the Ranger Access Manager/Service Manager host address in the External URL box in the format
http://<your_ranger_host>:6080.Under Ranger Settings, select ACTIVE_DIRECTORY.
Under AD Settings, set the following properties.
Table 3.12. AD Settings
Property Description Default Value Example Value ranger.ldap.ad.base.dn The Distinguished Name (DN) of the starting point for directory server searches. dc=example,dc=com dc=example,dc=com ranger.ldap.ad.bind.dn The full Distinguished Name (DN), including Common Name (CN) of an LDAP user account that has privileges to search for users. This is a macro variable value that is derived from the Bind User value from Ranger User Info > Common Configs. {{ranger_ug_ldap_bind_dn}} {{ranger_ug_ldap_bind_dn}} ranger.ldap.ad.bind.password Password for the bind.dn. This is a macro variable value that is derived from the Bind User Password value from Ranger User Info > Common Configs. Domain Name (Only for AD) The domain name of the AD Authentication service. dc=example,dc=com ranger.ldap.ad.referral See description below. ignore follow | ignore | throw ranger.ldap.ad.url The AD server URL. This is a macro variable value that is derived from the LDAP/AD URL value from Ranger User Info > Common Configs. {{ranger_ug_ldap_url}} {{ranger_ug_ldap_url}} ranger.ldap.ad.user.searchfilter The search filter used for Bind Authentication. This is a macro variable value that is derived from the User Search Filter value from Ranger User Info > User Configs. {{ranger_ug_ldap_user_searchfilter}} {{ranger_ug_ldap_user_searchfilter}} ![[Note]](../common/images/admon/note.png)
Note Properties with value
{{xyz}}are macro variables that are derived from other specified values in order to streamline the configuration process. Macro variables can be edited if required -- if you need to restore the original value, click the Set Recommended symbol at the right of the property box.There are three possible values for
ranger.ldap.ad.referral:follow,throw, andignore. The recommended setting isfollow.When searching a directory, the server might return several search results, along with a few continuation references that show where to obtain further results. These results and references might be interleaved at the protocol level.
When this property is set to
follow, the AD service provider processes all of the normal entries first, and then follows the continuation references.When this property is set to
throw, all of the normal entries are returned in the enumeration first, before theReferralExceptionis thrown. By contrast, a "referral" error response is processed immediately when this property is set tofolloworthrow.When this property is set to
ignore, it indicates that the server should return referral entries as ordinary entries (or plain text). This might return partial results for the search. In the case of AD, aPartialResultExceptionis returned when referrals are encountered while search results are processed.
When you have finished configuring all of the Customize Services Settings, click Next at the bottom of the page to continue with the installation.
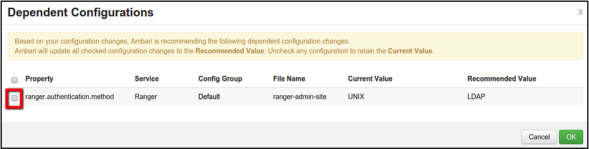
When you save the authentication method as Active Directory, a Dependent Configurations pop-up may appear recommending that you set the authentication method as LDAP. This recommended configuration should not be applied for AD, so you should clear (un-check) the ranger.authentication.method check box, then click OK.