Configure Ranger authentication for LDAP
How to configure Ranger to use LDAP for user authentication.
- In Cloudera Manager, select Ranger, then click the Configuration tab.
-
To display the authentication settings, type "authentication" in the Search
box. You may need to scroll down to see all of the LDAP settings.
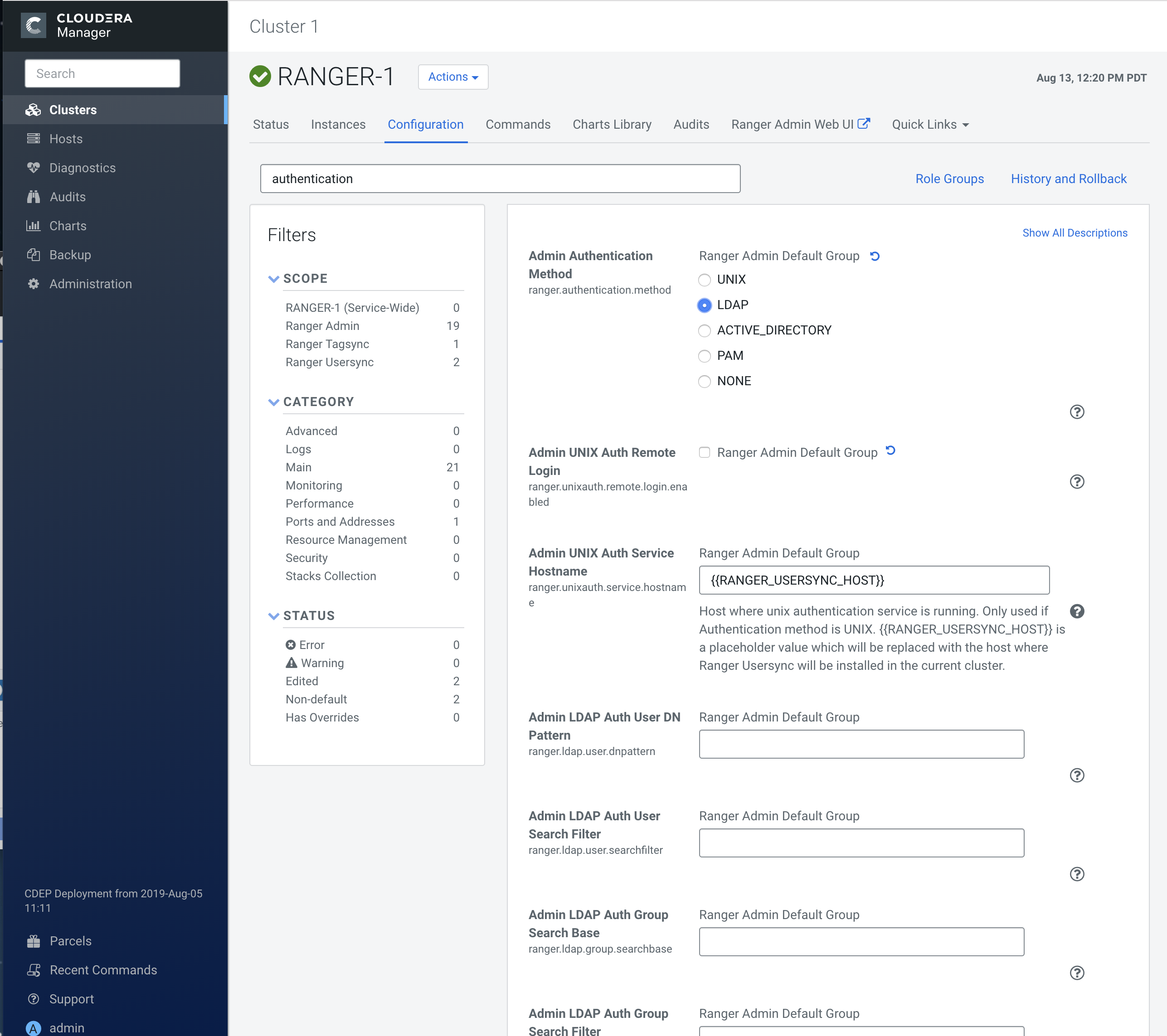
-
Configure the following settings for LDAP authentication, then click Save
Changes.
Property Description Default value Sample values Admin Authentication Method The Ranger authentication method. UNIX LDAP Admin LDAP Auth Group Search Base
ranger.ldap.group.searchbase
The LDAP group search base. N/A (|(CN=Hdp_users)(CN=Hdp_admins)) Admin LDAP Auth Group Search Filter
ranger.ldap.group.searchfilter
The LDAP group search filter. N/A Admin LDAP Auth URL
ranger.ldap.url
The LDAP server URL N/A ldap://localhost:389 or ldaps://localhost:636 Admin LDAP Auth Bind User
ranger.ldap.bind.dn
Full distinguished name (DN), including common name (CN), of an LDAP user account that has privileges to search for users. This user is used for searching the users. This could be a read-only LDAP user. N/A cn=admin,dc=example,dc=com Admin LDAP Auth Bind User Password
ranger.ldap.bind.password
Password for the account that can search for users. N/A Secret123! Admin LDAP Auth User Search Filter
ranger.ldap.user.searchfilter
The LDAP user search filter. N/A Admin LDAP Auth Base DN
ranger.ldap.base.dn
The Distinguished Name (DN) of the starting point for directory server searches. N/A dc=example,dc=com Admin LDAP Auth Group Role Attribute
ranger.ldap.group.roleattribute
The LDAP group role attribute. N/A cn Admin LDAP Auth Referral
ranger.ldap.referral*
See below. ignore follow | ignore | throw Admin LDAP Auth User DN Pattern
ranger.ldap.user.dnpattern
The LDAP user DN. N/A uid={0},ou=users,dc=xasecure,dc=net * There are three possible values for
ranger.ldap.ad.referral:follow,throw, andignore. The recommended setting isfollow.When searching a directory, the server might return several search results, along with a few continuation references that show where to obtain further results. These results and references might be interleaved at the protocol level.
-
When this property is set to
follow, the AD service provider processes all of the normal entries first, and then follows the continuation references. -
When this property is set to
throw, all of the normal entries are returned in the enumeration first, before theReferralExceptionis thrown. By contrast, a "referral" error response is processed immediately when this property is set tofolloworthrow. -
When this property is set to
ignore, it indicates that the server should return referral entries as ordinary entries (or plain text). This might return partial results for the search. In the case of AD, aPartialResultExceptionis returned when referrals are encountered while search results are processed.
-


