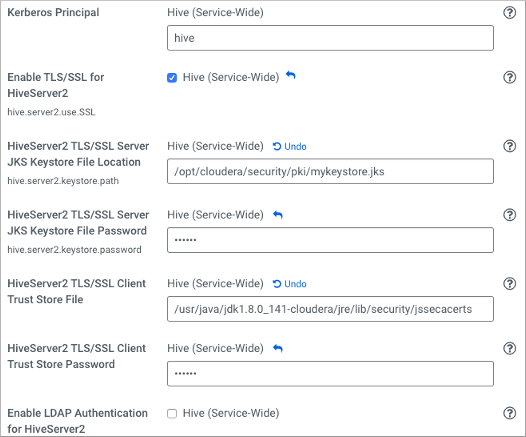
Enable TLS/SSL for HiveServer
You can secure client-server communications using symmetric-key encryption in the TLS/SSL (Transport Layer Security/Secure Sockets Layer) protocol. To encrypt data exchanged between HiveServer and its clients, you can use Cloudera Manager to configure TLS/SSL.
- HiveServer has the necessary server key, certificate, keystore, and trust store set up on the host system.
- The hostname variable (
$(hostname -f)-server.jks) was used with Java keytool commands to create keystore, as shown in this example:$ sudo keytool -genkeypair -alias $(hostname -f)-server -keyalg RSA -keystore \ /opt/cloudera/security/pki/$(hostname -f)-server.jks -keysize 2048 -dname \ "CN=$(hostname -f),OU=dept-name-optional,O=company-name,L=city,ST=state,C=two-digit-nation" \ -storepass password -keypass password
ssl=true;sslTrustStore=<path_to_truststore>. Truststore password
requirements depend on the version of Java running in the cluster: - Java 11: the truststore format has changed to PKCS and the truststore password is required; otherwise, the connection fails.
- Java 8: The trust store password does not need to be specified.