Enabling or disabling impersonation (doas)
As administrator, you must understand the permissions model supported in CDP Private Cloud Base and later. If you do not use Apache Ranger for security, you need to add users to an HDFS access control list (ACL) to permit access to the Hive warehouse for running DML queries on external tables. You base your doas configuration on the type of table you generally create.
Hive 3 supports the HDFS access control model instead of the legacy Hive permission inheritance
based on the hive.warehouse.subdir.inherit.perms parameter setting. In Apache
Hive 3, a directory inherits permissions from the Default ACL.
Configure services for this behavior, as described below:
Disable impersonation to use Ranger
When you enable Ranger, you disable user impersonation (doAs=false). This is
the Hive default and Ranger is the recommended security model. Managed, ACID tables as well as
external tables, secured by Ranger, are supported in this configuration. Impersonation of the
end user is disabled, which is the state required by Hive for managing ACID tables.
In Cloudera Manager, click and search for (hive.server2.enable.doAs).
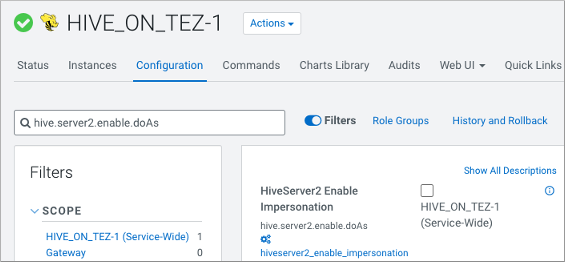
Uncheck Hive (Service-Wide) to disable impersonation.
With no impersonation, HiveServer authorizes only the hive user to access
Hive tables.
Enable impersonation to use SBA
As administrator, if you do not use the recommended Ranger security, you simply enable the
doAs impersonation parameter to use SBA: In Cloudera Manager, click and for HiveServer2 Enable Impersonation, check
Hive (Service-Wide) to enable impersonation
(doAs=true).
External tables are supported in this configuration. ACID, managed tables are not supported. Impersonation of the end user is enabled.


