Configuring Access to Azure on CDP Private Cloud Base
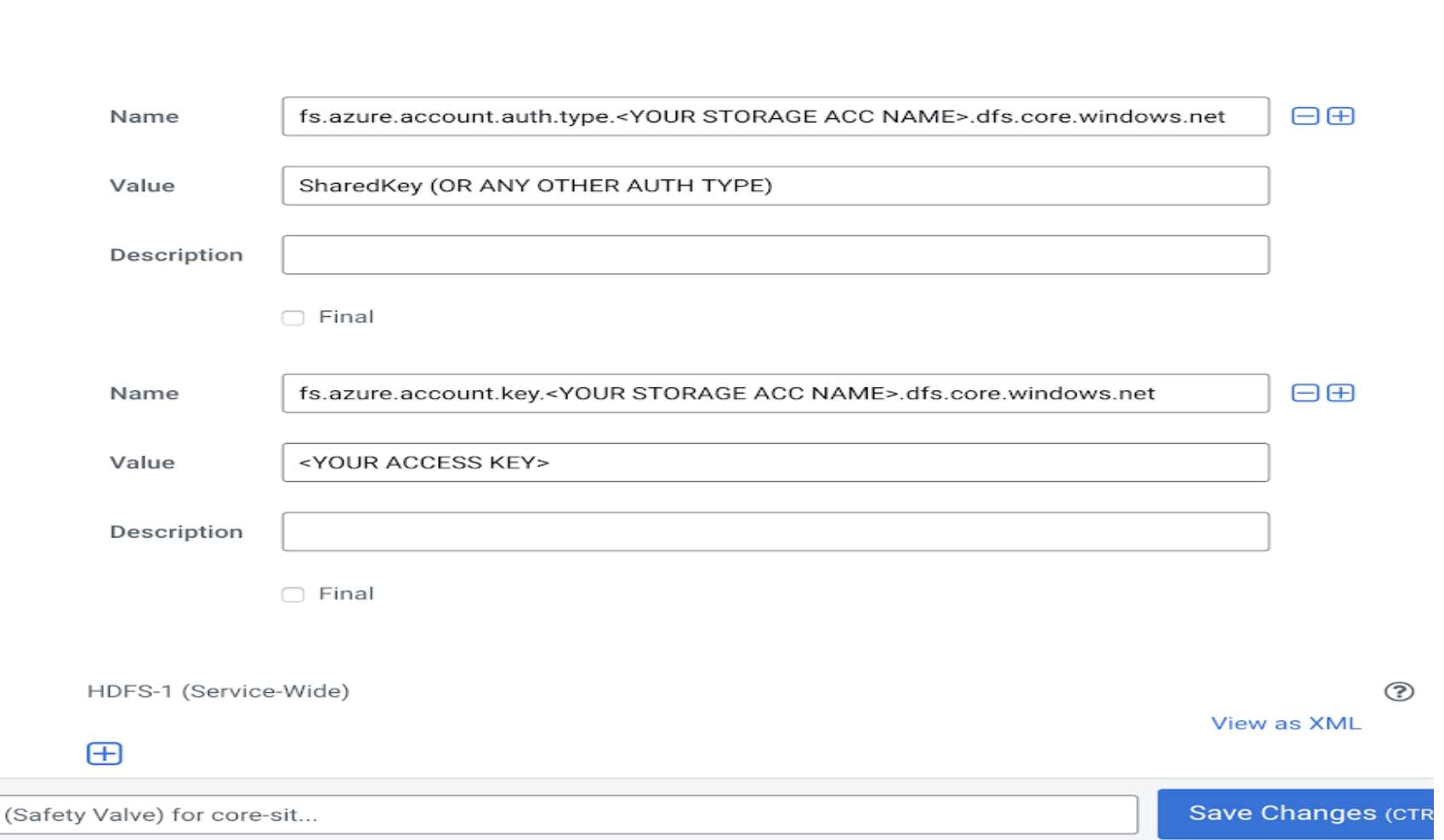
You can use Shared Key, Managed Instance, Shared Access Signature, and so on to configure access credentials to authorise access to Azure containers. For example, a shared key account can be configured for use regardless of which account is accessed with the property fs.azure.account.key or you can configure an identity to be used only for a specific storage account with fs.azure.account.key.<BUCKET NAME>.blob.core.windows.net.