Known Issues
Summarizes known issues for this release.
- JDK limitation
- JDK 8u271, JDK 8u281, and JDK 8u291 may cause socket leak issues in NiFi due to JDK-8245417 and JDK-8256818. Pay attention to the build version of your JDK because some later builds are fixed as described in JDK-8256818.
- ReplaceText with multiple concurrency tasks can result in data corruption
- ReplaceText, when scheduled to run with multiple Concurrent Tasks, and using a Replacement Strategy of "Regular Expression" or "Literal Replace" can result in content being corrupted.
- NiFi Registry start issue
-
When you upgrade CFM, NiFi Registry might fail during the start with the following error message:
Caused by: org.xml.sax.SAXParseException: cvc-complex-type.2.4.b: The content of element 'providers' is not complete. One of '{eventHookProvider, extensionBundlePersistenceProvider}' is expected.To resolve this issue:- Go to the
NiFi Registry Advanced Configuration Snippet (Safety Valve)section in Cloudera Manager for staging/providers.xml. - Click View as XML and paste the following configuration in the
template:
<property> <name>xml.providers.extensionBundlePersistenceProvider.file-bundle-provider.class</name> <value>org.apache.nifi.registry.provider.extension.FileSystemBundlePersistenceProvider</value> </property> <property> <name>xml.providers.extensionBundlePersistenceProvider.file-bundle-provider.property.Extension Bundle Storage Directory</name> <value>${nifi.registry.working.directory}/extension_bundles</value> </property>
- Go to the
- NiFi start issue
- If the master key password or LDAP manager password contains a
$character, Cloudera Manager will fail to start NiFi. The following image shows the error messsage: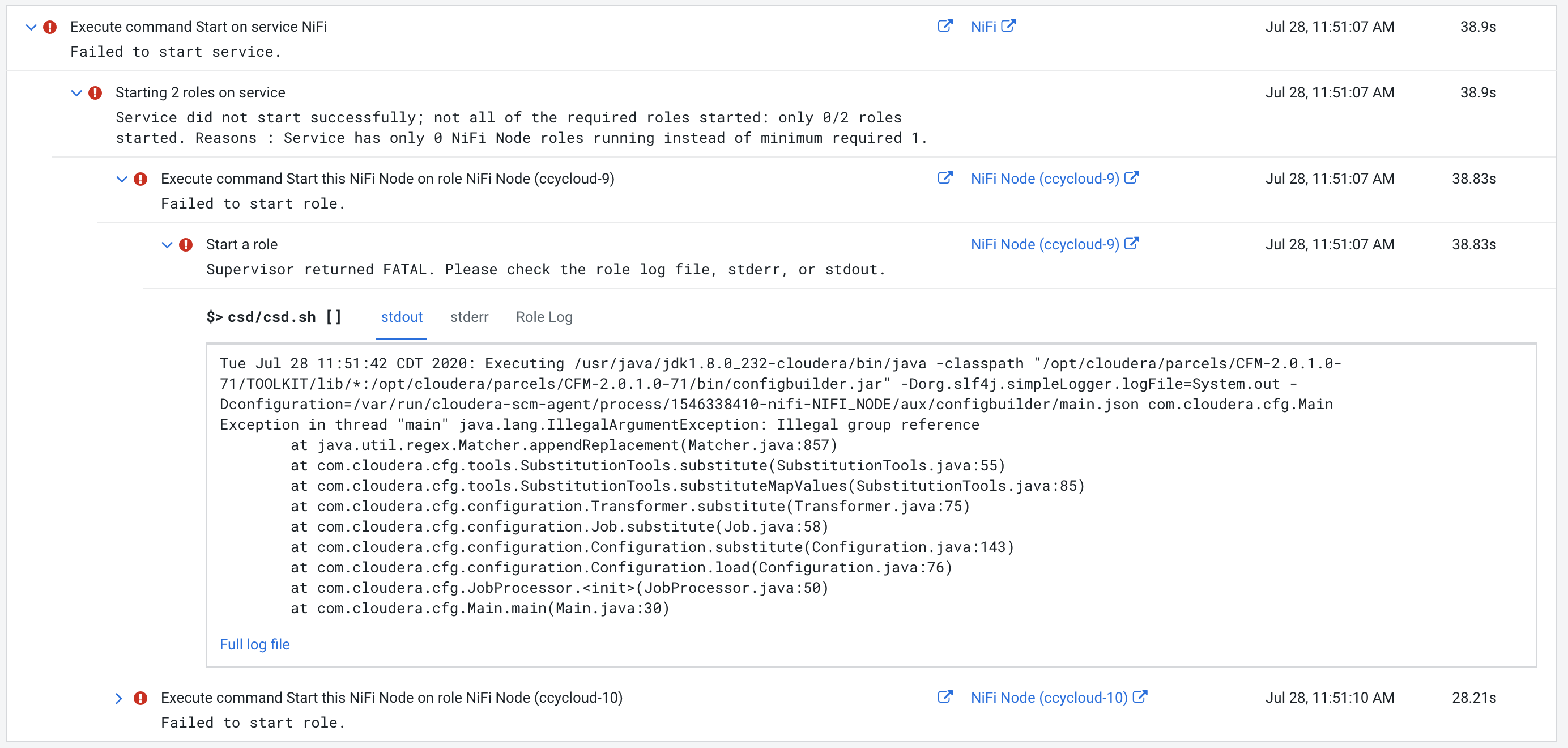
- Base cluster and compute cluster names must not have white space
- When you create your base cluster or compute cluster, ensure that the cluster name does not contain any white space.
- Ranger audits for NiFi and NiFi Registry
- After you install NiFi and NiFi Registry, complete the following steps to ensure that Ranger audits are stored correctly in HDFS:
- Ranger High Availability
- If you have multiple instances of the Ranger Admin service and if the
ranger_rest_url parameter contains a comma separated list of URLs
(i.e. the Ranger instances are not behind a load balancer), then NiFi and NiFi Registry
will not start and the following error appears in Cloudera Manager:
Traceback (most recent call last): File "/var/run/cloudera-scm-agent/process/1546471613-nifiregistry-NIFI_REGISTRY_SERVER/scripts/ranger.py", line 683, in <module> main() File "/var/run/cloudera-scm-agent/process/1546471613-nifiregistry-NIFI_REGISTRY_SERVER/scripts/ranger.py", line 633, in main keytab=args.keytab, principal=args.principal) File "/var/run/cloudera-scm-agent/process/1546471613-nifiregistry-NIFI_REGISTRY_SERVER/scripts/ranger.py", line 302, in create_ranger_repository _create() File "/var/run/cloudera-scm-agent/process/1546471613-nifiregistry-NIFI_REGISTRY_SERVER/scripts/ranger.py", line 291, in _create ranger_service_name, code, out)) Exception: Failed to create ranger repository 'Lower Environment_nifiregistry', response code is '404', output is ''.
Technical Service Bulletins
- TSB 2022-580: NiFi Processors cannot write to content repository
- If the content repository disk is filled more than 50% (or any other value that is set
in
nifi.propertiesfornifi.content.repository.archive.max.usage.percentage), and if there is no data in the content repository archive, the following warning message can be found in the logs: "Unable to write flowfile content to content repository container default due to archive file size constraints; waiting for archive cleanup". This would block the processors and no more data is processed.This appears to only happen if there is already data in the content repository on startup that needs to be archived, or if the following message is logged: “Found unknown file XYZ in the File System Repository; archiving file”.
- Upstream JIRA
- Knowledge article
- For the latest update on this issue see the corresponding Knowledge article: TSB 2022-580: NiFi Processors cannot write to content repository
- TSB 2022-589: CVE-2022-33140 Apache NiFi ShellUserGroupProvider Vulnerability
- The optional ShellUserGroupProvider in Apache NiFi 1.10.0 to 1.16.2 and Apache NiFi Registry 0.6.0 to 1.16.2 does not neutralize arguments for group resolution commands, allowing injection of operating system commands on Linux and macOS platforms. The ShellUserGroupProvider is not included in the default configuration. Command injection requires ShellUserGroupProvider to be one of the enabled User Group Providers (UGP) in the Authorizers configuration. Command injection also requires an authenticated user with elevated privileges. Apache NiFi requires an authenticated user with authorization to modify access policies in order to execute the command. Apache NiFi Registry requires an authenticated user with authorization to read user groups in order to execute the command. The resolution removes command formatting based on user-provided arguments.
- Knowledge article
- For the latest update on this issue see the corresponding Knowledge article: TSB 2022-589: CVE-2022-33140 Apache NiFi ShellUserGroupProvider Vulnerability


