Additional requirements for Atlas with Ranger and Kerberos
Currently additional configuration steps are required for Atlas with Ranger and in Kerberized environments.
Additional Requirements for Atlas with Ranger
When Atlas is used with Ranger, perform the following additional configuration steps:
 | Important |
|---|---|
These steps are not required for Ambari-2.4.x and higher
versions. For Ambari-2.4.x and higher, these steps will be performed automatically
when Atlas is restarted. |
-
Create the following HBase policy:
-
table: atlas_titan, ATLAS_ENTITY_AUDIT_EVENTS
user: atlas
permission: Read, Write, Create, Admin
-
-
Create following Kafka policies:
-
topic=ATLAS_HOOK
permission=publish, create; group=public
permission=consume, create; user=atlas (for non-kerberized environments, set group=public)
-
topic=ATLAS_ENTITIES
permission=publish, create; user=atlas (for non-kerberized environments, set group=public)
permission=consume, create; group=public
-
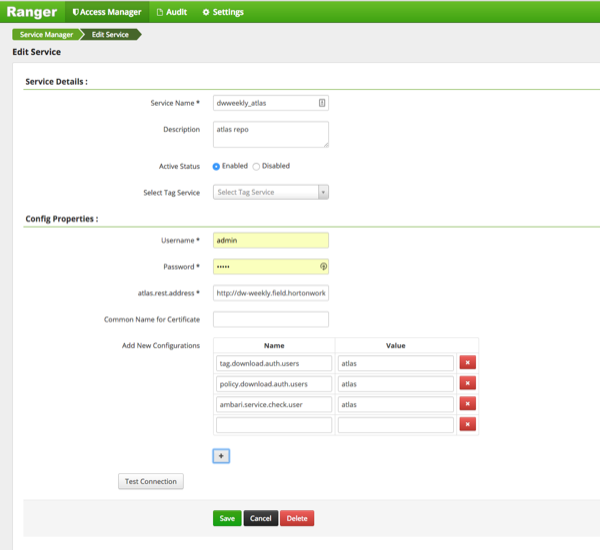
You should also ensure that an Atlas service is created in Ranger, and that the Atlas service includes the following configuration properties:
Table 2.4. Ranger Atlas Service Kerberos Properties
| Property | Value |
|---|---|
| tag.download.auth.users | atlas |
| policy.download.auth.users | atlas |
| ambari.service.check.user | atlas |
 | Note |
|---|---|
If the Ranger Atlas service is not created after enabling the plugin and
restarting Atlas, that indicates that either there is already a policy JSON on
the Atlas host (in the
/etc/ranger/<service_name>/policycache/ directory),
or Ambari was unable to connect to Ranger Admin during the Atlas restart. The
solution for the first issue is to delete or move the
policycache file, then restart Atlas.
|
Additional Requirements for Atlas with Kerberos without Ranger
When Atlas is used in a Kerberized environment without Ranger, perform the following additional configuration steps:
-
Start the HBase shell with the user identity of the HBase admin user ('hbase')
-
Execute the following command in HBase shell, to enable Atlas to create necessary HBase tables:
-
grant 'atlas', 'RWXCA'
-
-
Start (or restart) Atlas, so that Atlas would create above HBase tables
-
Execute the following commands in HBase shell, to enable Atlas to access necessary HBase tables:
-
grant 'atlas', 'RWXCA', 'atlas_titan'
-
grant 'atlas', 'RWXCA', 'ATLAS_ENTITY_AUDIT_EVENTS'
-
-
Kafka – To grant permissions to a Kafka topic, run the following commands as the Kafka user:
/usr/hdp/current/kafka-broker/bin/kafka-acls.sh --authorizer kafka.security.auth.SimpleAclAuthorizer --authorizer-properties zookeeper.connect=hostname:2181 --add --operation All --allow-principal User:atlas --topic ATLAS_HOOK /usr/hdp/current/kafka-broker/bin/kafka-acls.sh --authorizer kafka.security.auth.SimpleAclAuthorizer --authorizer-properties zookeeper.connect=hostname:2181 --add --operation All --allow-principal User:atlas --topic ATLAS_ENTITIES