Application ACL evaluation
The better you understand how YARN ACLs are evaluated, the more prepared you will be to define and configure the various YARN ACLs available to you.
For example, if you enable user access in Administrator ACLs, then you must be aware that user may have access to/see sensitive data, and should plan accordingly. So if you are the administrator for an entire cluster, you also have access to the logs for running applications, which means you can view sensitive information in those logs associated with running the application.
Best Practice: A best practice for securing an environment is to set the YARN Admin ACL to include a limited set of users and or groups.
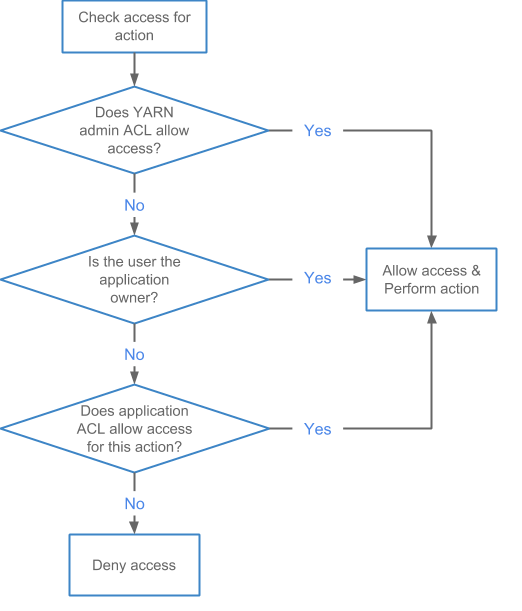
The following diagram shows the evaluation flow for Application ACLs:
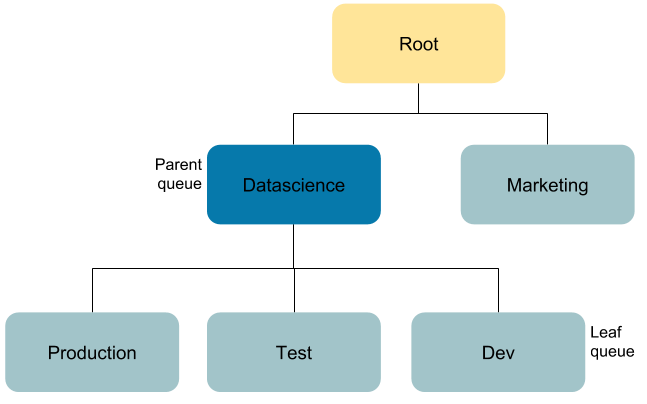
The following diagram shows a sample queue structure, starting with leaf queues on the bottom, up to root queue at the top:
Example: Stopping an application in the "Production" queue
Provide the privilege to a user to stop an application in a specific queue.
application_1536220066338_0001 running in the
queue "Production":- Application owner: John
- "Datascience" queue administrator: Jane
- YARN cluster administrator: Bob
In this use case, John attempts to stop the application, which is allowed because he is the application owner.
Working as the queue administrator, Jane attempts to stop a job in the queue "Production", which she can do as the queue administrator of the parent queue.
Bob is the YARN cluster administrator and he is also listed as a user in the Admin ACL. He attempts to stop the job for which he is not the owner, but because he is the YARN cluster administrator, he can stop the job.
Example: Moving the application and viewing the log in the "Test" queue
Provide the privileges to a user to move application between queues and to view a log in a specific queue.
application_1536220066338_0002 running in the
queue "Test":- Application owner: John
- "Marketing" and "Dev" queue administrator: Jane
- Jane has log view rights via the
mapreduce.job.acl-view-jobACL - YARN cluster administrator: Bob
In this use case, John attempts to view the logs for his job, which is allowed because he is the application owner.
Jane attempts to access application_1536220066338_0002 in the queue "Test" to move the application to the
"Marketing" queue. She is denied access to the "Test" queue via the queue ACLs–so she cannot
submit to or administer the queue "Test". She is also unable to stop a job running in queue
"Test". She then attempts to access the logs for application_1536220066338_0002 and is allowed access via the mapreduce.job.acl-view-job ACL.
application_1536220066338_0002 in the queue "Test" to move the application to the
"Marketing" queue. As the YARN cluster administrator, he has access to all queues and can move
the application.


