Installing Ranger KMS with Key Trustee Server
Use these steps to install Ranger KMS with Key Trustee Server as the backing key store.
- Apache Ranger must be installed and running.
- Kerberos must be enabled.
- TLS/SSL should be enabled.
- You must install Key Trustee Server before installing Ranger KMS with Key Trustee Server. See Installing Cloudera Navigator Key Trustee Server.
- Ranger KMS with Key Trustee Server must be installed on a separate host than Key Trustee Server.
-
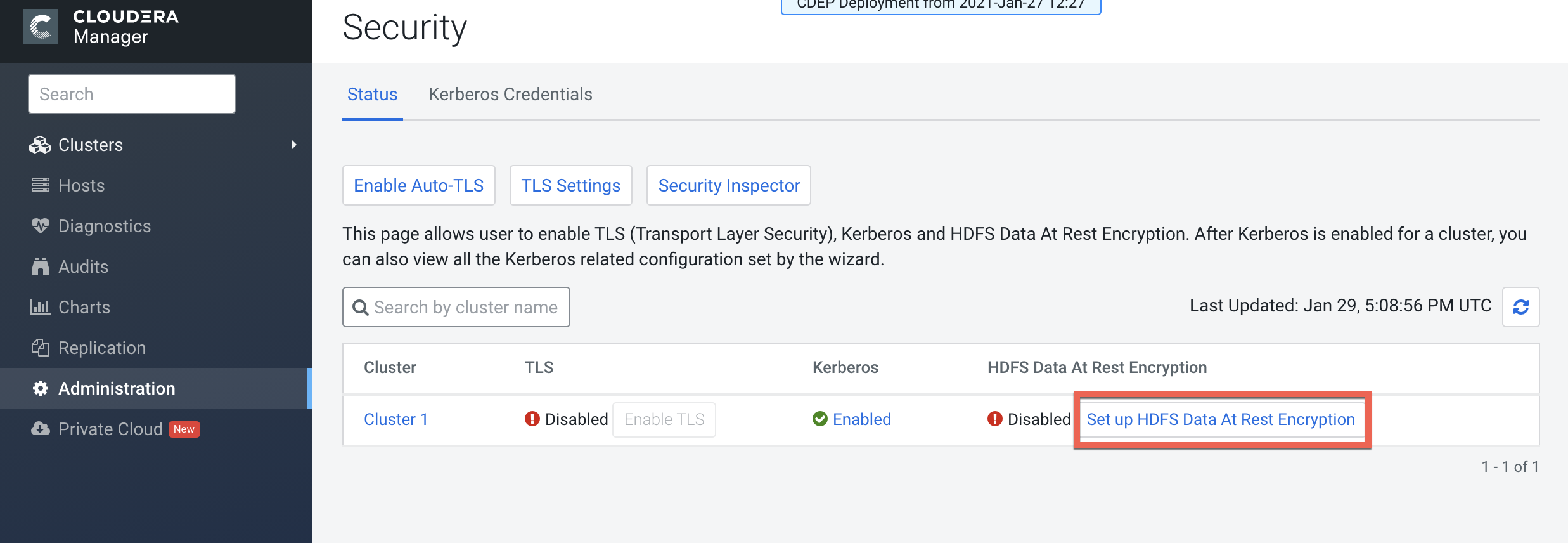
In Cloudera Manager, select Administration > Security, then click Set up HDFS
Data At Rest Encryption.
-
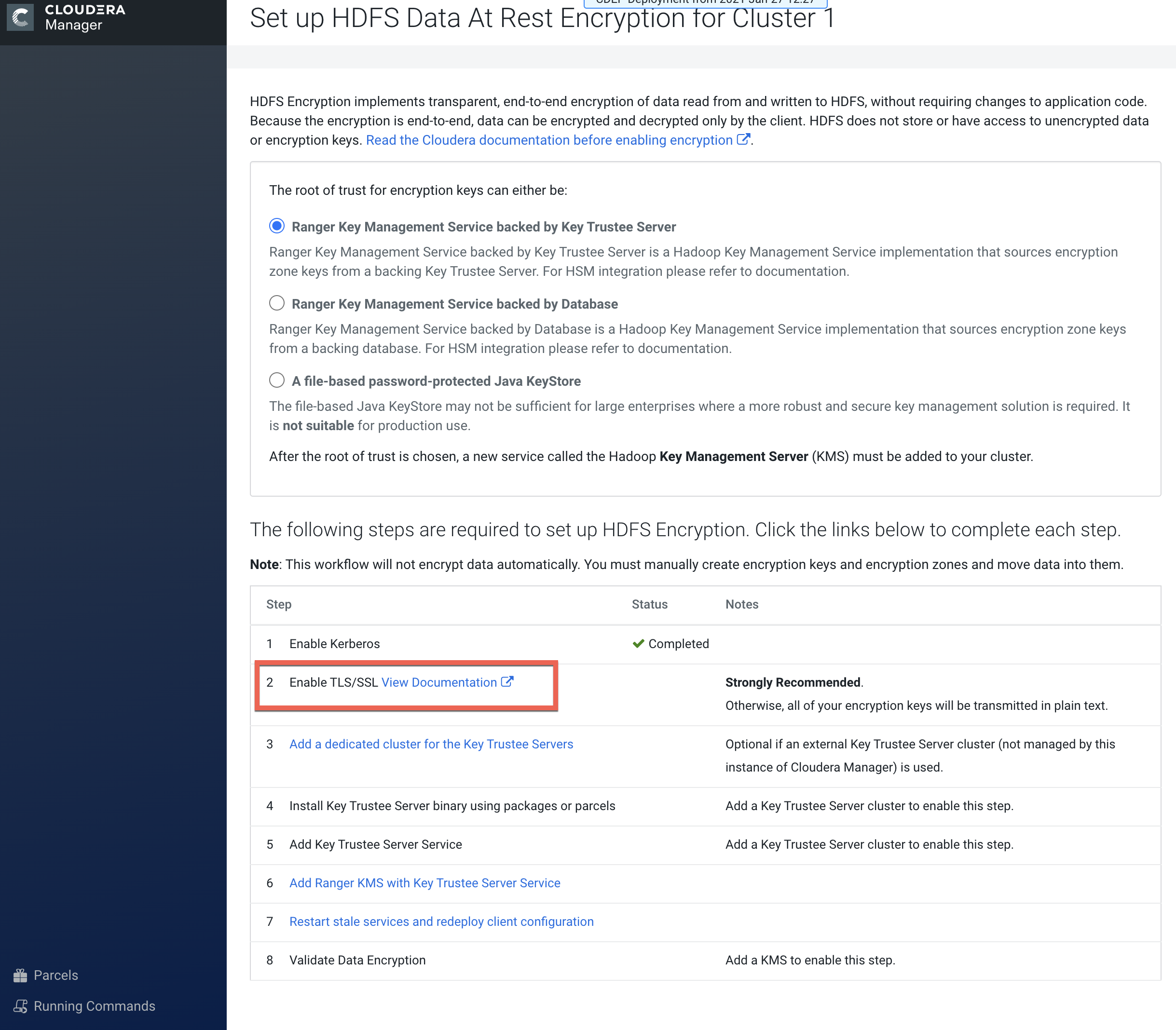
On the Set up HDFS Data At Rest Encryption page, select Ranger Key Management
Service backed by Key Trustee Server. The setup steps are listed at the bottom of
the page. In the following image, Kerberos has been enabled, so the next step is to enable TLS/SSL.
-
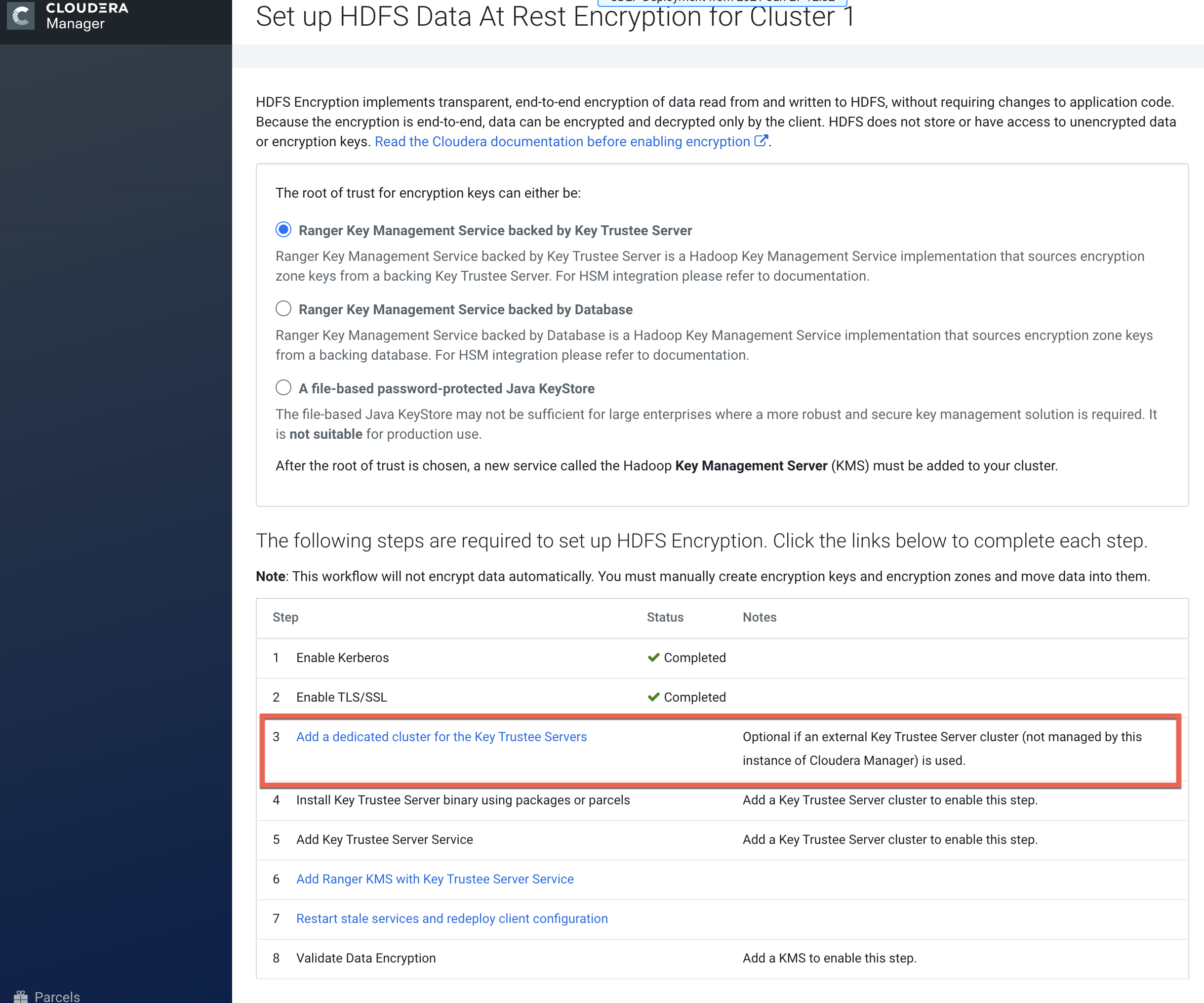
[OPTIONAL] After TLS has been enabled, you can optionally add an external cluster for
the Key Trustee servers.
-
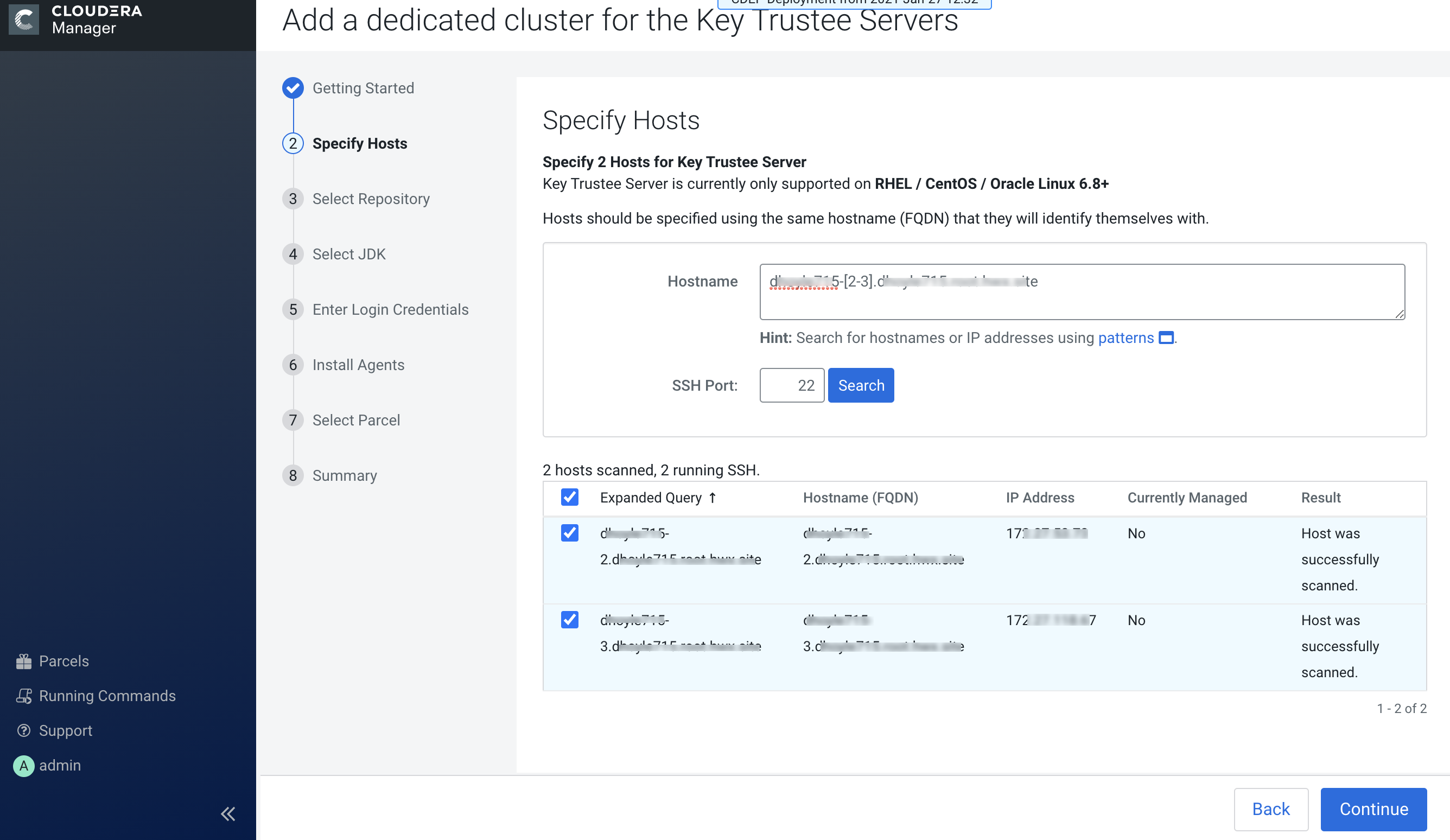
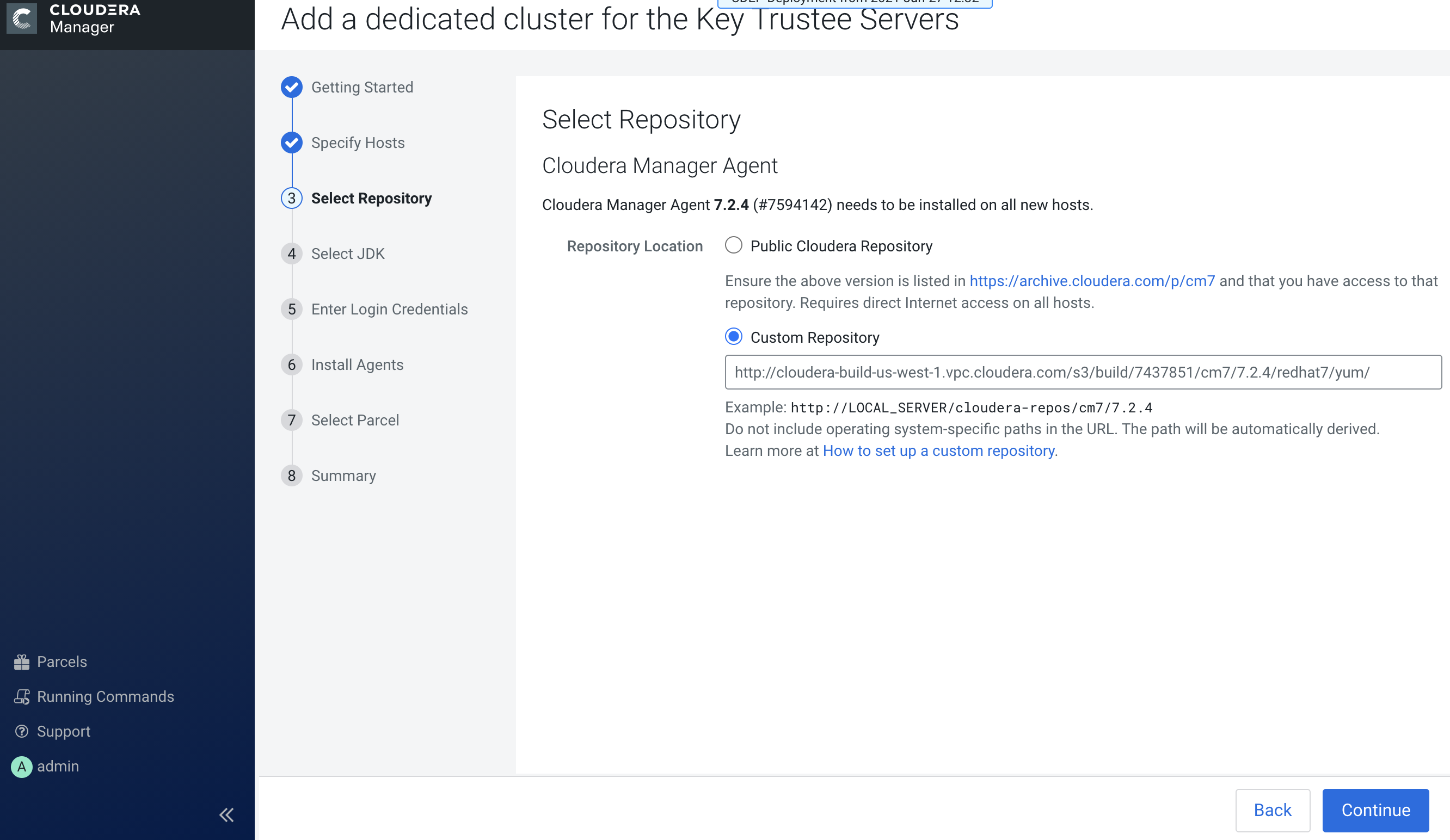
Click Add a dedicated cluster for the Key Trustee Servers, then use the
wizard to set up a Cloudera Manager agent and Key Trustee server parcel that is
compatible with the activated CDPDC parcel registered with CDP Private Cloud
base.
- Add Key Trustee Server Service – Use the Cloudera Manager wizard to select each active and passive Passive Key Trustee Server. Synchronize their Server Private Keys followed by starting them.
-
Click Add a dedicated cluster for the Key Trustee Servers, then use the
wizard to set up a Cloudera Manager agent and Key Trustee server parcel that is
compatible with the activated CDPDC parcel registered with CDP Private Cloud
base.
-
Click Add Ranger KMS with Key Trustee Server Service, then click
Continue.
-
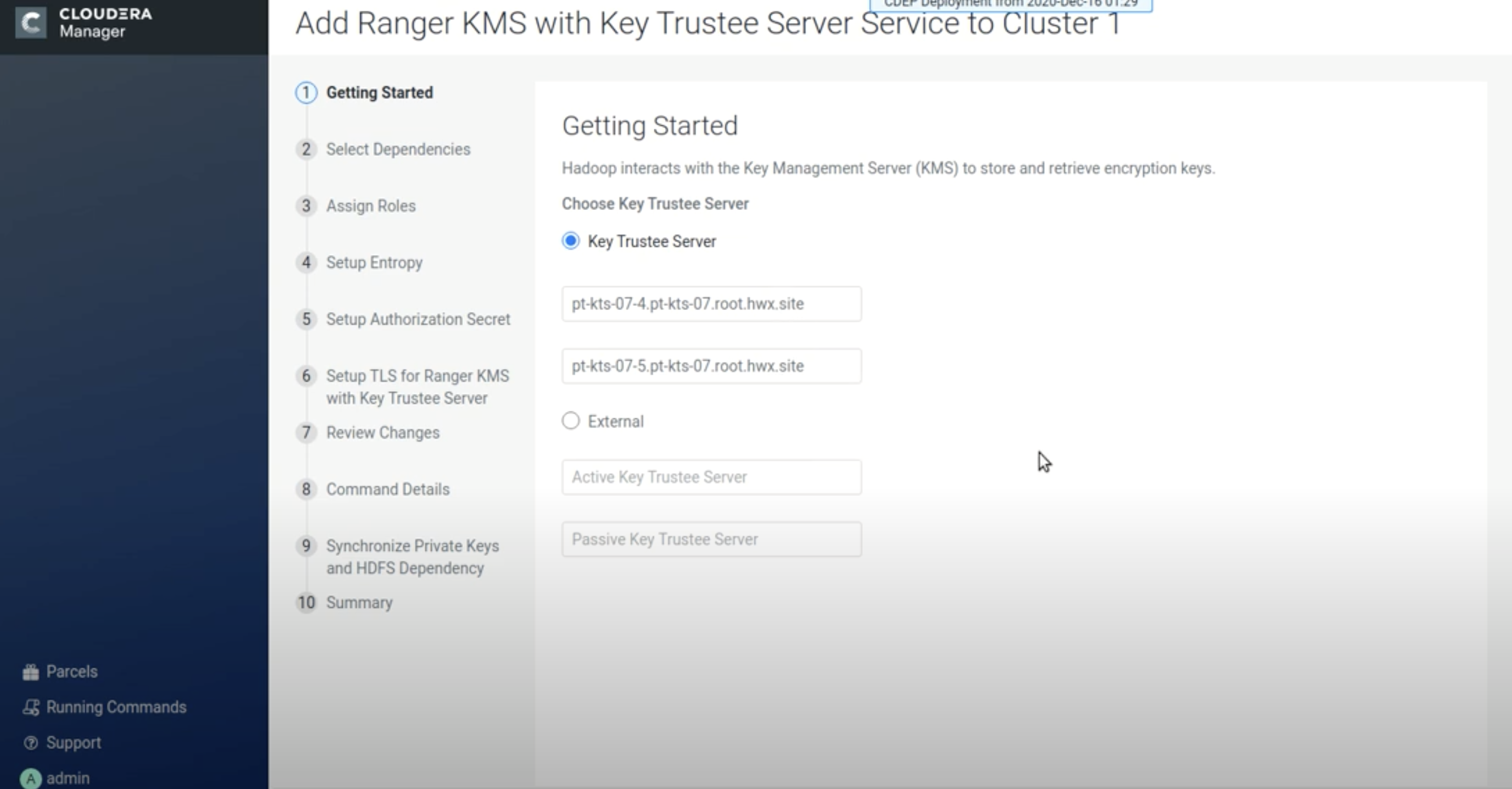
On the Getting Started page, the existing active and passive Key Trustee Server
instances are selected by default. You can also specify an external Key Trustee
Server.
-
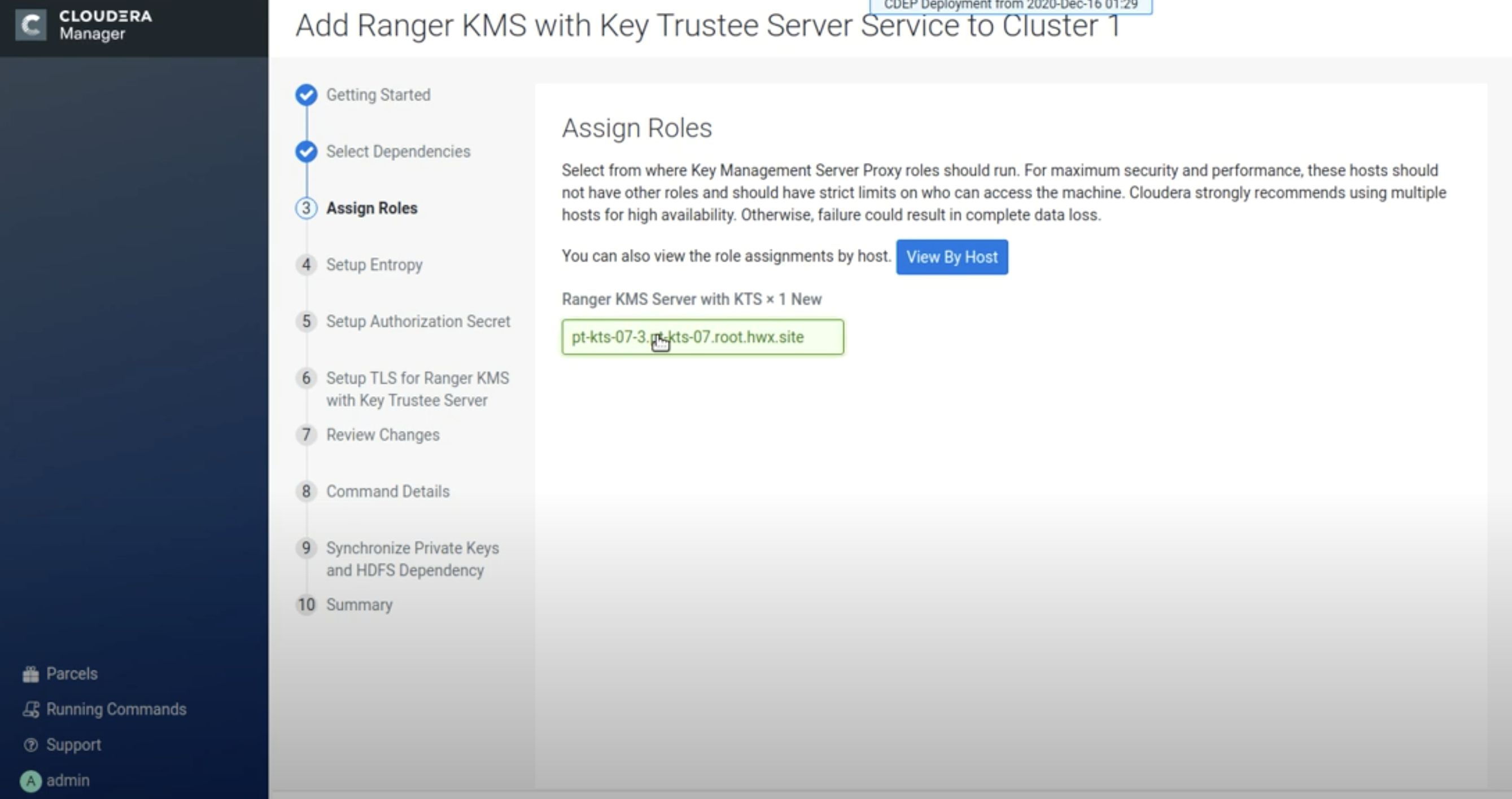
On the Assign Roles page, specify a host where Ranger KMS with Key Trustee Server
will be installed, then click Continue.
-
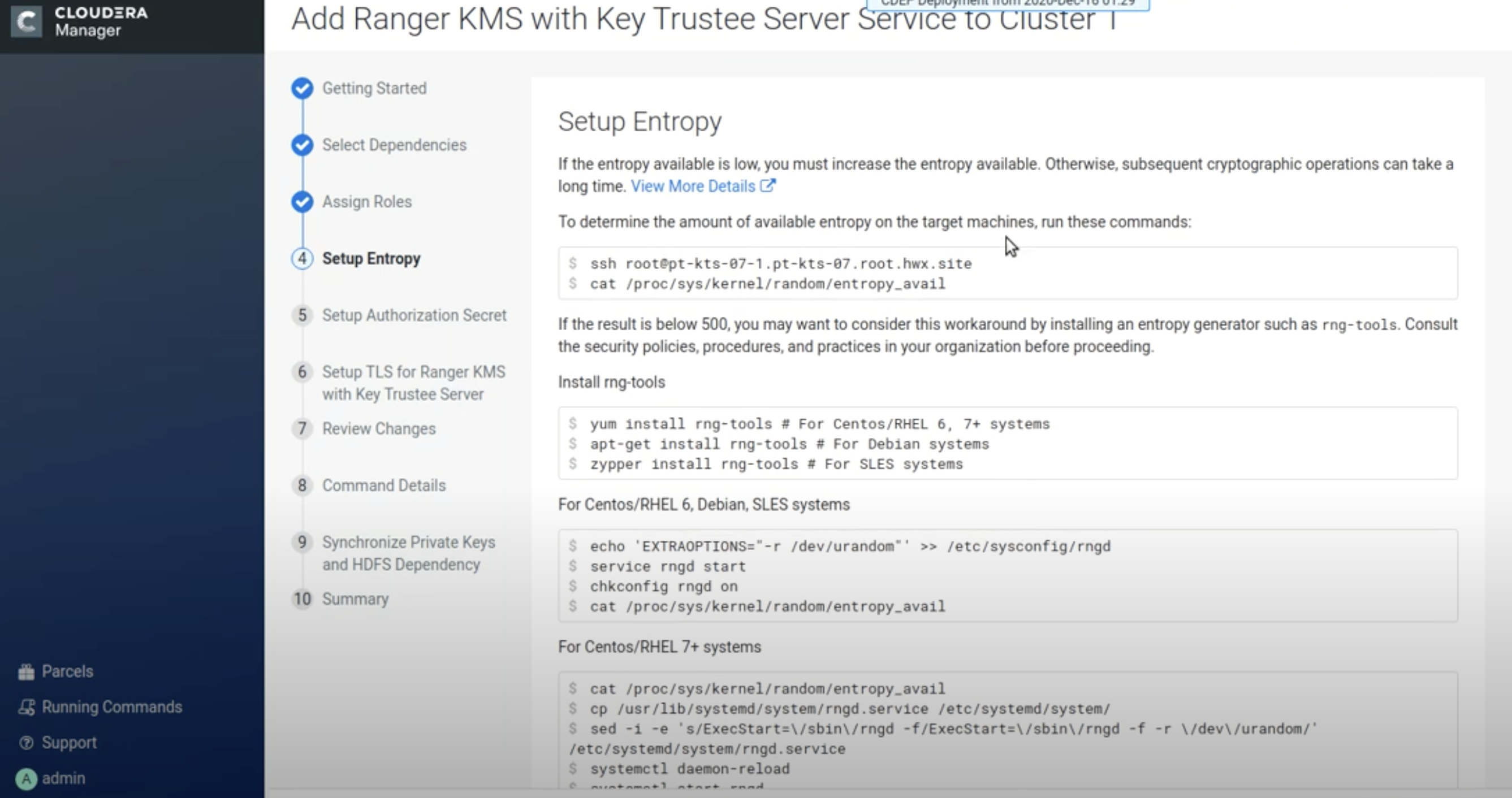
On the Setup Entropy page, follow the instructions and perform any required steps,
then click Continue.
-
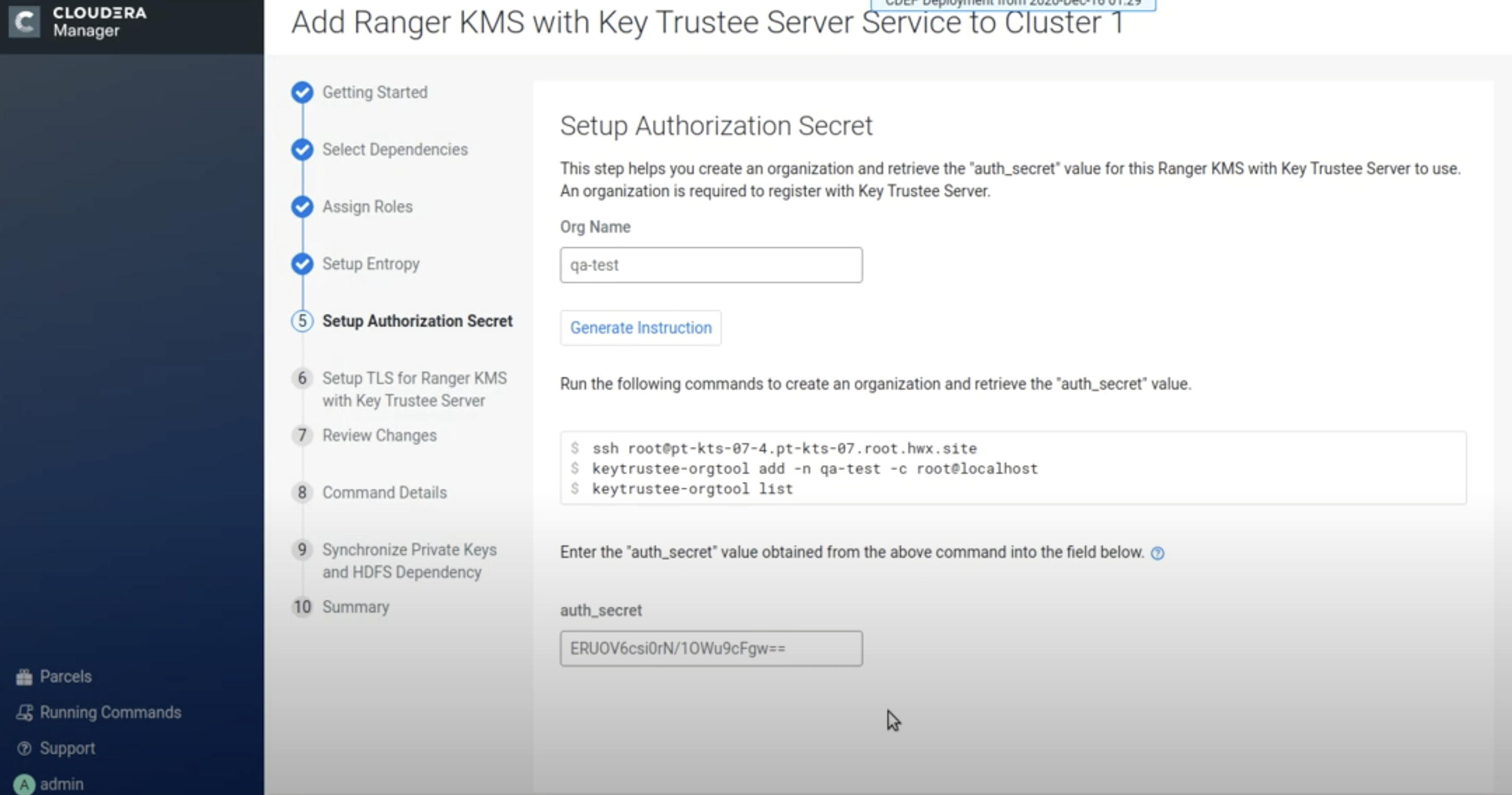
On the Setup Authorization Secret page, specify an Org Name, then click Generate
Instruction. Follow the instructions and enter the authorization secret in the
auth_secret box, then click Continue.
-
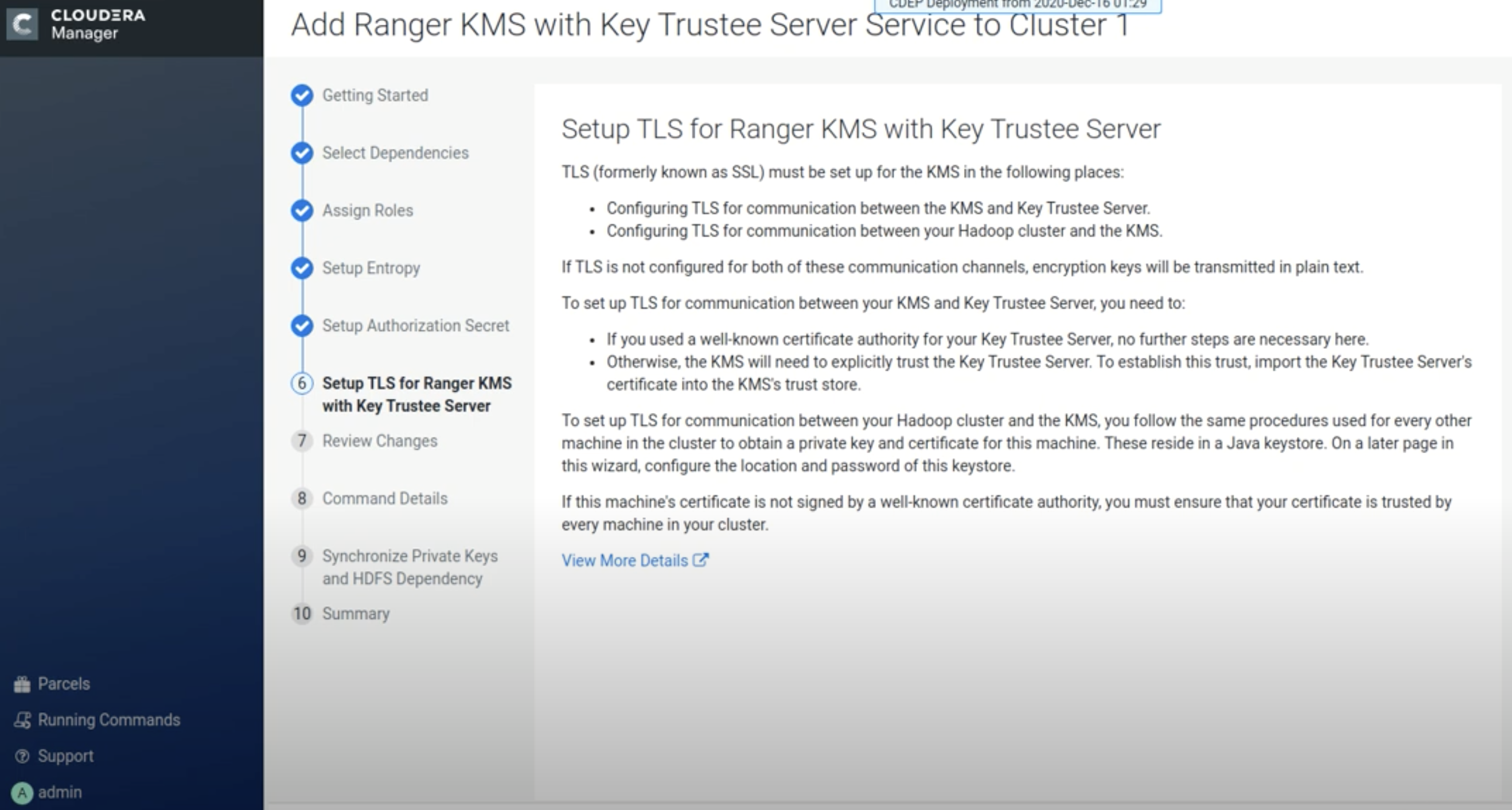
On the Setup TLS for Ranger KMS with Key Trustee Server page, click
Continue.
-
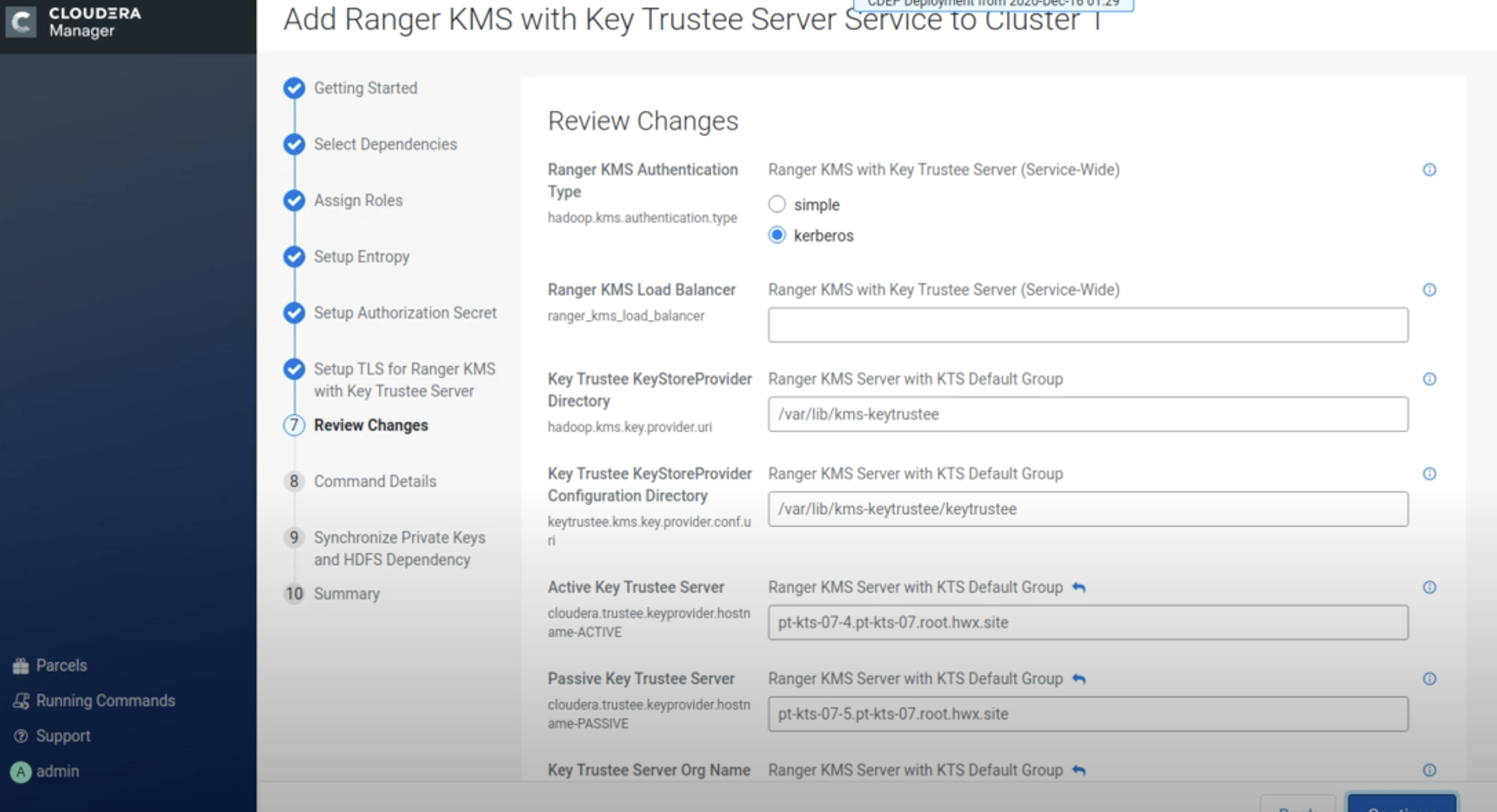
On the Review Changes page, review the configuration settings, then click
Continue.
-
On the Command Details page, select run options, then click Continue.
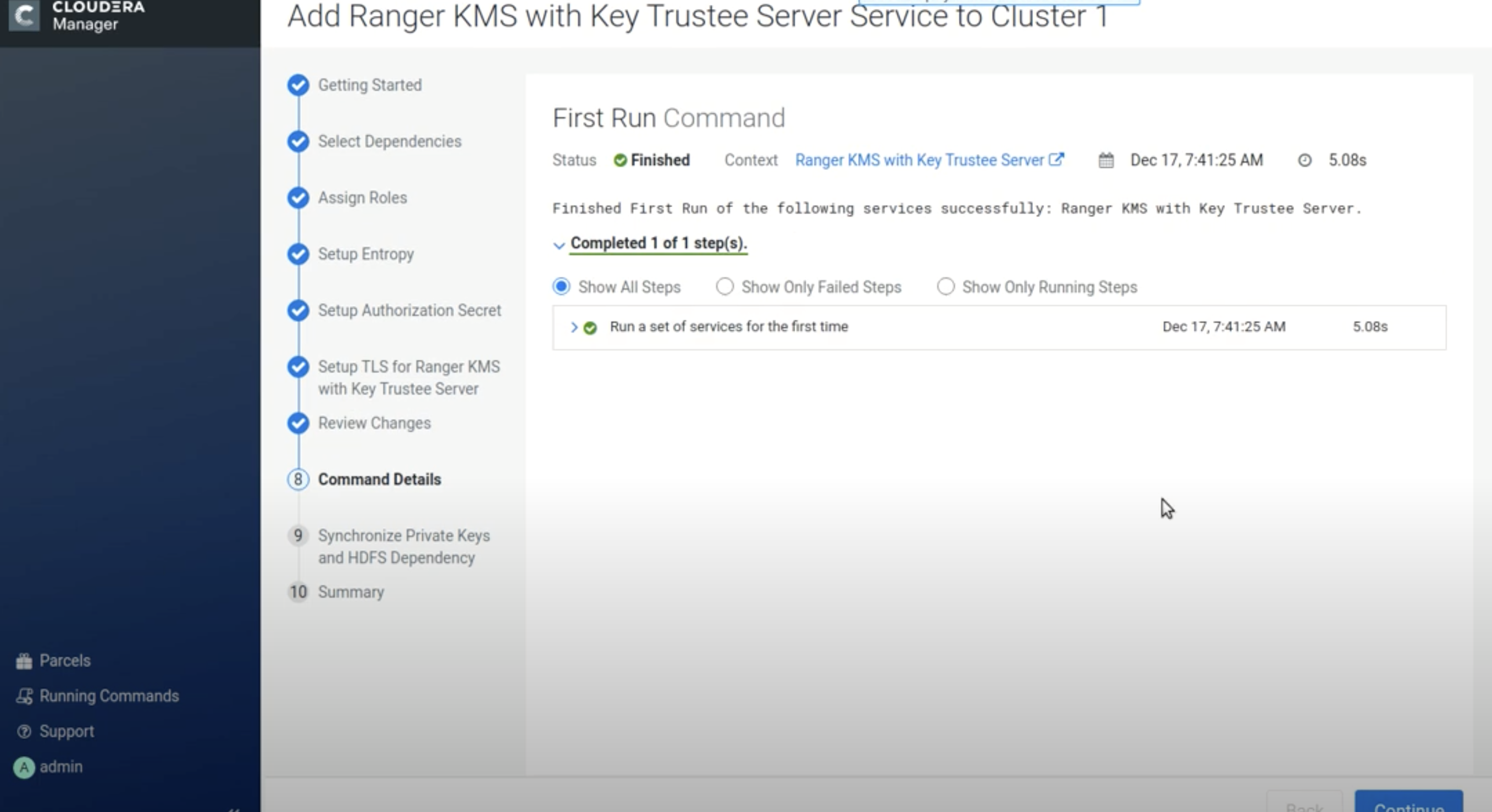
-
On the Summary page, click Finish.
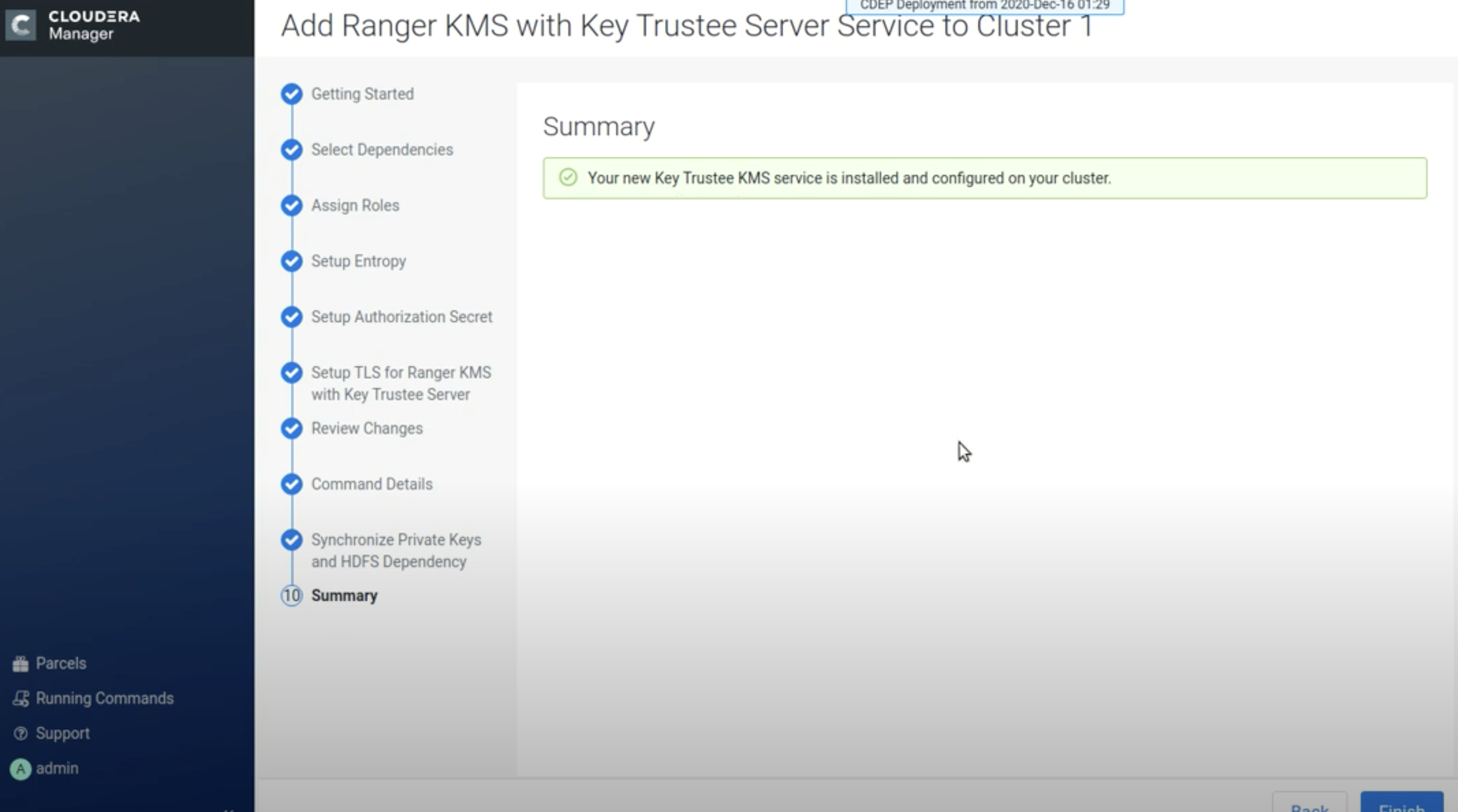
-
On the Getting Started page, the existing active and passive Key Trustee Server
instances are selected by default. You can also specify an external Key Trustee
Server.
-
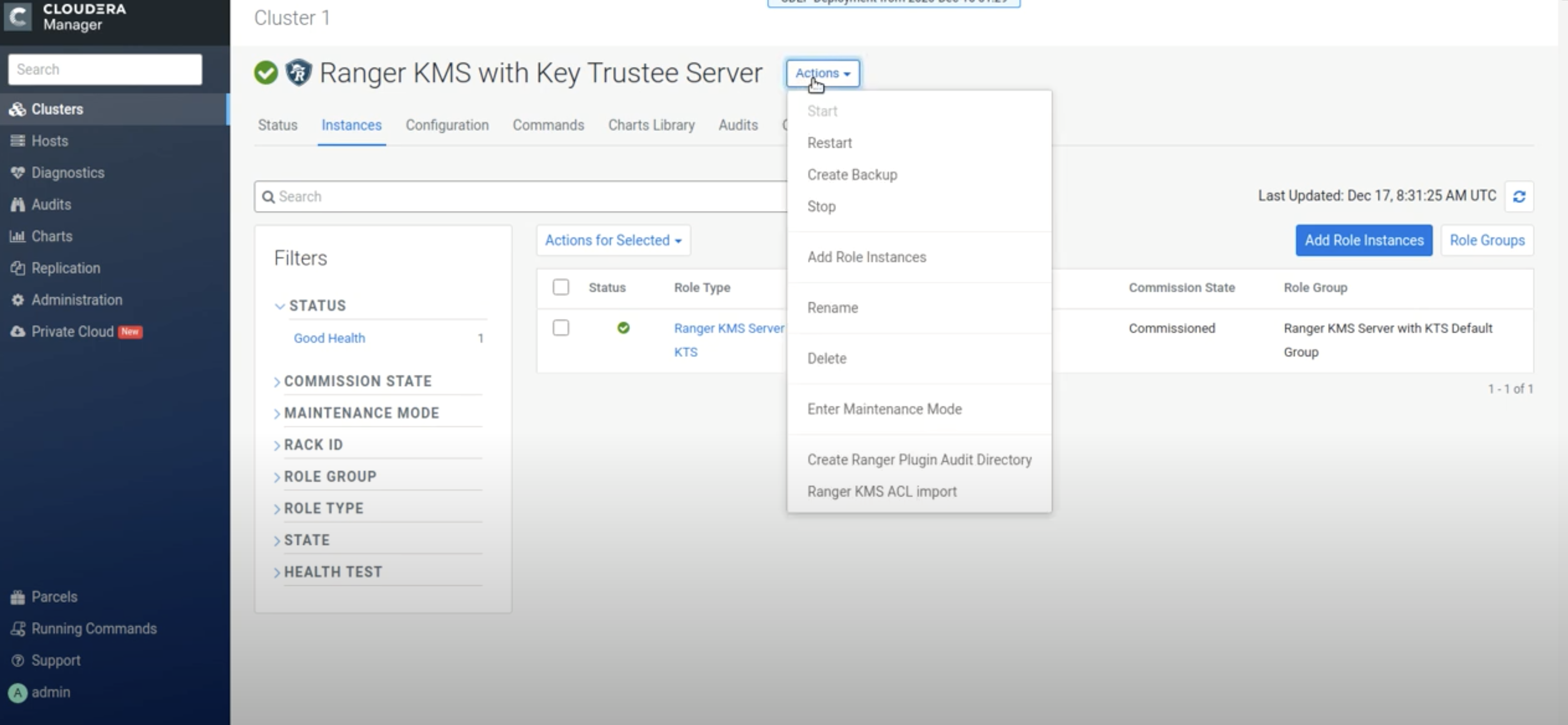
The Ranger KMS with Key Trustee Server service appears in the Cloudera Manager cluster
components list. If Ranger KMS with Key Trustee Server was not started by the installation
wizard, you can start the service by clicking Actions > Start in the Ranger KMS
with Key Trustee Server service.
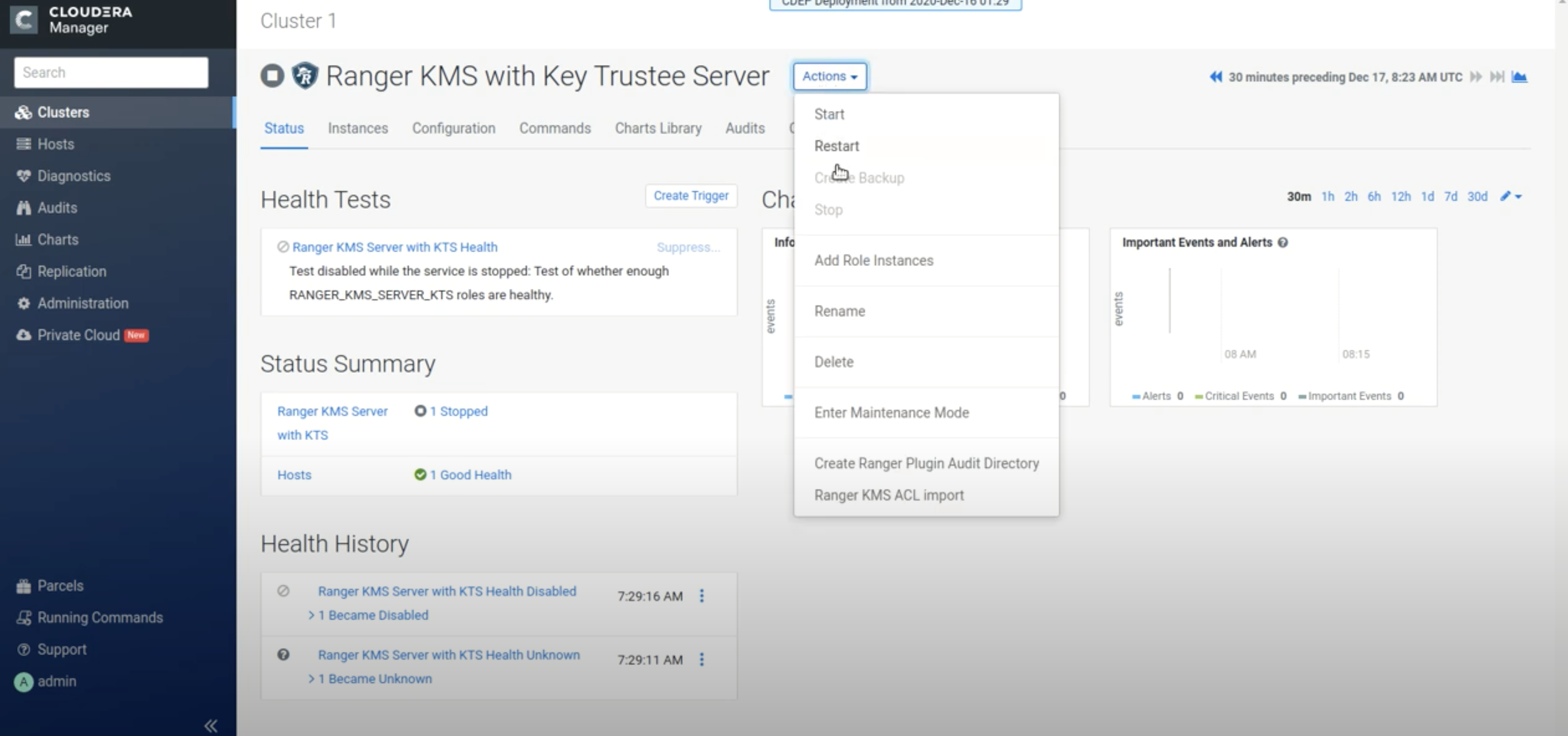
-
In Cloudera Manager, select the Ranger service, click Ranger Admin Web UI, then
log in as the Ranger KMS user (the default credentials are keyadmin/admin123). Click the
Edit icon for the cm_kms service, then update the KMS URL property.
- Use the following format:
kms://http@<kms_host>:<kms_port>/kms - Change the host name from localhost to the KMS host name. The default port is
9292. For example:
kms://http@kms_host:9292/kms - If SSL is enabled, use
httpsand port 9494. For example:kms://https@kms_host:9494/kms
Click Save to save your changes.
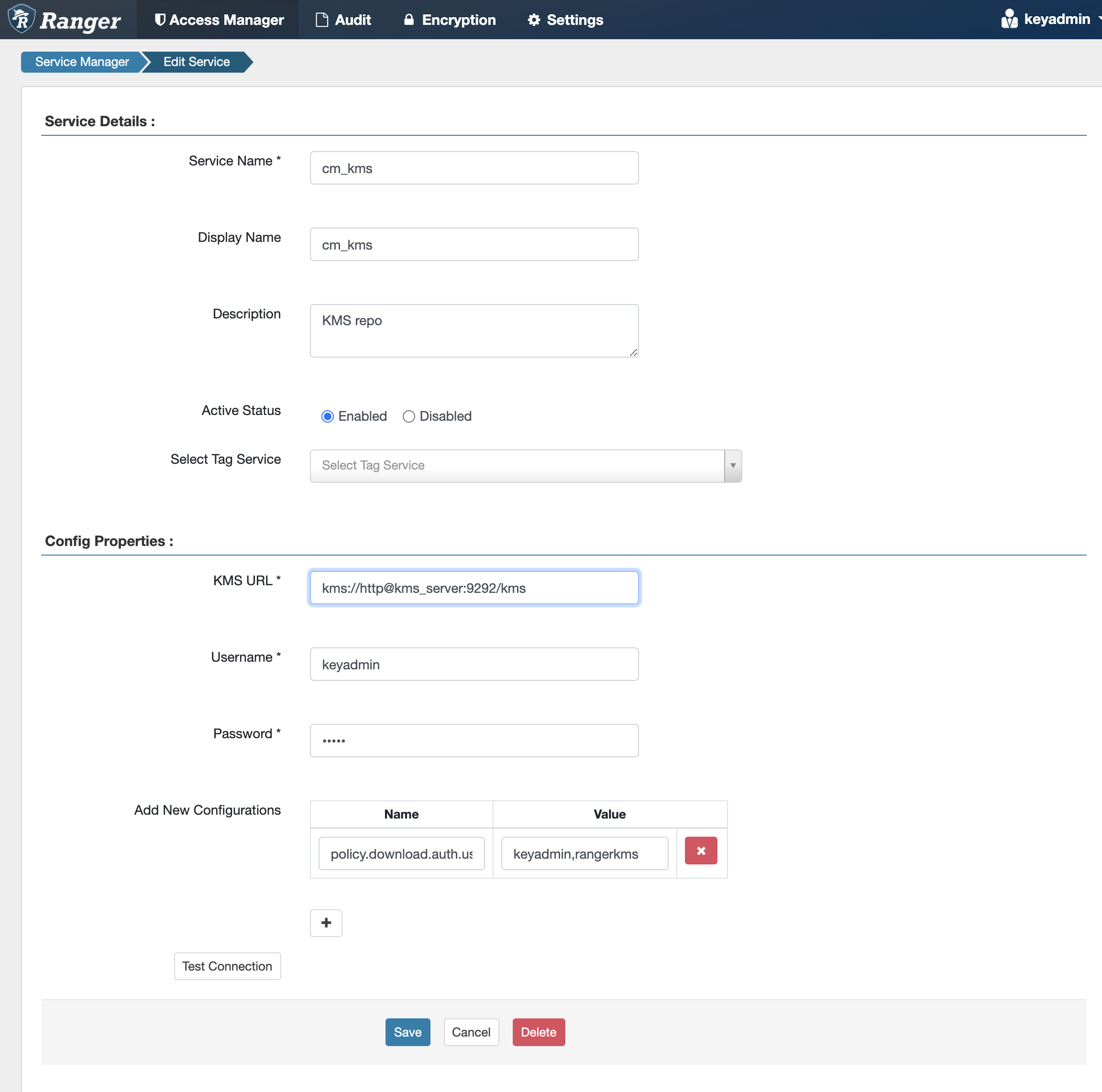
- Use the following format:
- In Cloudera Manager, restart all services with stale configurations.
-
In Cloudera Manager click the Ranger KMS with Key Trustee Server service, then select
Actions > Create Ranger Plugin Audit Directory. The Ranger KMS with Key Trustee
Server service is now ready to use and you should be able to validate Ranger KMS policy
enforcement.