Encryption Zones and Keys
HDFS transparent encryption introduces the concept of an encryption zone (EZ), which is a directory in HDFS whose contents will be automatically encrypted on write and decrypted on read.
Encryption zones always start off as empty directories, and tools such as distcp
with the -skipcrccheck -update flags can be used to add data to a zone.
(These flags are required because encryption zones are being used.) Every file and
subdirectory copied to an encryption zone will be encrypted.
Each encryption zone is associated with a key (EZ Key) specified by the key administrator when the zone is created. EZ keys are stored on a backing keystore external to HDFS. Each file within an encryption zone has its own encryption key, called the Data Encryption Key (DEK). These DEKs are encrypted with their respective encryption zone's EZ key, to form an Encrypted Data Encryption Key (EDEK).
The following diagram illustrates how encryption zone keys (EZ keys), data encryption keys (DEKs), and encrypted data encryption keys (EDEKs) are used to encrypt and decrypt files.
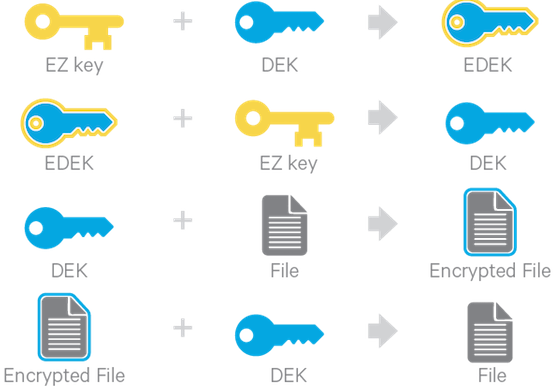
EDEKs are stored persistently on the NameNode as part of each file's metadata, using HDFS
extended attributes. EDEKs can be safely stored and handled by the NameNode because the
hdfs user does not have access to the EDEK's encryption keys (EZ keys).
Even if HDFS is compromised (for example, by gaining unauthorized access to a superuser
account), a malicious user only gains access to the encrypted text and EDEKs. EZ keys are
controlled by a separate set of permissions on the KMS and the keystore.
An EZ key can have multiple key versions, where each key version has its own distinct key material (that is, the portion of the key used during encryption and decryption). Key rotation is achieved by bumping up the version for an EZ key. Per-file key rotation is then achieved by re-encrypting the file's DEK with the new version of the EZ key to create new EDEKs. HDFS clients can identify an encryption key either by its key name, which returns the latest version of the key, or by a specific key version.


