Integrating Ranger KMS DB with CipherTrust Manager HSM
How to integrate Ranger KMS DB with CipherTrust Manager HSM.
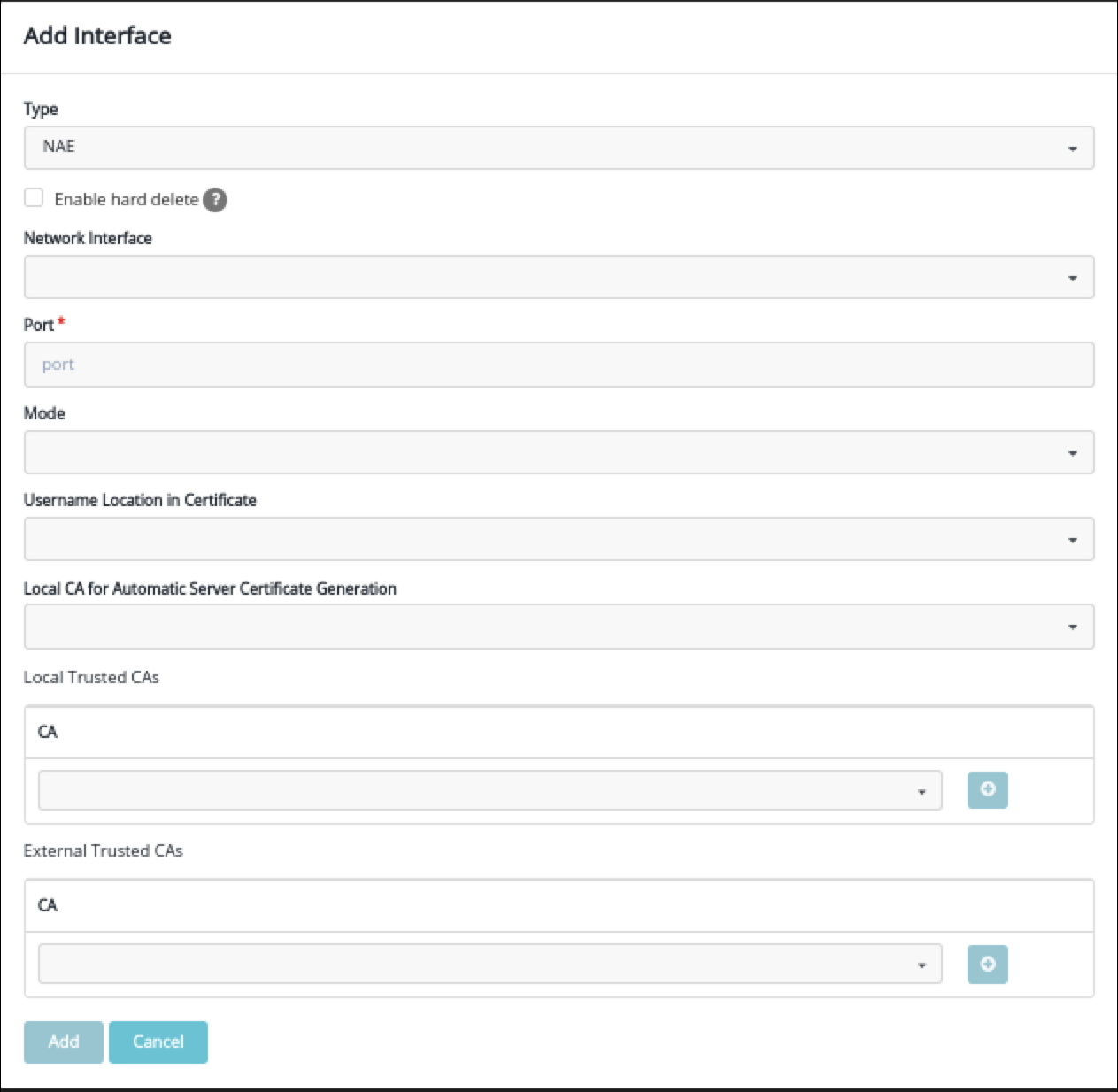
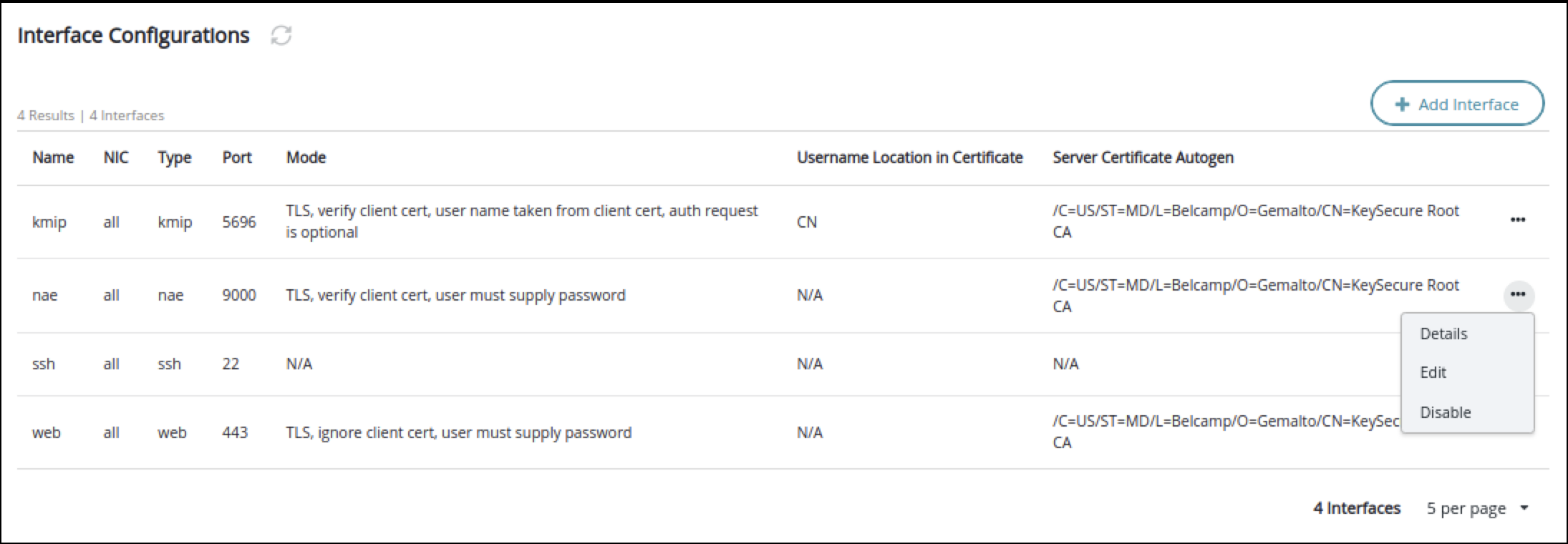
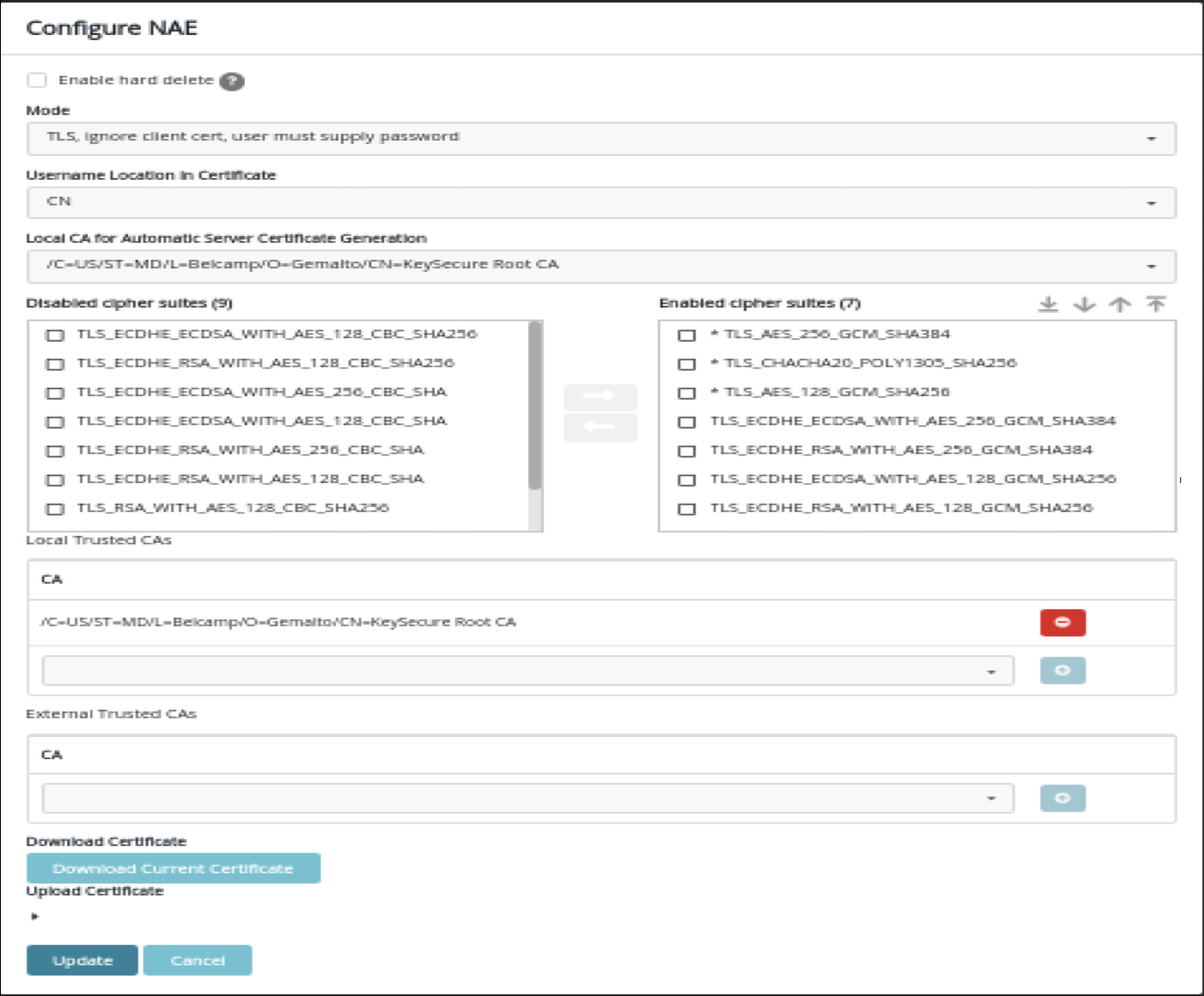
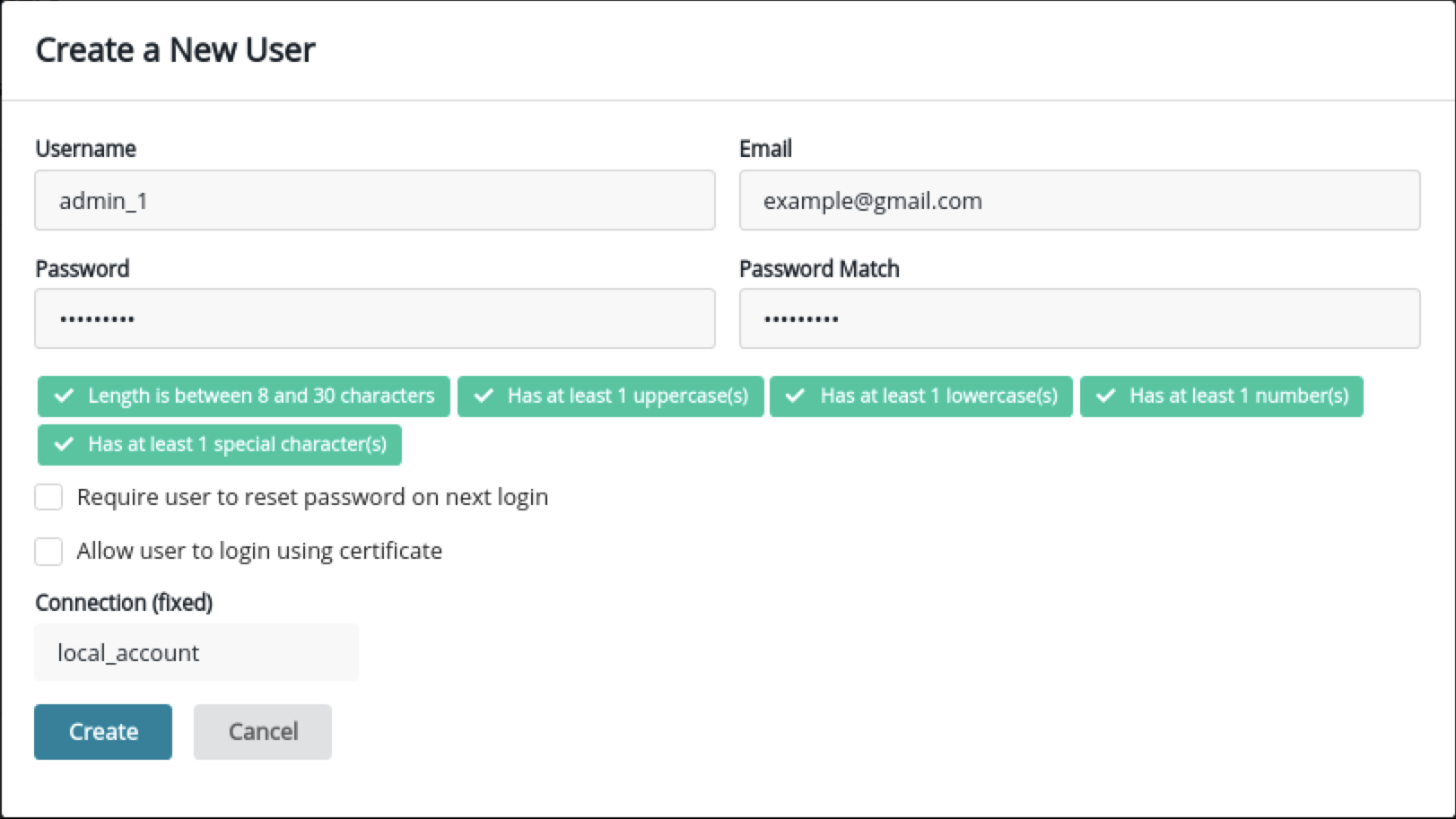
This task describes how to integrate Ranger KMS DB with CipherTrust Manager Hardware Security Module (HSM). This process includes configuring the NAE port in Thales Cipher Trust Manager, configuring Ranger DB KMS to interact with Thales CipherTrust HSM, or, migrating Ranger KMS DB Master Key To CipherTrust Manager HSM, and migrating the master key from CipherTrust Manager HSM to Ranger KMS DB.
- Ensure you have Thales CipherTrust Manger installed in your enivronment.
- Ensure you have Java (jdk1.8.0.232) installed.
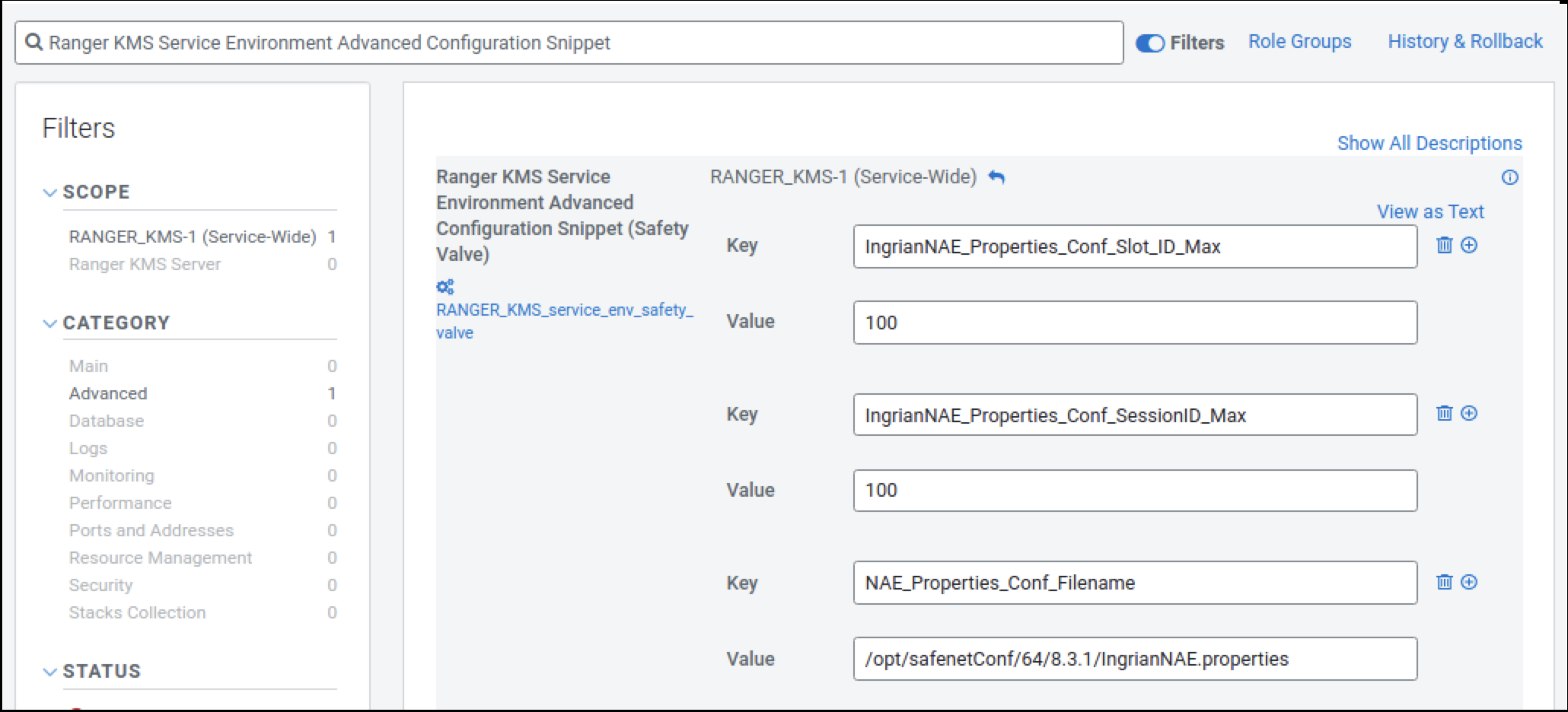
Fresh installation - Configuring Ranger KMS DB to interact with Thales CipherTrust HSM.
These are the steps required to configure Ranger KMS DB to interact with Thales CipherTrust HSM. These steps need to be performed only when the cluster is ready with all the required services and no encryption zone keys are present.
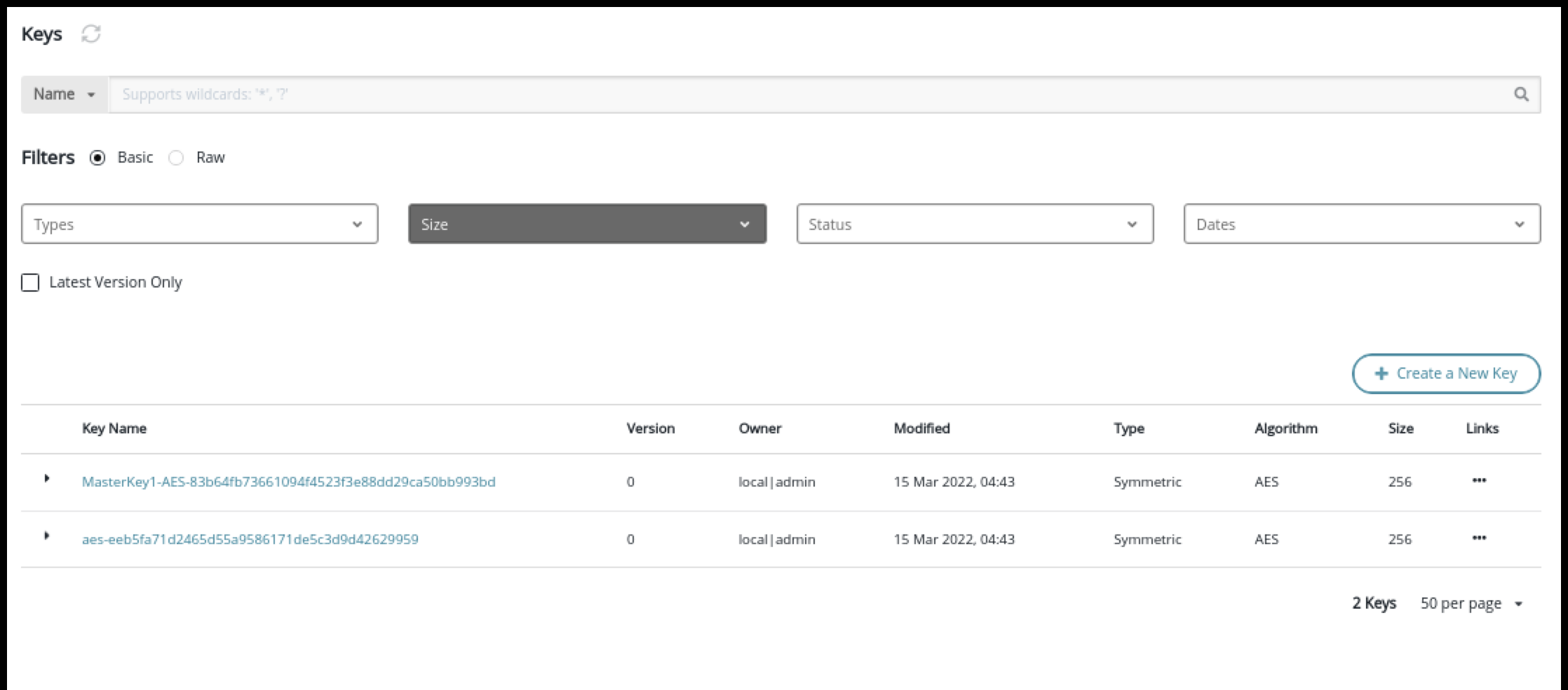
Migrating Ranger KMS DB Master Key To CipherTrust Manager HSM
How to migrate the Ranger KMS DB Master Key to CipherTrust Manager HSM. These steps need to be performed when the cluster is ready with all the required services and encryption zone keys are present in the Ranger KMS DB.
Migrating the Master key from CipherTrust Manger HSM to Ranger KMS DB
How to migrate the Master key from CipherTrust HSM to Ranger KMS DB. These steps need to be performed when the cluster is ready with all the required services and encryption zone keys are present in the Ranger KMS DB.