AWS quickstart (Deprecated)
If you've reached the Cloudera landing page for the first time, you've come to the right place! In this quickstart, we'll show you step-by-step how to connect Cloudera to your AWS account, so that you can begin to provision clusters and workloads.
- The Cloudera console pictured above
- The AWS console
The steps that we will perform are:
Step 0: Verify the AWS prerequisites
Step 1: Create a provisioning credential
Step 2: Register an AWS environment in Cloudera
Verify AWS cloud platform prerequisites
Before getting started with the AWS onboarding quickstart, review and acknowledge the following:
- This AWS onboarding quickstart is intended for simple Cloudera evaluation deployments only. It may not work for scenarios where AWS resources such as VPC, security group, storage accounts, and so on, are pre-created or AWS accounts have restrictions in place.
- Users running the AWS onboarding quickstart should have:
- AWS Administrator permissions on the AWS account that you would like to use for Cloudera.
- Rights to create AWS resources required by Cloudera. See list of AWS resources used by Cloudera.
- Cloudera Admin role or Power User role in Cloudera subscription.
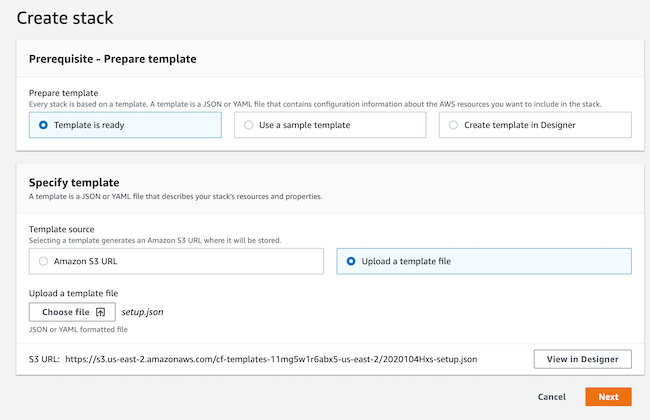
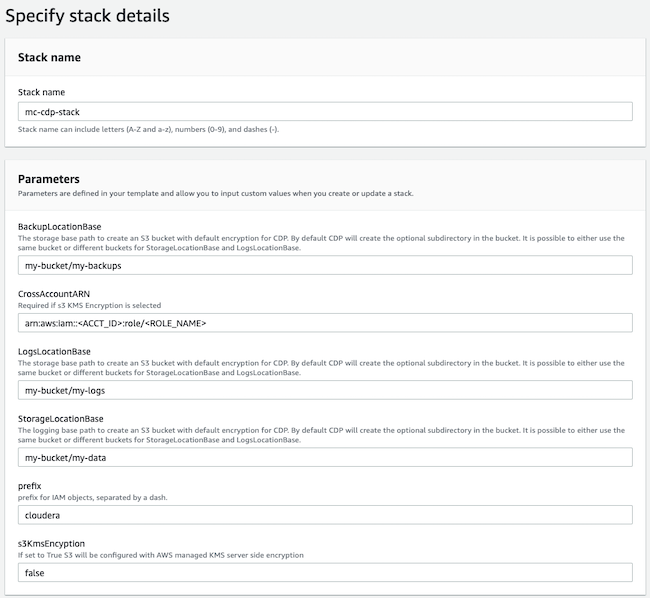
- This AWS onboarding quickstart uses a CloudFormation template that automatically creates the required resources such as buckets, IAM roles and policies, and so on.
- Cloudera on cloud relies on several AWS services that should be available and enabled in your region of choice. Verify if you have enough quota for each AWS service to set up Cloudera in your AWS account. See list of AWS resources used by Cloudera.
If you have more complex requirements than those listed here, contact Cloudera Sales Team to help you with the Cloudera onboarding.
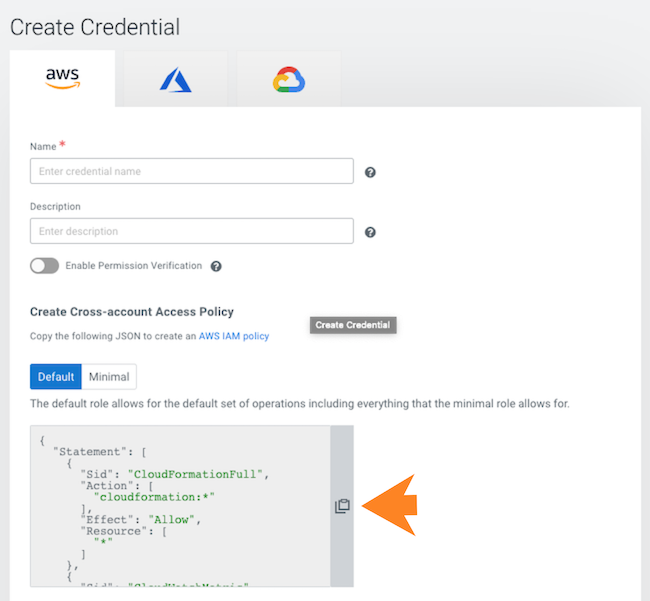
Create a Cloudera credential
In the Cloudera console, the first step is to create a Cloudera credential. The Cloudera credential is the mechanism that allows Cloudera to create resources inside of your cloud account.
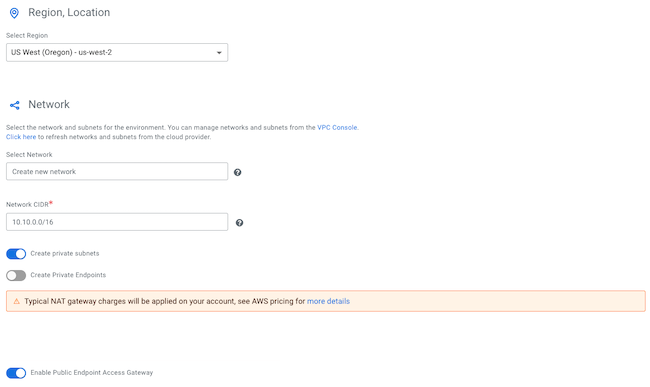
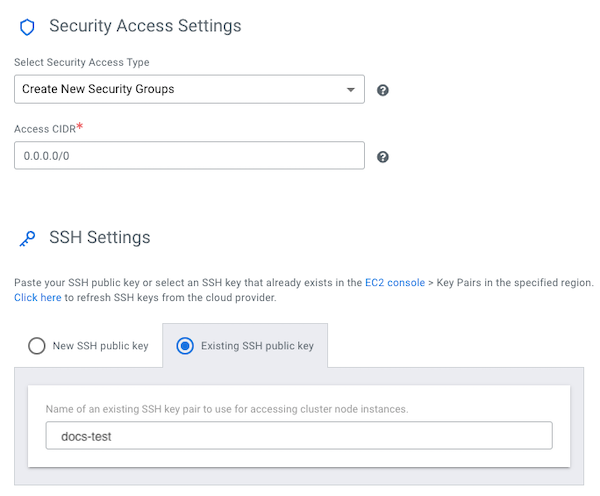
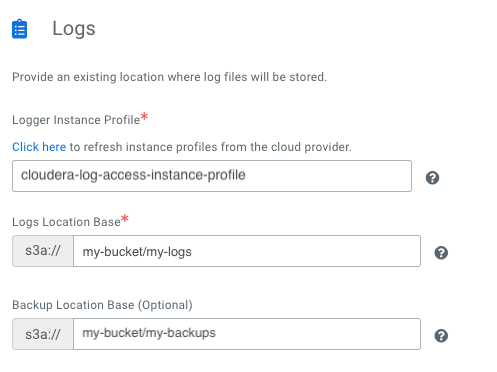
Register a Cloudera environment
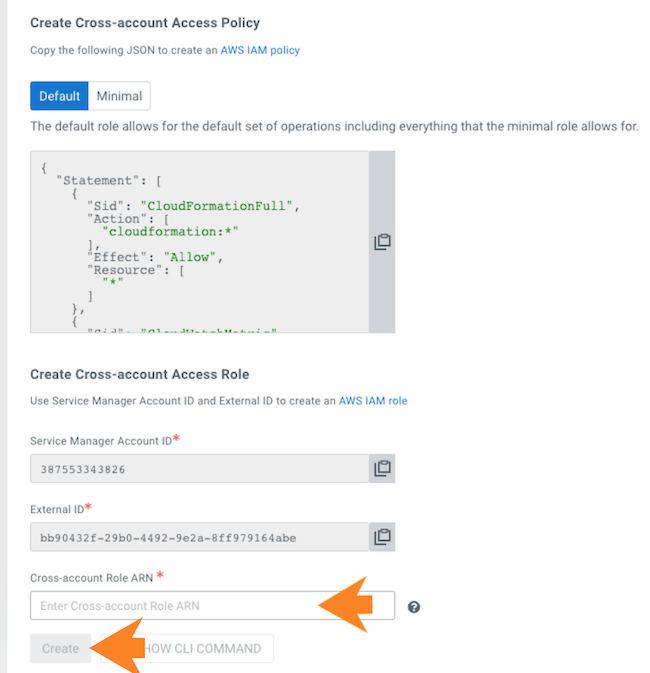
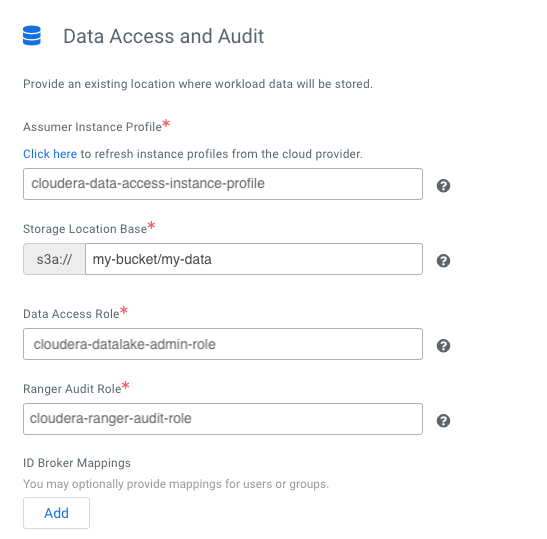
Before you register an environment, you'll want to create specific IAM roles and policies so that Cloudera can operate in a secure manner.