Cloudera Private Links Network for Azure
Cloudera Private Links Network enables you to connect privately and securely to the Cloudera Control Plane without traversing the internet. You can use Cloudera Private Links Network for end-to-end encryption of your workloads between Cloudera Control Plane and Azure private endpoints.
- High-level options of Virtual Network (VNet) endpoint placement
- Cloudera Private Links Network deployment process
- Instructions of how to set up both Private Link options:
- VNet: Setup of Cloudera Private Links Network for a workload VNet through CDP CLI
- Authorization: Authorization with CDP CLI to enable the setup of Cloudera Private Links Network through your automation tools
- References for proxy profile configuration and considerations, and Cloudera Private Links Network commands
Comparison of connectivity setup without and with Cloudera Private Links Network
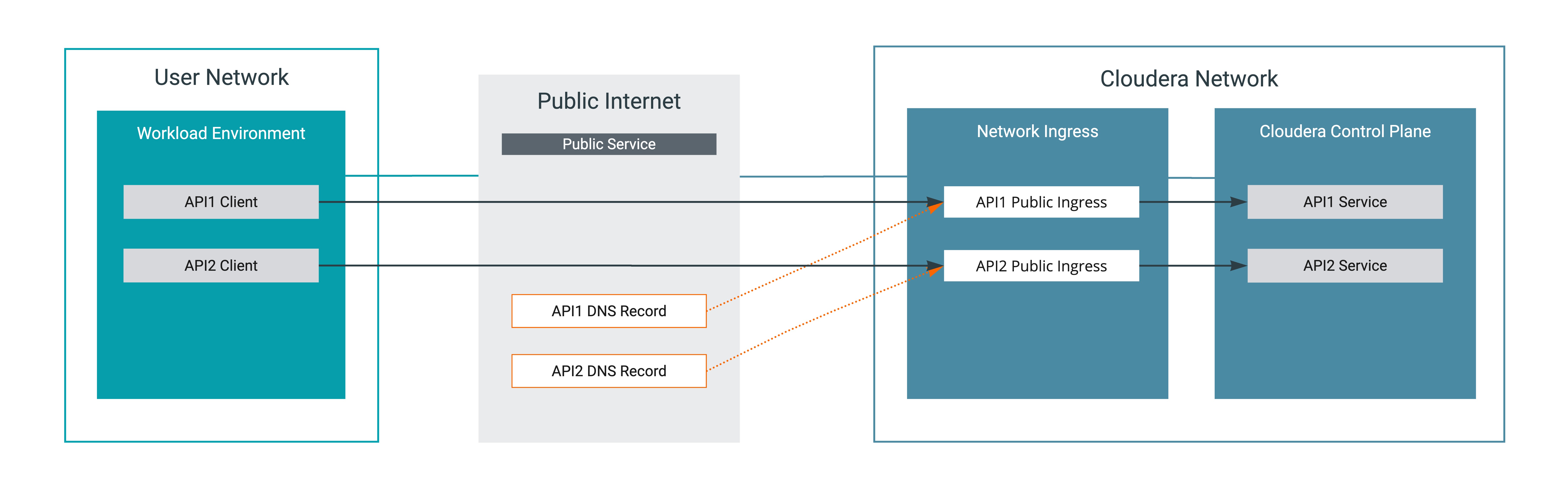
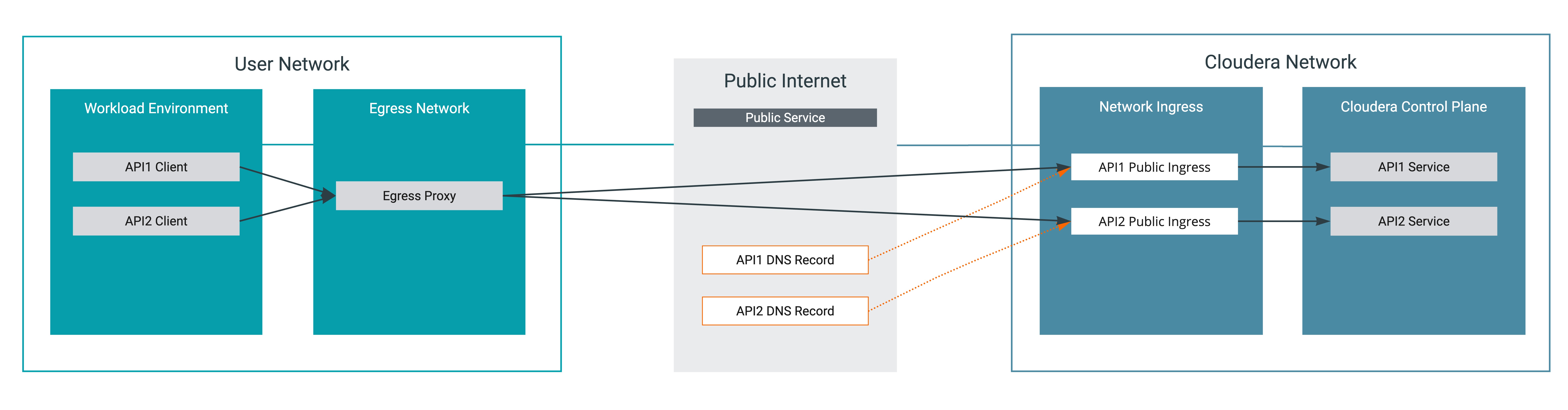
With Cloudera Private Links Network, the Cloudera Control Plane is accessed as if the Cloudera Control Plane would be on your network. This means that IP addresses are assigned to the Cloudera Control Plane services from your network, and DNS lookups will return your local IP addresses.
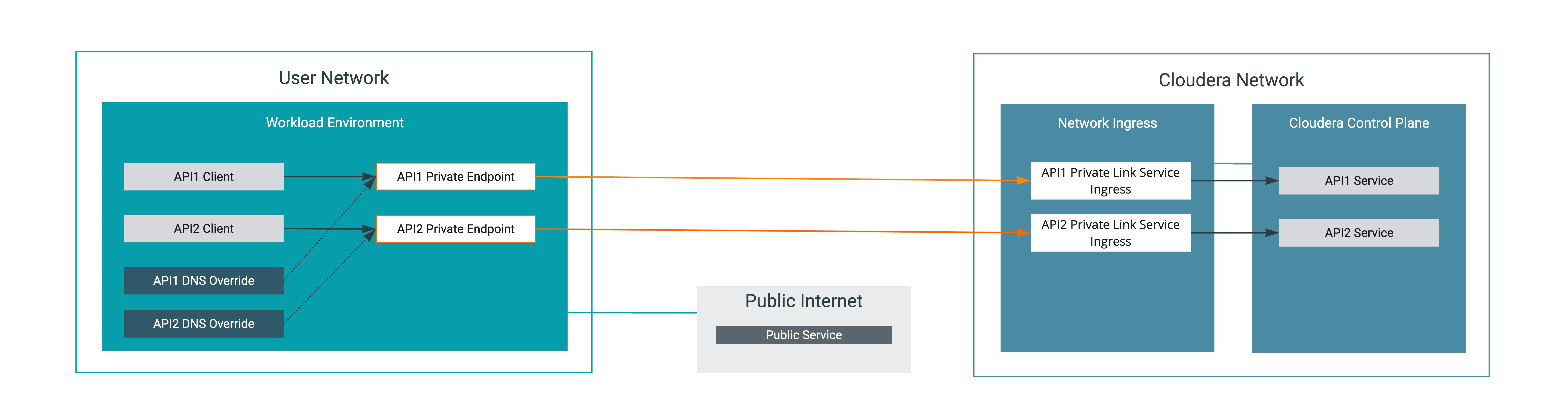
The following options are available for DNS overrides:
- DNS is a regional or global view: Installing overrides at a regional or global scope will impact DNS resolution for other VNets, these other VNets will attempt to use the local private endpoints of the VNet.
This section does not include an exhaustive list of design options, but should cover most cases. For more information about more advanced use cases, see the Additional VNet scenarios section.
