Azure quickstart (Deprecated)
If you've reached the Cloudera landing page for the first time, you've come to the right place! In this quickstart, we'll show you step-by-step how to connect Cloudera to your Azure subscription, so that you can begin to provision clusters and workloads.
- The Cloudera console pictured above
- The Azure console
- Azure Cloud shell
The steps that we will perform are:
Step 0: Verify the Azure prerequisites
Step 1: Create an Azure AD app
Step 2: Deploy the Azure quickstart template
Step 3: Assign roles
Step 4: Create or locate an SSH key
Step 5: Create a Cloudera credential
Step 6: Register a Cloudera environment
Verify Azure cloud platform prerequisites
Before getting started with the Azure onboarding quickstart, review and acknowledge the following:
- This Azure onboarding quickstart is intended for simple Cloudera evaluation deployments only. It may not work for scenarios where Azure resources such as VNet, security group, storage accounts, and so on, are pre-created or Azure accounts have restrictions in place.
- User running the Azure onboarding quickstart should have:
- Owner permissions on the Azure subscription that you would like to use for Cloudera.
- Rights to create Azure resources required by Cloudera. See list of Azure resources used by Cloudera.
- Rights to create an Azure AD application (service principal) and assign Contributor role at subscription level.
- Cloudera Admin role or Power User role in Cloudera subscription.
- This Azure onboarding quickstart uses an Azure ARM template that automatically creates the required resources such as storage accounts, containers, managed identities, resource groups, and so on.
- Cloudera on cloud relies on several Azure services that should be available and enabled in your region of choice. Verify if you have enough quota for each Azure service to set up Cloudera in your Azure account. See list of Azure resources used by Cloudera.
If you have more complex requirements than those listed here, contact Cloudera Sales Team to help you with Cloudera onboarding.
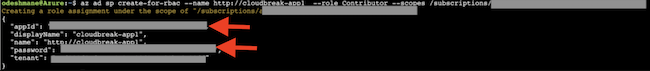
Create an Azure AD app
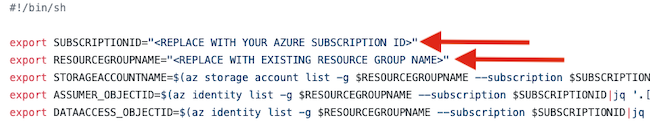
In the Azure portal, create an application in your Azure Active Directory tenant. This steps allows you to use the native Cloud Shell terminal and not have to set up Azure CLI.
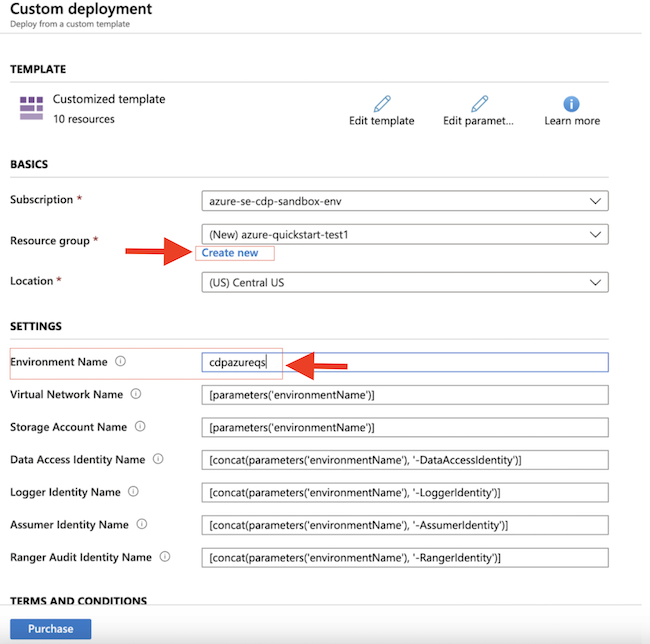
Deploy the Azure quickstart template
The Azure quickstart template is a customized ARM template that deploys essential Azure resources for the Cloudera environment.
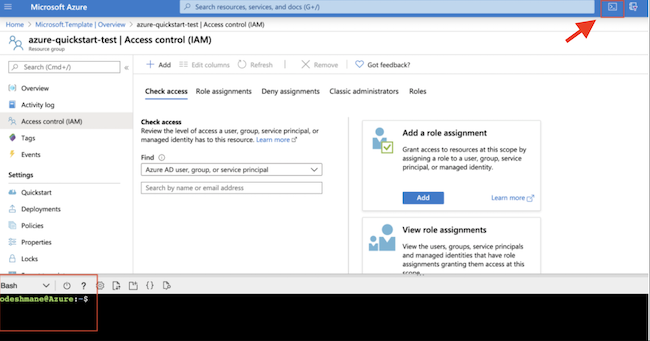
Assign roles
Azure Resource Manager templates do not support role assignments at a scope other than resource groups. Perform the following role assignments through UI or CLI.
Create or locate an SSH Key
Cloudera requires that you provide a public SSH key for admin access to VM instances.
You can find more information on SSH key requirement in the topic SSH key. If you need to create one, you can do
so by running ssh-keygen -t rsa.
When you complete this step, you have created all of the Azure resources required for this quickstart.
Create a Cloudera credential
In the Cloudera Console, the first step is to create a Cloudera credential. The Cloudera credential is the mechanism that allows Cloudera to create resources inside of your cloud account.
- Log in to the Cloudera web interface.
- From the Cloudera home screen, click the Cloudera Management Console icon.
- In the Cloudera Management Console, select Shared Resources > Credentials from the navigation pane.
- Click in the Create Credential button to create a new credential.
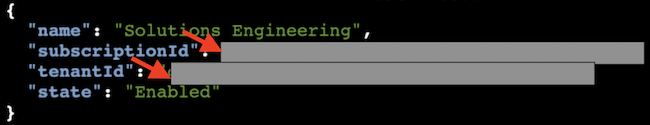
- Select the Azure tab, name your credential, under "Credential Type", select "App based", and enter the values you previously collected for subscription ID, app ID, and password.
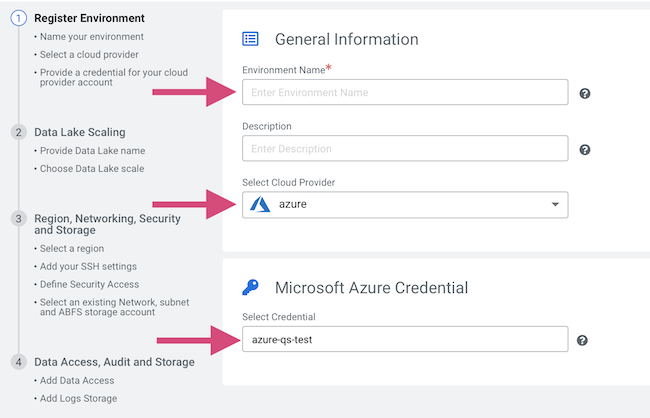
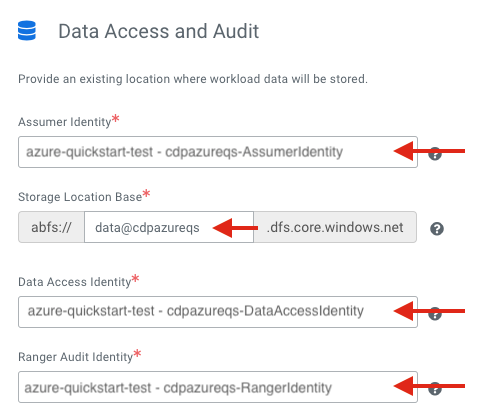
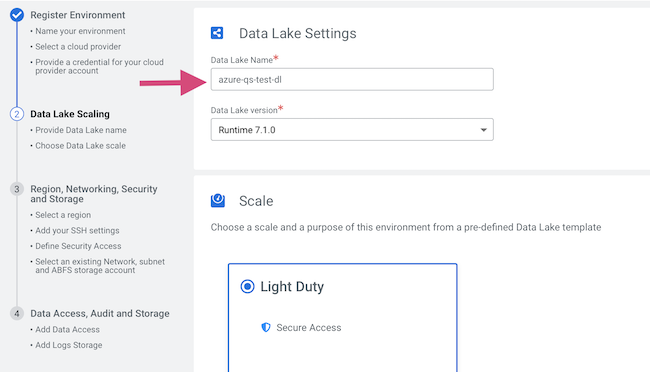
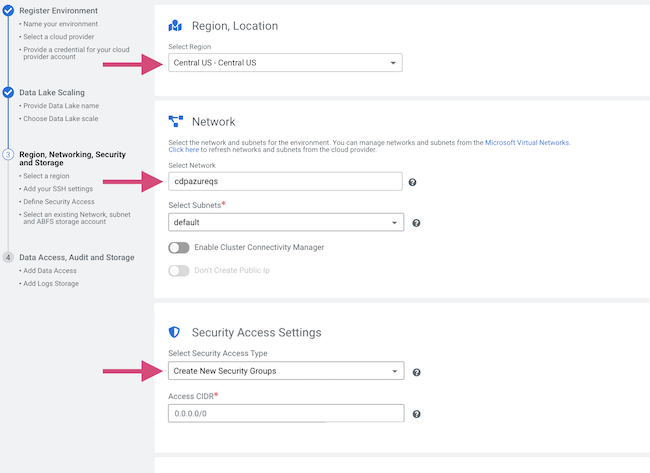
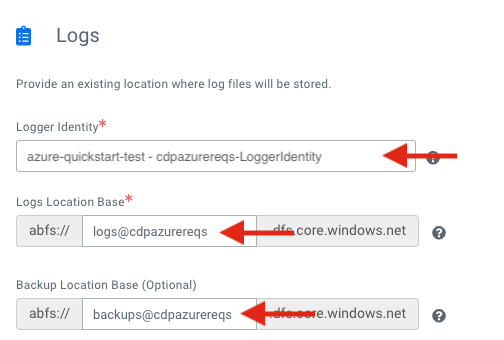
Register a Cloudera environment
When you register an environment, you set properties related to data lake scaling, networking, security, and storage. You will need your Azure environment name, resource group name, storage account name, and virtual network name from your resource group.