Renewing private/host certificates on Data Lake and Cloudera Data Hub clusters
Private (host) certificates have a default expiration date of one year; to keep the Data Lake and Data Hub clusters running, you must renew the host certificates before they expire.
Required role (Data Lakes): EnvironmentAdmin or Owner of the environment
Required role (Cloudera Data Hub): DatahubAdmin, Owner of the Cloudera Data Hub cluster, EnvironmentAdmin, or Owner of the environment
During cluster provisioning, Cloudera Manager creates an intermediate certificate (CMCA) signed by FreeIPA CA. The CMCA is used to create certificates for every host with Auto-TLS.There are two ways to renew a private/host certificate. To renew the private/host certificates at any time, use the following CLI commands:
Data Lake certificate renewal:
cdp datalake rotate-private-certificates --datalake <Data Lake name or CRN>Data Hub certificate renewal:
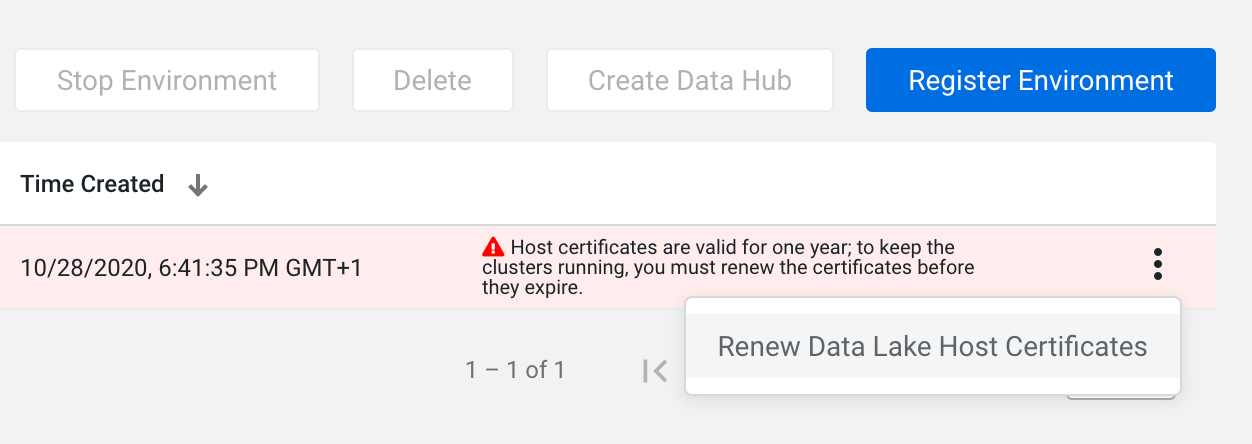
cdp datahub rotate-private-certificates --datahub <Data Hub name or CRN>Alternatively, you can wait until the host certificate is close to expiration. During periodic cluster state synchronization, Cloudera uses the Cloudera Manager API to check that the HOST_AGENT_CERTIFICATE_EXPIRY apiHealthCheck alert is in a GOOD state. If the apiHealthCheck is not in a GOOD state, Cloudera displays a warning in the UI.
These UI warnings will display on the associated environments, Data Lakes, or Cloudera Data Hub clusters list and details pages. For example:
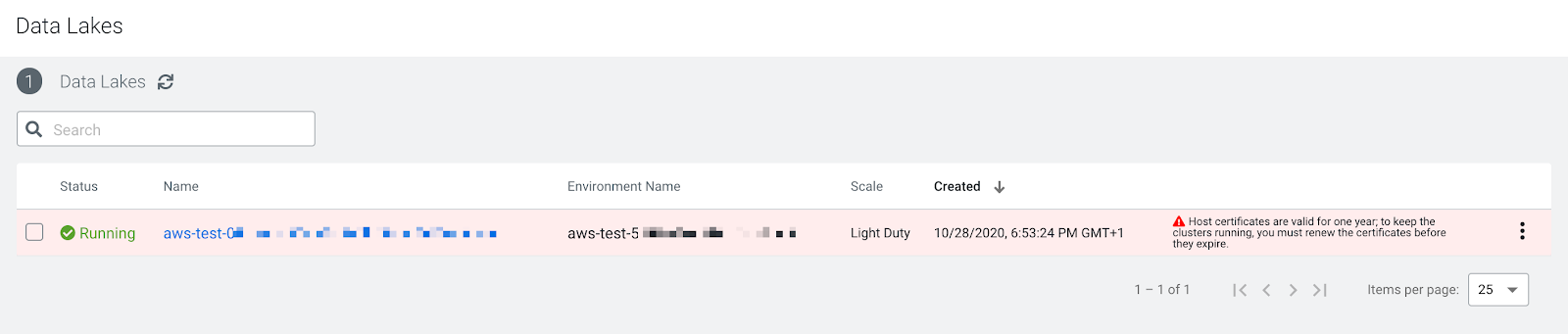
To renew the host certificate once you receive an expiration warning, follow the steps below.