Adding a customer managed encryption key for GCP
By default, a Google-managed encryption key is used to encrypt disks and Cloud SQL instances in Data Lake, FreeIPA, and Cloudera Data Hub clusters, but you can optionally configure Cloudera to use a customer-managed encryption key (CMEK) instead.
If you set a CMEK for your GCP environment, then the imported Compute Engine images will be encrypted with the CMEK instead of the default Google-managed key.
To set up a CMEK, you should:
- Meet the CMEK prerequisites.
- Register a GCP environment in Cloudera via Cloudera web UI or CDP CLI. During environment registration, specify the encryption key that you would like to use.
CMEK prerequisites
Refer to GCP Prerequisites: Customer managed encryption keys.
Create a Cloudera environment with a CMEK
You can pass the CMEK during GCP environment registration in Cloudera via Cloudera web interface or CDP CLI.
Steps
-
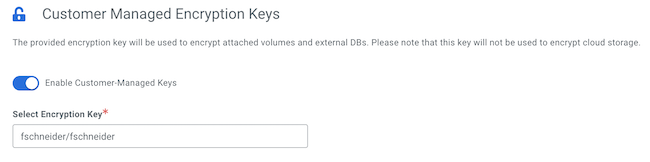
Under Customer-Managed Encryprion Keys, click Enable Customer-Managed Keys.
-
In the same section, select the CMEK:
The following screenshot shows the UI options:
--encryption-key parameter as shows in this example:
cdp environments create-gcp-environment \
--no-use-public-ip \
--environment-name <ENVIRONMENT_NAME> \
--credential-name <EXISTING_CREDENTIAL-NAME>\
--region <REGION>\
--security-access securityGroupIdForKnox=<SG_NAME1>,defaultSecurityGroupId=<SG_NAME2> \
--public-key <PUBLIC_SSH_KEY>\
--log-storage storageLocationBase=<LOGS_STORAGE_LOCATION> \
--existing-network-params networkName=<NETWORK>,subnetNames=<SUBNET>,sharedProjectId=<PROJECT_ID>\
--workload-analytics \
--encryption-key <PATH_TO_THE_ENCRYPTION_KEY>Next, create a Data Lake and IDBroker mappings using the usual commands. Once the environment is running, Cloudera Data Hub clusters can be created using the usual steps.
