Rotating database certificates when SSL enforcement is enabled
When SSL enforcement is enabled on your database server, do not perform the RDS certificate rotation directly using AWS tools, as this can lead to a service degradation or an outage of the respective resource. Use the options provided by Cloudera to perform the required RDS certificate rotation instead.
Required role (Data Lakes): EnvironmentAdmin
Required role (Cloudera Data Hub): DataHubAdmin or EnvironmentAdmin
If the following warning message is displayed on top of the Cloudera Management Console window, you must perform the TLS/SSL certificate rotation:
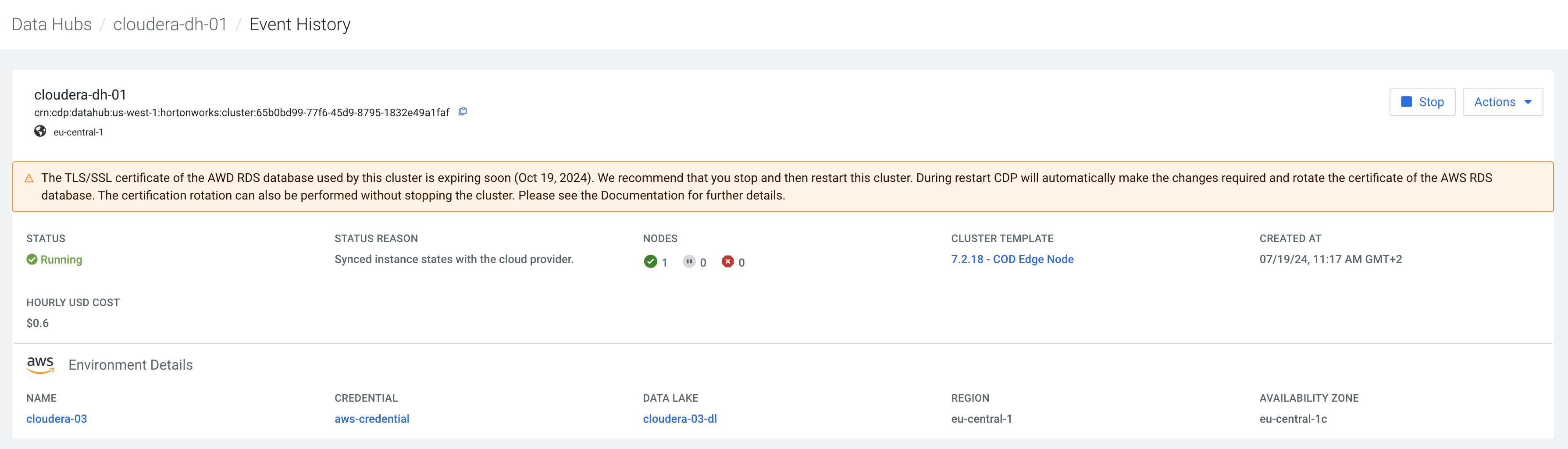
If you do not see the warning message, your clusters are not affected or the rotation has already been performed when you recently stopped and started your cluster or the environment.
Cloudera provides two options for rotating the expiring database certificates, with and without stopping your cluster:
Rotating the database certificate by stopping and starting your cluster
This is the default and most simple way to let Cloudera perform the certificate rotation and all changes required.
Instructions
- Stop all Cloudera Data Hub clusters where the warning about expiring database certificates is shown.
-
Stop and start your Data Lakes where the warning message is displayed.
Cloudera will automatically perform all Data Lake and AWS RDS changes required.
-
Start all Cloudera Data Hub clusters that you have previously stopped.
Cloudera will automatically perform all Cloudera Data Hub and AWS RDS changes required where the warning message is displayed.
You can perform the stop and start either via UI or CLI, see Stop a cluster.
Rotating the database certificate without stopping the cluster
Stopping the Data Lake or Cloudera Data Hub clusters is not feasible in some scenarios, as workloads need to be stopped and data stored on ephemeral disks or ephemeral cache is lost during cluster restart.
In certain cases, Cloudera allows the database certificate rotation to be performed without stopping your cluster. If your cluster supports this, you will see a Rotate Database Certificate button in the warning message.
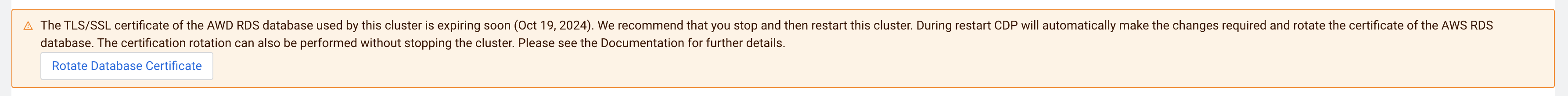
The Rotate Database Certificate button is only available if a rolling restart is supported on your cluster. For the list of supported versions, see the Data Lake rolling upgrades and the Cloudera Data Hub rolling upgrades documentations.
Under some circumstances, a rolling certificate rotation may not be supported for a Data Lake or Cloudera Data Hub cluster, but can be enabled through entitlement. For information about obtaining this entitlement, contact Cloudera Customer Support.
Instructions
To perform a rolling restart, click the Rotate Database Certificate button on top of the screen, inside the warning message.
You can also use the following CLI commands to perform the certificate rotation with minimal downtime and without stopping the cluster. The same roles are required as for the Rotate Database Certificate action through the UI.
- Use the following command to rotate the certificate for each Cloudera Data Hub
cluster.
cdp datahub rotate-db-certificate --datahubName <VALUE CAN BE cluster CRN or name> - Use the following command to rotate the certificate for the Data
Lake.
cdp datalake rotate-db-certificate --datalakeName <VALUE CAN BE cluster CRN or name>
Overriding default root certificate
rds-ca-rsa2048-g1, which is valid for 40 yearsrds-ca-rsa4096-g1, which is valid for 100 yearsrds-ca-ecc384-g1, which is valid for 100 years
rds-ca-rsa2048-g1 is the root certificate in all supported
regions that is picked as a target certificate during the certificate rotation. You have the
option to override the default certificate, and set one of the certificates available in your
region as a target root certificate that will be picked during the certificate rotation.
Overriding the default root certificate is not tied to any particular RDS instance, but
applicable to the whole AWS region in the target AWS account.aws --region [*** REGION ***] rds describe-certificatesaws --region [*** REGION ***] rds modify-certificates --certificate-identifier [*** ROOT CERTIFICATE ***]rds-ca-rsa2048-g1
certificaate in the us-west-1 to
rds-ca-ecc384-g1:aws --region us-west-1 rds modify-certificates --certificate-identifier rds-ca-ecc384-g1