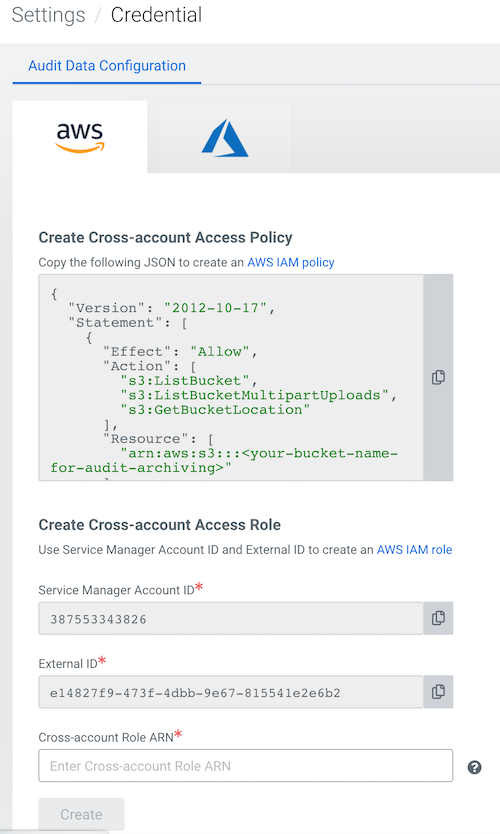
To configure archiving, you must create an AWS IAM role specifically for audit event
archiving. Then create an audit credential using the cross-account role ARN.
In AWS, create a new S3 bucket or designate an existing bucket
for audit archiving. Be sure to block all public access. The audit logs are written to the S3
bucket even without public access as the writing process is based on the AWS role and not on
the internet access.Audit events will be archived under the /cdp/cp folder,
which will be created automatically by Cloudera.Required
Role:
PowerUser
-
Log in to the Cloudera interface.
-
In the left-side navigation menu, click and
then click Create.
-
Select the AWS icon.
- Copy the cross-account access policy provided to you in the Create
Cross-account Access Policy field, substituting your bucket name where
indicated.
-
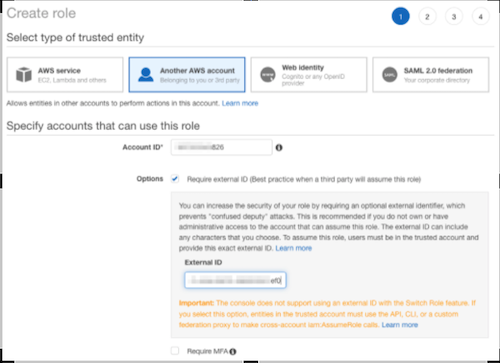
From the AWS account hosting the bucket, create an IAM role for another AWS account, in
this case, for the account running the Cloudera Control Plane.
Include the policy that you copied as the only one in the role.
For detailed
instructions on creating an AWS IAM cross-account role, see Create a cross-account IAM role, starting with
"1. Log into the AWS Management Console." Although the audit event archiving credential
requires a unique policy and cross-account Role ARN, the process is largely the same as
creating a role-based credential during environment registration.
-
When you finish creating the new cross-account policy and role in AWS, copy the Role
ARN from the Role Summary page in the AWS Management Console and
return to Cloudera. Paste the Role ARN into the
Cross-account role ARN field.
- Click Create.
- Configure the audit data location with the name of the S3 bucket that you
designated as the audit archive bucket.
- Select the AWS region where storage services should be accessed.
- Use the toggle button to enable or disable audit log export to the configured
storage location.
- Click Save.
Audit event archiving configuration is complete.