Granting remote access to Kubernetes clusters on Azure Kubernetes Service
You can remotely access Azure Kubernetes Service (AKS) clusters for troubleshooting, log collection, and maintenance purposes using SSH. To do that, you must add the Azure Active Directory (AD) object ID in the Cloudera Data Warehouse environment Kubeconfig.
Required Role: DWAdmin
- You must have an active Cloudera Data Warehouse environment to grant your users remote access to the Kubernetes cluster.
- Contact your Azure account administrator to obtain the Azure AD object ID.
Obtaining the Azure AD object ID using Azure CLI
You can obtain the object ID by running the following
command:
az ad group list --filter "displayname eq '[***GROUP-NAME***]'" -o tableThis lists all the existing groups within the directory.
Obtaining the Azure AD object ID from the Azure portal
- Sign in to the Azure portal using a Global administrator account for the directory.
- Search for and select Azure Active Directory.
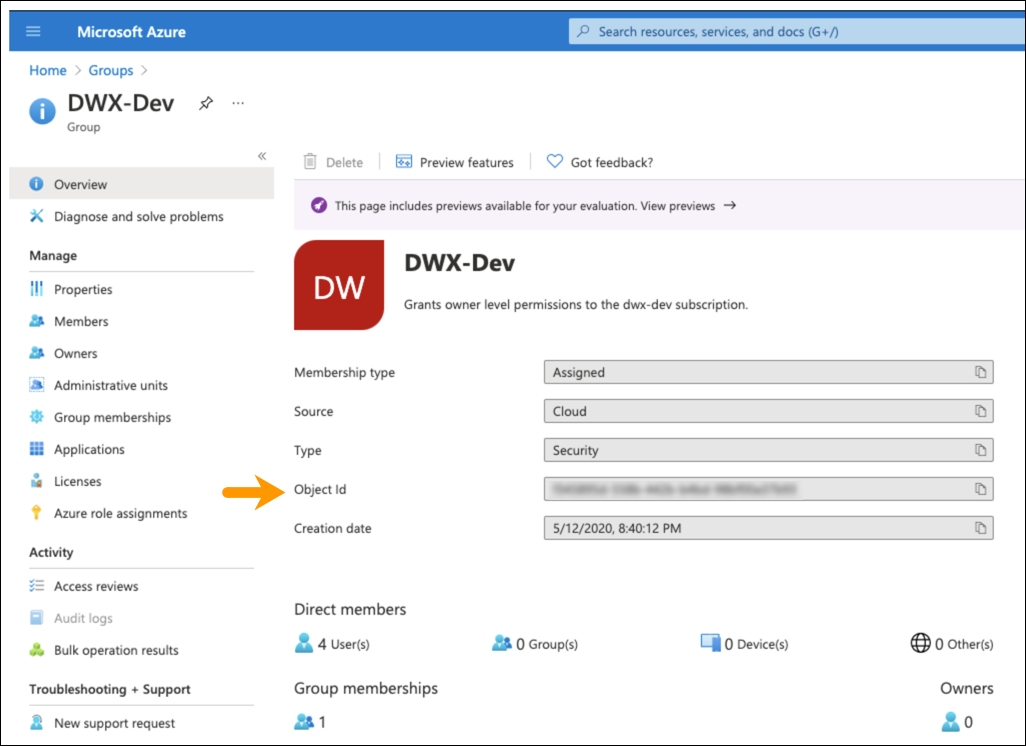
- On the Active Directory page, select Groups and click Overview.
- Note the Object ID from the Group
Overview page.
- In the Cloudera Data Warehouse service, go to the Environments tab.
- Locate the environment for which you want to grant access to AKS and click .
- Enter the Azure AD object ID in the Add new group text box.
- Click Grant Access to save your changes.
kubectl get pods Azure CLI, you
see the
following
message:To sign in, use a web browser to open the page https://microsoft.com/devicelogin and enter the code ****** to authenticate.
- Open a web browser and go to https://microsoft.com/devicelogin.
- Enter the code on the Enter code page and click Next.
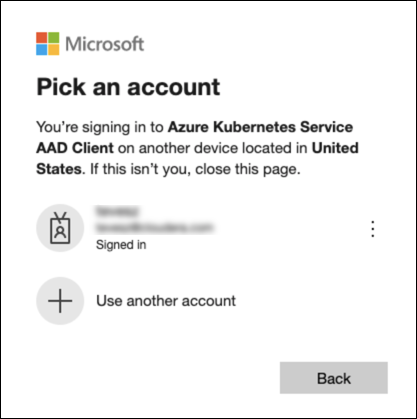
- On the Pick an account page, select the account for signing
into the AKS AAD Client.
Upon successful login, you get the following message:
