Define a new default KMS key for Cloudera environment level EBS encryption
When you define a custom KMS key at the Cloudera environment level, you need to add policies to your key definition that allow for storage provisioning and fulfilling scaling requests.
-
Create a custom encryption key on the AWS Management
Console.
The key policy section of the new key must contain additional permissions. Add the three required permission blocks in the example below.Replace [***YOUR ACCOUNT ID***] and [***YOUR ACCOUNT REGION***] with your AWS account ID and with the AWS region where you want to deploy Cloudera Data Flow, respectively.
{ "Sid": "AllowAutoscalingServiceLinkedRoleForAttachmentOfPersistentResources", "Effect": "Allow", "Principal": { "AWS": "arn:aws:iam::[***YOUR ACCOUNT ID***]:role/aws-service-role/autoscaling.amazonaws.com/AWSServiceRoleForAutoScaling" }, "Action": "kms:CreateGrant", "Resource": "*", "Condition": { "Bool": { "kms:GrantIsForAWSResource": "true" } } }, { "Sid": "AllowAutoscalingServiceLinkedRoleUseOfTheCMK", "Effect": "Allow", "Principal": { "AWS": "arn:aws:iam::[***YOUR ACCOUNT ID***]:role/aws-service-role/autoscaling.amazonaws.com/AWSServiceRoleForAutoScaling" }, "Action": [ "kms:Encrypt", "kms:Decrypt", "kms:ReEncrypt*", "kms:GenerateDataKey*", "kms:DescribeKey" ], "Resource": "*" }, { "Sid": "Allow EKS access to EBS.", "Effect": "Allow", "Principal": { "AWS": "*" }, "Action": [ "kms:CreateGrant", "kms:Encrypt", "kms:Decrypt", "kms:ReEncrypt*", "kms:GenerateDataKey*", "kms:DescribeKey" ], "Resource": "*", "Condition": { "StringEquals": { "kms:CallerAccount": "[***YOUR ACCOUNT ID***]", "kms:viaService": "ec2.[***YOUR ACCOUNT REGION***].amazonaws.com" } } } -
When registering your Cloudera environment,
follow these steps on the Region, Networking and Security
page to assign the custom key:
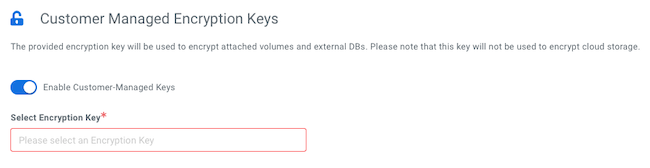
-
Under Customer-Managed Keys, click Enable Customer-Managed Keys.
-
Select the CMK you want to enable for this environment from the Select Encryption Key drop-down list.
-
- If you are also using restricted IAM policies with Cloudera, make sure you provide the KMS CMK for volume encryption when you Create the restricted policies and attach them to the cross-account role .
