Roles
Cloudera Data Visualization provides URL access to the Cloudera Data Visualization server object called roles.
To support installations that store the users and
groups information outside the Cloudera Data Visualization environment (such as LDAP), the role
membership lists for users and groups only
store names. During role update and create operations, Cloudera Data Visualization accepts user and group names 'as is',
without validating them.
Each entry in the privs list corresponds to a single privilege
row on the Cloudera Data Visualization role edit page. Each row
contains fields for the privilege type (ptype), an
identifier section, and a list of permissions (perms) for
the identified objects, such as datasets or data connections. Each privilege
type has a specific identifier, and set of possible permissions. Cloudera Data Visualization stores the dataset IDs and connection
IDs within the identifier sections as a STRING and uses the
special value -1 to indicate 'All dataset' or 'All
connections.
Roles data type
The JSON fields for the roles' data type are defined as follows:
| Field | Detail Only | Updatable | Description |
|---|---|---|---|
id |
No | No | Role ID |
name |
No | Yes | Role name |
desc |
No | Yes | Role description |
users |
No | Yes | List of usernames that belong to this role |
groups |
No | Yes | List of groups that belong to this role |
privs |
Yes | Yes | List of privilege structures for this role, as described in Privileges types |
Privileges types
The Cloudera Data Visualization Role-Based Access Control system supports the following permission types:
- ptype: "system"
- Identifier
- None
- Permissions
Permission name Description sys_editpermManage roles and users sys_stylesManage styles and settings sys_viewlogsView query logs sys_editconnManage data connections
- ptype: "dataconn"
- Identifier
-
Field name Description Example dclistList of data connection IDs, or -1for 'All data connections'"dclist" : ["-1"] - Permissions
-
Permission name Description dc_aviewsManage analytical views dc_uploadImport data dc_exporeCreate datasets and explore tables
- ptype: "dataset"
- Identifier
-
Field name Description Example dcidData connection ID for this privilege, or -1for 'All'"dcid" : "-1"dslistList of dataset IDs for this privilege "dslist" : ["1", "2", "3"] - Permissions
Permission name Description dc_aviewsManage analytical views dc_uploadImport data dc_exporeCreate datasets and explore tables
Creating roles
The following code creates a new role with groups
dataconn_managers and
arcviz_admins. The role has system-level
permissions to view logs, and to create new datasets. It also has
full permissions on all connections and all datasets.
The actual API Key and the method of retrieving the key depends on the user system.
curl -s \
-X POST \
-H "Content-Type: application/x-www-form-urlencoded" \
-H "Authorization: apikey api_key" \
-d 'data=[{
"name": "Connection manager",
"desc": "Data connection management",
"groups": ["dataconn_managers", "arcviz_admins"],
"privs": [
{"ptype": "system",
"perms": ["sys_viewlogs", "sys_editconn"]
},
{"ptype": "dataconn",
"dclist": ["-1"],
"perms": ["dc_aviews", "dc_upload", "dc_explore"]
},
{"ptype": "dataset",
"dcid": "-1",
"dslist": ["-1"],
"perms": ["ds_manage", "ds_appedit", "ds_appview"]
}
]
}]' \
127.0.0.1:7999/arc/adminapi/roles
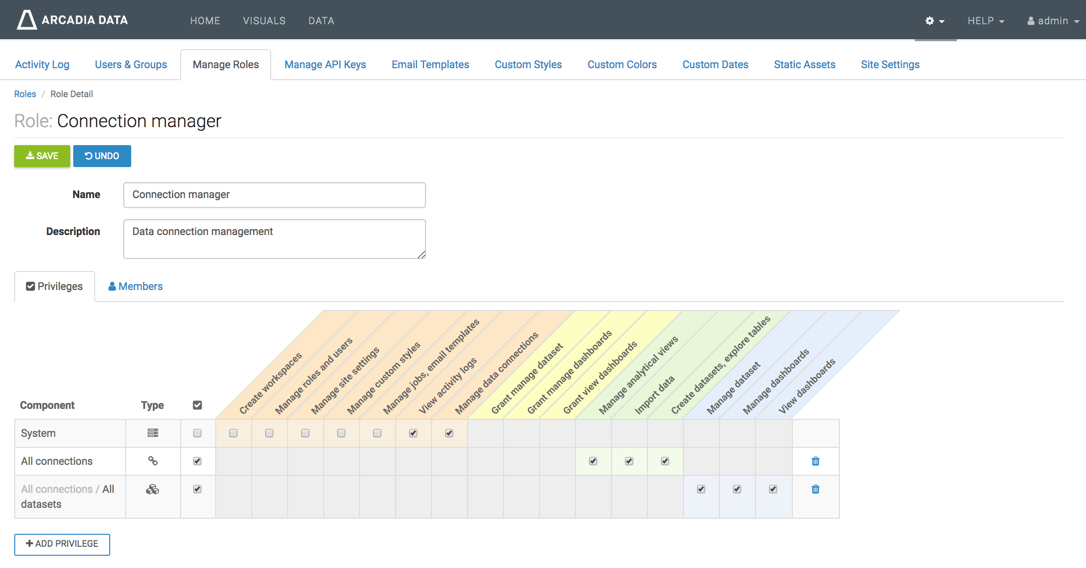
When viewing this role through the Cloudera Data Visualization user interface, it appears on the edit page like this: